Warning: Surprise spam trojan on Facebook
Ever received messages from your Facebook friends containing a notice or invitation, such as an invitation to visit a particular site, added with an interesting message, like “Hey watch this, so cool!”? In most cases, the recipient of the message will be happy to follow it, especially if the message was sent by one of your best friends, which you trust. However, did you ever think that it could be sent by an intruder, spam, or even viruses?
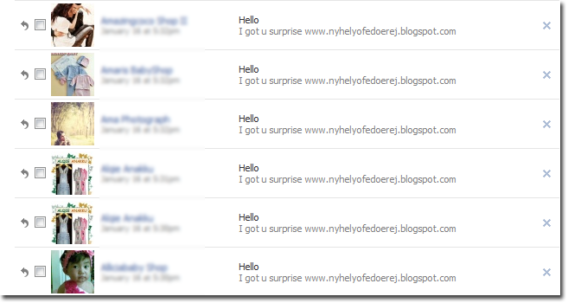
Like yesterday, one of my friends received a “surprise” from Facebook, but then soon realized that his computer was now infected with the trojan, as well as making it a “spam machine.”
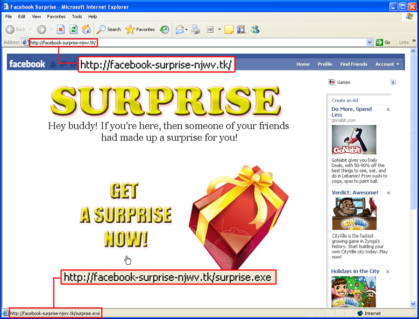
As you can see, the site was not the original of Facebook, but “hxxp://facebook-surprise-kjeg.tk/”. Through social engineering techniques, the author deliberately makes the site look like the original one, of course, to give users a false sense of security.
And when the mouse is hovering at that page, it would seem that it is a link that leads to the file “suprise.exe” (hxxp://facebook-surprise-kjeg.tk/surprise.exe). The file itself is using an icon that similar to the default icon of image file:
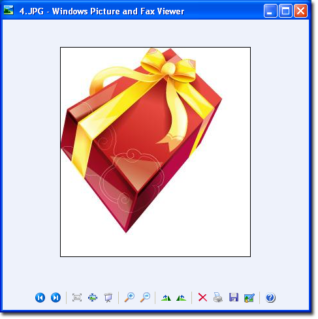
Once the user runs the file, it will only display a “gift” image like this:
But, without realizing it, a Trojan infecting the computers in the background.
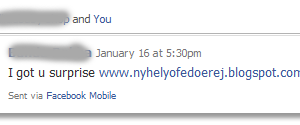
Apparently, it all comes from a message that he received on his Facebook account. The messages look like this: “I got u surprise www.nyhelyofedoerej.blogspot.com.”
When the link is clicked it will lead to an account on Blogspot, and then it is redirected again to hxxp://facebook-surprise-kjeg.tk/.
Once the file “surprise.exe” is executed, it will then monitor all user activity, by injecting itself to the active browser, such as Internet Explorer or Mozilla Firefox. If the user tries to login into his Facebook account, the malware will record the username and password, to be used to spamming to every friend on the Facebook account. Users can find out by looking at the folder “sent”.
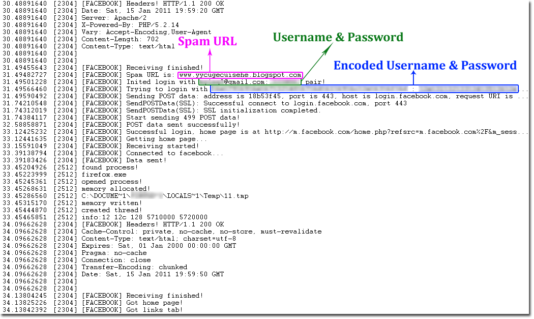
Interestingly, the author tells us what he was doing behind the scenes (or he forgot to remove the debug string?). These messages will appear when we run the debugger, or DebugView to monitor debug output. We obtain the following log when the malware is trying to login into the facebook account:
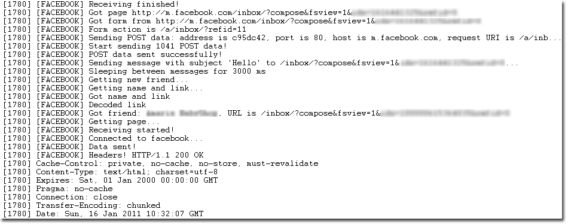
And the following when the trojan did spam to all friends in the Facebook account:
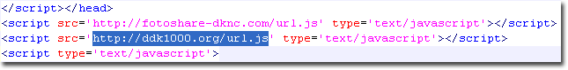
Before doing spam, it performs the GET request to address “ddk1000.org/ab/setup.php?act=fb_get” to obtain data used for spam, such as subject, message body, and the malicious url that is used for spam. The data is a string like this:
<data>3000|140000|Hello|I got u surprise |My Dear Friend u should look for |I have surprise for u
[www.ebyqerapinylyrato.blogspot.com|www.udenaqylinabig.blogspot.com|www.kuopyqupisee.blogspot.com|
www.sebafelumunynuly.blogspot.com|www.sypupolufoigirisyc.blogspot.com|www.ogyohanofaeqis.blogspot.com|
www.juyeliadileqaq.blogspot.com|www.gyseuodysecu.blogspot.com|www.pucoriiukiylyfo.blogspot.com|
www.yycugecuisehe.blogspot.com|www.nyhelyofedoerej.blogspot.com|www.teejoubiimanuh.blogspot.com|
www.timeteobyqufousy.blogspot.com|www.ooapetyuqatoda.blogspot.com|www.okojylimukikap.blogspot.com|
www.milurudutyfebusab.blogspot.com]</data>
Following is the malicious site that we get from the data above (please don’t visit, some link are still active):
- hxxp://ebyqerapinylyrato.blogspot.com
- hxxp://udenaqylinabig.blogspot.com
- hxxp://kuopyqupisee.blogspot.com
- hxxp://sebafelumunynuly.blogspot.com
- hxxp://sypupolufoigirisyc.blogspot.com
- hxxp://ogyohanofaeqis.blogspot.com
- hxxp://juyeliadileqaq.blogspot.com
- hxxp://gyseuodysecu.blogspot.com
- hxxp://pucoriiukiylyfo.blogspot.com
- hxxp://yycugecuisehe.blogspot.com
- hxxp://nyhelyofedoerej.blogspot.com
- hxxp://teejoubiimanuh.blogspot.com
- hxxp://timeteobyqufousy.blogspot.com
- hxxp://ooapetyuqatoda.blogspot.com
- hxxp://okojylimukikap.blogspot.com
- hxxp://milurudutyfebusab.blogspot.com
Emsisoft detects this malware as Trojan-Downloader.Win32.FraudLoad!IK.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialAlways stay alert and be cautious with everything you receive.