Are firewalls a waste of time? No. Here’s why.


Everyone knows the term firewall, but few people know why they would ever need one. Go on the Internet and read around, and you’ll find that there are not only many different ideas of what a firewall is supposed to do, but there are also many different technical concepts that fall under the term.
The basic idea of a firewall is a “wall-layer” that protects against attacks from the “other” side. This may seem simple enough, but then many people go on to wonder: Where should that wall be placed? And what, actually, are “attacks”?
To begin, let’s start out with an overview of the places where a firewall can reside.
Hardware firewalls
For high-end users, large networks or servers, a hardware firewall is usually a standalone device. For home users or small businesses, it is typically a component built into a router/modem. When a hardware firewall is used, all network traffic is routed through it before the data reaches individual computers.
As traffic passes through, the hardware firewall takes a deep look into its content to decide what should be let through and what should not. Some firewalls just follow plain rules that the user has defined.
For example: Don’t let anyone from the Internet initiate a connection to any local computer that sits behind the firewall – only allow outgoing connections.
Other firewalls adopt more advanced rules, using protocol-based filters. For example: Let users connect to the Internet, but only through port 80 (the HTTP web server port), and route the incoming traffic to a web server behind the firewall before it reaches individual computers. Still other firewalls are even more sophisticated and inspect every data package deeply on an application layer. Here a rule might be: Allow incoming traffic on port 80, unless it contains any code sequence that may be used to hack the web server residing behind the firewall, such as a cross site scripting attack or an exploit against a database the web server works with.
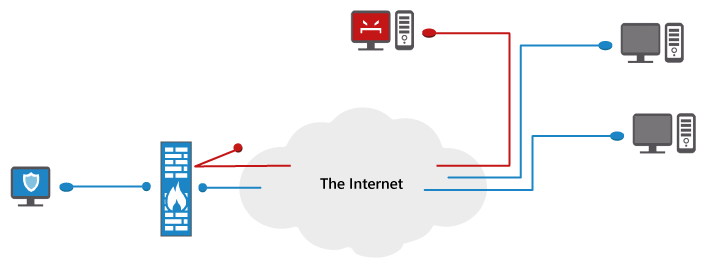
![]() The advantage of hardware firewalls is that they are very literally separate from the computers they protect. All traffic must go through the dedicated, hardware firewall or it will not reach the local, target computer at all. Furthermore, there is no extra “surface area” within a hardware firewall for a malicious data package to sneak through by using manipulative code, such as there might be with a software-based firewall. The data either gets through or it doesn’t. A square peg cannot fit through a round hole.
The advantage of hardware firewalls is that they are very literally separate from the computers they protect. All traffic must go through the dedicated, hardware firewall or it will not reach the local, target computer at all. Furthermore, there is no extra “surface area” within a hardware firewall for a malicious data package to sneak through by using manipulative code, such as there might be with a software-based firewall. The data either gets through or it doesn’t. A square peg cannot fit through a round hole.
![]() The disadvantage of hardware firewalls, however, is that because of their separation and limited surface area (i.e., brain power) the firewall doesn’t really know what’s happening on the computers behind it. The hardware firewall only sees the data traffic generated by these computers, but it doesn’t know which applications are generating this data.
The disadvantage of hardware firewalls, however, is that because of their separation and limited surface area (i.e., brain power) the firewall doesn’t really know what’s happening on the computers behind it. The hardware firewall only sees the data traffic generated by these computers, but it doesn’t know which applications are generating this data.
Therefore, if a user tells a legitimate application to connect to the Internet and that application tries to connect in a way that the hardware firewall is configured to block, the hardware firewall will prevent the application from connecting. Wrong decisions stemming from too strictly configured rule sets that block legitimate services are an inherent problem of hardware firewalls – and they typically result in unhappy users.
Network Address Translation (NAT) Routers
A special form of a hardware firewall is a Network Address Translation, or NAT, router. Most DSL routers in use today are using NAT, and in technical terms they are actually not firewalls, but they have a similar effect.
