LINKEDIN – connecting to… ZeuS?
Below you can see the email as we received it. It looks harmless enough and appears to be sent to us from a genuine LinkedIn email address.
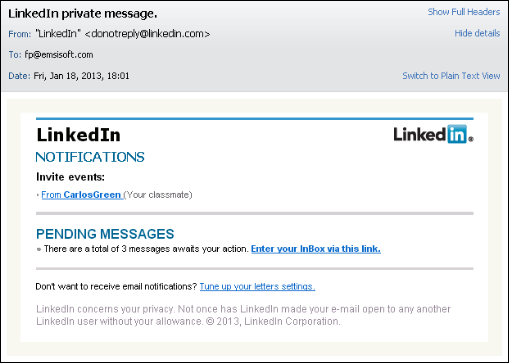 The message looks pretty authentic, but as it happens “Carlos Green” doesn’t sound familiar. A simple right click and copy of the hyperlink reveals the actual URL address:
The message looks pretty authentic, but as it happens “Carlos Green” doesn’t sound familiar. A simple right click and copy of the hyperlink reveals the actual URL address:
hxxp://cdn-iix.static.unkn0wn.or.id/linkfrrequest.html
Which in turn redirects us to:
hxxp://shininghill.net/detects/solved-surely-considerable.php
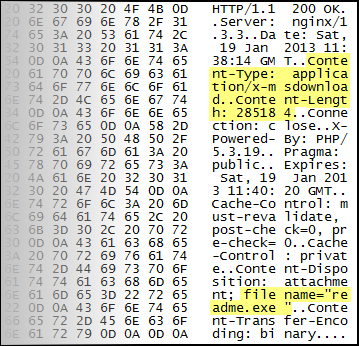
Analysis of this URL reveals that it exploits a vulnerable Java version (7 update 10 or older) in order to install the well-known ZeuS banking trojan. The image below illustrates how an executable with a size of 285184 bytes, named “readme.exe” is retrieved from the remote server. A quick check of the binary data reveals that this is the same file as the ZeuS executable that will end up infecting the system.
After the malicious code is loaded the browser will redirect to the normal LinkedIn website. The installed malware is detected by Emsisoft products as Trojan.Win32.Zbot.
When testing the malicious URL on the same system with the latest Java update (7 update 11) installed, the site will still make an attempt to infect the computer but will not succeed in requesting and retrieving the readme.exe file. In the end no malware is installed.
More information about this Java vulnerability can be found in the Oracle Security Alert for CVE-2013-0442.
Java exploits are among the most common sources of infection. Many computer users have Java installed but do not keep it up to date. This makes it a profitable business for malware-writers and-distributors to look for (new) vulnerabilities and exploit them. New exploit kits are sold for thousands of dollars.
If you have become the victim of this exploit and need help cleaning your computer, our experts in the “Help, my PC is infected!” Emsisoft Forum are always ready and willing to offer additional help. The removal service is free even if you are not an Emsisoft customer yet.
To prevent infection in the first place, make sure you:
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free Trial- Keep Java and other commonly exploited software (e.g. Adobe Reader and Flash player), as well as your Windows installation up to date.
- Use an Antivirus solution with a good behavior blocker, such as Emsisoft Anti-Malware. Traditional signature-based detection alone is ineffective against this type of malware.