From spams to botnets
At Emsisoft Labs we are always on the lookout for something out of the ordinary happening, and we recently came across a circulation of spam portraying as fake FedEx Emails. Emsisoft AntiMalware will detect and remove the same as Trojan-Dropper.Win32.Oficla (alias Sasfis).
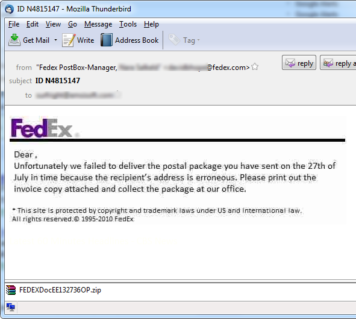
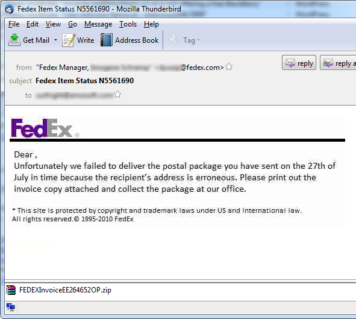
The email comes with subjects like “ID N4815147” or “FedEx Item Status N5561690” and does not contain any text but image. More and more spams recently are using this tactics to prevent being blocked by mail servers/gateway spam blockers.
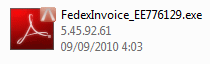
The attachment comes in zipped format and spoofs the executable as a PDF format.
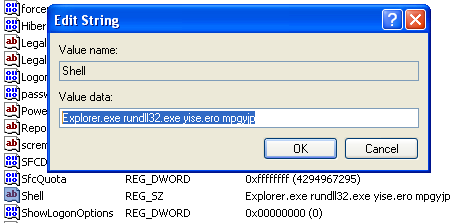
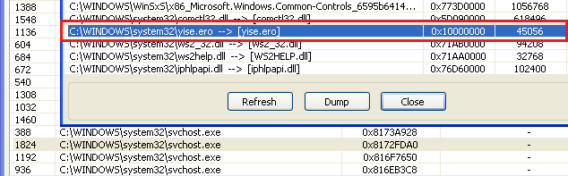
Once executed, the dropper drops a DLL under System32yise.ero which overwrites the shell entry in the registry.
The module yise.ero on decryption exposed the payload and we could confirm the same on the following events.
When the system restarts, the malware automatically executes itself and injects yise.ero module to svchost.exe process. The malware calls “mpgyjp” which is an export function of the DLL.
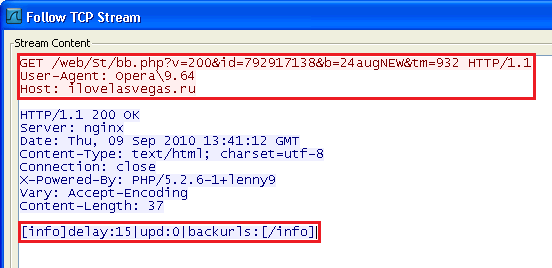
Carrying out the process and initiation of a botnet in the system, a HTTP GET request is sent to the server or C&C, which in this case is: ilovelasvegas.ru (109.196.134.44). The GET result contains command for the bot to download and execute another file.