CryptoDefense: The story of insecure ransomware keys and self-serving bloggers

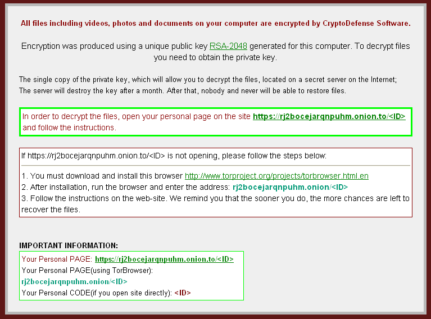
The past week has been particularly eventful for the Emsisoft Malware Research team. It all started about 2 weeks ago, when we received reports of a new ransomware from our friends over at BleepingComputer. A considerable amount of users reported that their files had been encrypted and that all that was left on their system was the following ransom note:
The self-proclaimed name of the culprit? CryptoDefense.
To the attentive reader the name CryptoDefense may look quite familiar, as it sounds suspiciously similar to the infamous CryptoLocker ransomware that has been active since late last year. Like CryptoLocker, CryptoDefense also spreads mostly through spam email campaigns, and it also claims to use RSA with 2048 bit keys to encrypt the user’s files. Like CryptoLocker, CryptoDefense also claims that encrypted files can’t possibly be decrypted; but unlike CryptoLocker this claim was not initially true.
One of the key differences between CryptoDefense and CryptoLocker is the fact that CryptoLocker generates its RSA key pair on the command and control server. CryptoDefense, on the other hand, uses the Windows CryptoAPI to generate the key pair on the user’s system. Now, this wouldn’t make too much of a difference if it wasn’t for some little known and poorly documented quirks of the Windows CryptoAPI. One of those quirks is that if you aren’t careful, it will create local copies of the RSA keys your program works with. Whoever created CryptoDefense clearly wasn’t aware of this behavior, and so, unbeknownst to them, the key to unlock an infected user’s files was actually kept on the user’s system.
If there was a blooper reel of malware authors’ funniest mistakes this one would surely make the cut, and when we first picked up on this little quirk about 10 days ago we simply couldn’t believe it. Once the shock wore off, we quickly developed a decryption tool that could retrieve this key and had a working prototype in just one day. With this, we had a functional decrypter that could unlock CryptoDefense, but we still faced an interesting conundrum. How to get our tool out to the most victims possible without alerting the malware developer of his mistake?
After a bit of thought, our solution was simple: Seek out CryptoDefense victims directly and offer our fix in private. To do so, we searched through various support forums for anyone who may have been affected and also posted announcements to contact us for help, in the hope that these announcements would be seen by people who were searching for a solution. We also shared the decrypter and instructions on how to use it with a number of trustworthy volunteers who help out in these support communities, to give us a wider reach. As it turned out, this approach was very effective, however it did come with cost: Emsisoft received 0 publicity for its findings, and gained little attention from the press.
This lack of publicity was of course our intent, but despite our discreetness, CryptoDefense’s author still caught on to us. After about 5 days, he identified who we were and what we were doing to help his victims, but he still did not have access to the decrypter we used and had no idea how we were unlocking his victims’ files. Surely, this infuriated him, and pretty soon he tried to take down the contact address we left in various support communities by flooding it with emails. No doubt, this was an act of desperation, undertaken to try to prevent us from communicating with victims, but this too proved ineffective. We received over 30,000 emails within just a few hours, but were able to sidestep the attack with some clever server side filtering, and soon we were back online to answer requests for help from CryptoDefense victims.
So why are we writing a blog post about this now? Valid question – especially when we had taken such great efforts to ensure secrecy. Well, once again, the answer is simple. We weren’t the only ones to catch this malware author’s mistake. Other parties did indeed notice what was going on, however they didn’t quite share the same concern for victims as we did, and chose quick publicity over helping CryptoDefense victims recover their files.
On March 31st, a large anti-virus company and one of our competitors decided to release a blog post detailing CryptoDefense and the tremendous mistake its author had made. Unfortunately, this blog post also contained enough information to help the CryptoDefense developer find and correct the flaw in his program. This post was quickly picked up by the press, and merely 24 hours later the malware author started spreading an improved version of CryptoDefense – a version that no longer leaves any keys on the victim’s system. This unfortunate series of events proves a point that Emsisoft has recognized since our foundation: Sometimes there are things that are better left unsaid, even if it means not promoting our company’s achievements.
Until our competitor inadvertently helped CryptoDefense’s author realize his mistake, Emsisoft was contacted by at least 450 malware victims asking for help. We managed to decrypt at least 350 computers, lowering the malware author’s potential income by at least $175,000 and helping many individuals, families, and companies retrieve their important files.
We may not have gotten the attention the other company did, and we may not have made Hacker News, but in the end we believe we did the right thing and contributed to a more Malware-Free World.
For us, that is all that matters.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialYour Emsisoft Malware Research Team.