ALERT: Google Drive Phishing Scam
A new phishing scam is circulating one of the more populated regions
of the web: Google Drive File Sharing.
Google Drive Scam Play-by-Play
- The scam is initiated by the standard email request to view a shared document on Drive, with a subject line:
Documents. - Opening the email reveals a link to what is said to be a “very important document.”
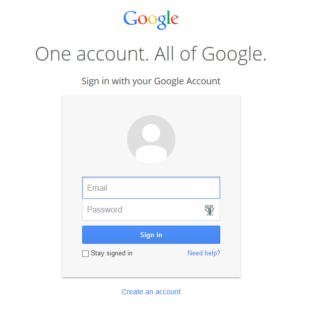
- Clicking on the link leads users to a fake Google log-in page, which is essentially identical to the real one.
- The fake log-in page is even hosted on Google and contains SSL certification.
Users who enter their information and “Sign in” are redirected to an actual Google Doc containing irrelevant information. At the same time, and in the background, the user’s Google log-in credentials are sent to the scammer’s web server.
How to Avoid the Drive Scam
- Delete any unsolicited invitations to share Google Documents.
- Do not click on links you receive from people you don’t know.
- Avoid logging in to Google through emailed links; instead, go to the real Google.com and proceed from there.
- Stop and think: If you use Gmail and are already logged on to your Google Account, you shouldn’t need to log on again to access Drive.
ESSENTIAL READING:
Never fall for a phishing scam again. Read Emsisoft’s Guide on Phishing Scams and how to prevent them
Google Drive Scam Consequences
As Google’s actual log-in page makes clear, your log-in credentials provide access to “One Account. All of Google.” That means that users fooled by this recent scam provide attackers with access to everything they do on Google. Gmail, Google+, Google Calendar, Google Play – all of Google indeed. This consequence highlights the problem with using just one service provider, and thus one username and password, for all of one’s online activities. Doing so may make things easier for you, but it also makes things easier for the bad guys.
Drive Scam Protection
Emsisoft Anti-Malware’s Surf Protection technology automatically protects users from malicious servers like the one used in this Google Drive scam. Surf Protection utilizes a built-in list of dangerous websites that is updated in realtime, and it is completely immune to social engineering tactics like fake log-in pages.
If you have recently logged on to Google through a suspicious email request, Emsisoft recommends that you change your Google password immediately. Even if you haven’t logged on through such an email, it is important to change any account’s password with some regularity. Passwords are your first line of defense to Internet security, and when they are weak or reused the truth is that they’re not much good at all.
It is also important to remember that any email containing attachments, links, or requests to share files should be carefully examined before you click. Emails are common vectors for malware, and messages from anyone but trusted co-workers, family members, or friends should automatically raise suspicion.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialHave a Great (Malware-Free) Day!


