Ransomware – The no. 1 threat for 2013
 “Your computer is blocked!” – Not something you enjoy seeing when using it. Unfortunately thousands of PC users worldwide find themselves in a situation where, all of a sudden their computer is unusable unless they pay a fee to unlock it. The FBI or a similar national law enforcement organization seems to claim that access to the computer has been restricted. The usage of pirated software, distribution of child porn and copyright infringements are most often brought up as grounds for these restrictions. “Seems” is the keyword here, because a malware infection, not an official law enforcement organization, is responsible.
“Your computer is blocked!” – Not something you enjoy seeing when using it. Unfortunately thousands of PC users worldwide find themselves in a situation where, all of a sudden their computer is unusable unless they pay a fee to unlock it. The FBI or a similar national law enforcement organization seems to claim that access to the computer has been restricted. The usage of pirated software, distribution of child porn and copyright infringements are most often brought up as grounds for these restrictions. “Seems” is the keyword here, because a malware infection, not an official law enforcement organization, is responsible.
While the idea of scaring a user into paying money to regain the use of their computer isn’t new and has been used for years by rogue security programs, the “scare” factor is much greater with so-called ransomware because in many cases the PC cannot be used at all, with the only active option remaining, being the entry of the unlock/payment code.
The last months have shown a massive increase in ransomware infections with new variants, droppers and infection methods each day. We have previously discussed ransomware in 2011 – The Renaissance of Ransomware, but because the risk of catching such an infection has increased so much we want to afford it extra attention to make computer users aware and point out preventive measures.
There are two main categories of ransomware, the so-called screenlockers and crypto ransomware. Screenlockers are wide-spread; they use exploit kits, infected sites and downloads and target home users as well as corporate computer users. Crypto ransomware often (but not exclusively) spreads through dedicated server hacks and home users will not be affected as much by this category of ransomware.
Screenlockers
Screenlocker ransomware can infect a computer in a variety of ways. Popular methods include the use of Java exploits as many Windows users have outdated versions of Java installed, which contain certain vulnerabilities that can be exploited by malware to infect a system. And of course porn sites with videos or other site content that when executed/activated actually installs malware.
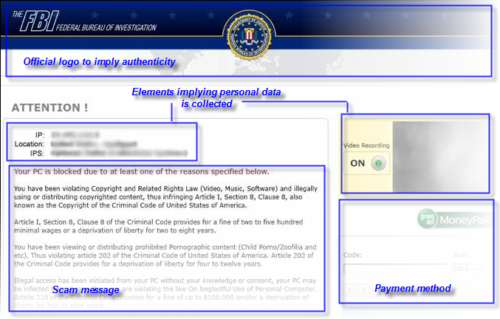
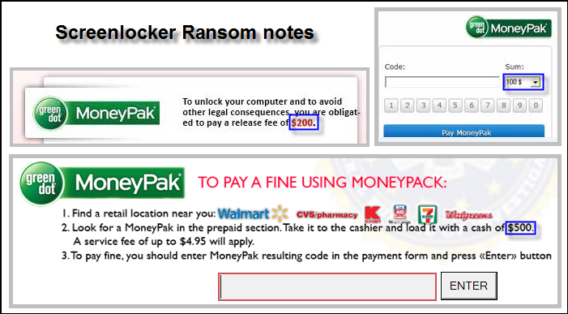
A typical screenlocker will usually display a law-enforcement logo. Which logo that is depends on the screenlocker variant, but can also depend on country. Furthermore an offense is specified; as mentioned already, this often concerns copyright infringement, child porn distribution, software pirating and similar. Next of course is the most important thing – the payment method. Sometimes a specific unlock code is required, but in most cases a prepaid payment method like Ukash or PaySafe is used.
Some screenlockers add extra elements, for example to give the impression that webcam capture is activated or geographical data is being collected, by displaying the IP address and location (see image).
Windows as well as all third-party software present on your computer is up-to-date. Especially Java and Adobe Reader – two programs that are commonly exploited by malware for the simple reason that they are installed on so many systems and many users use older versions. For further advice on how to keep your computer safe, also see this article.
In particular, the number and variety of screenlocker infections have exploded in 2012. One of the most common screenlockers is Reveton (see image), commonly referred to as the FBI moneypak trojan. While during the first months of 2012 this infection was seen only occasionally, there was a major outbreak in July/August and since then other variants have also been increasing in prevalence, causing screenlocker infections to surpass the amount of rogue infections.
While the ransom screen can look convincing, it is nothing more than a scam, with the only objective being to scare a computer user into paying the ransom. Fortunately, removal of a screenlocker is possible and our experts on the Emsisoft Support forum are always there to help victims of such scams to regain access to their computer.
Crypto ransomware
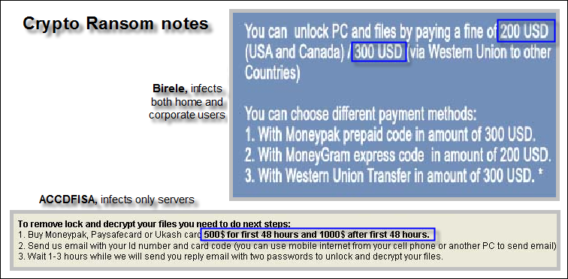
Well-known crypto ransomware infections are ACCDFISA and Dorifel. Unlike screenlockers, crypto malware actually encrypts personal files (on all drives connected to the computer at the moment of infection), which makes it a much more severe threat than screenlockers. Newer crypto malware variants make recovery of encrypted files extremely difficult if not impossible. A preventive security solution is imperative as important personal files could be irretrievably lost, which, especially in a corporate environment can cause serious problems. A few preventive measures, necessary for any server are:
- Make sure all the latest server/software updates and patches are installed. Server hacks are often performed by exploiting an existing software vulnerability. Whenever a zero-day vulnerability is discovered a software company will release a patch to fix this and it is crucial to apply such patches as soon as possible.
- Make sure offline backups (backups stored on a medium not connected to the server computer) are made regularly, because data on any connected backup drive will be affected, making the backup useless.
- Use strong passwords, containing random characters. This will make gaining server access through brute-forcing a lot more complicated.
Other crypto ransomware like Birele infects home users as well as corporate users, using the same methods as screenlocker ransomware. In some cases recovery of the encrypted data is possible.
So, how much money is involved?
A typical screenlocker usually asks for $100 – $200, crypto ransomware may ask a lot more (it is not uncommon for newer ACCDFISA variants to request sums of $4000).
The reason for this difference can be explained by looking at the targeted victims (loss of critical files on a server used to store company/customer data can mean a direct financial loss for the company). Millions are made yearly by people who set up these scams. The images show a few ransom amounts from different variants. As ransomware is so “popular” and recovery can be difficult, prevention is essential, not only for corporate users but for home-users as well. To summarize, we recommended that all users heed the following advice to save themselves a lot of trouble and frustration:
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trial- Make sure all software is up to date and especially when using servers running 24/7, ensure you are using strong passwords.
- Use a real-time Antivirus solution with a good behavior blocker such as Emsisoft Anti-Malware, which will detect the changes ransomware makes at an early stage.
Have a Great (Malware-Free) Day!