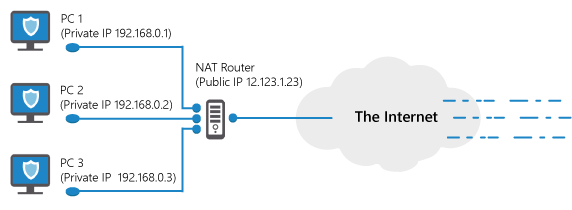
The idea behind NAT is simple. Many households have more than 1 Internet-connected computer, but the Internet account has only one public IP address. That IP address is like your Internet phone number, and it can be reached from anywhere in the world. With NAT, your public IP address is assigned to the router. Incoming data packages must then pass through the router before they reach their destination computer.
A NAT router enables this passage by converting each incoming data package sent to the public IP address to a special IP address that is exclusively used on local networks. These exclusive-use IPs usually start with 10.* or 192.168.* and they can’t be reached from the outside directly. These IPs are actually used multiple times by millions of local networks around the world.
As an example, consider the case of a local computer requesting a website from a public web server. First, a NAT router will replace the computer’s original, local IP with the account’s public IP. At the same time, the NAT router will “wrap” information about the original, local source IP within the data package request, so that it can keep track of which computer it belongs to when it returns. When the web server responds, it will then send the data back to the public IP – at which point the NAT router will “unwrap” the information it appended about the local source IP and forward the data package to the computer with that local IP.
![]() NAT routers give us a huge advantage: Computers that are in a NAT can reach everything on the outside, but nothing on the outside can directly connect to a computer in a NAT, unless the NAT router is specifically configured to forward individual protocols to single machines. In this way, NAT can enable a very powerful “firewalling” effect, despite the fact that NAT is not usually called a “firewall.”
NAT routers give us a huge advantage: Computers that are in a NAT can reach everything on the outside, but nothing on the outside can directly connect to a computer in a NAT, unless the NAT router is specifically configured to forward individual protocols to single machines. In this way, NAT can enable a very powerful “firewalling” effect, despite the fact that NAT is not usually called a “firewall.”
Software firewalls
A software firewall runs on a local computer, but basically does the same job as a hardware firewall. Software firewalls inspect network data packages and decide which data to block or allow, based on rules.
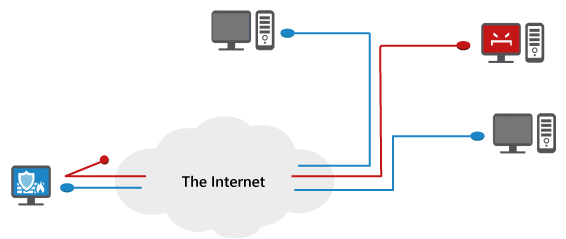
![]() One of the biggest things software firewalls have going for them is that they are usually not as expensive as standalone hardware firewalls. Another major advantage of a software-based firewall is that in addition to analyzing network traffic, it can also link each data package with the program that generates it – which is exactly what hardware firewalls can’t do. A software firewall can analyze traffic and program behavior as a whole, which means it can make decisions with much more precision than a hardware firewall ever could.
One of the biggest things software firewalls have going for them is that they are usually not as expensive as standalone hardware firewalls. Another major advantage of a software-based firewall is that in addition to analyzing network traffic, it can also link each data package with the program that generates it – which is exactly what hardware firewalls can’t do. A software firewall can analyze traffic and program behavior as a whole, which means it can make decisions with much more precision than a hardware firewall ever could.
For example: If a data package genuinely originates from a program that was made by a trusted software vendor, there is no need to ask each time whether to allow it, even if it violates some pre-configured rule. A software firewall will recognize this benign origin and grant an exception.
A good software firewall is one that shows almost no warning messages, unless it is certain that there is a real attack and that some malicious program is attempting to gain access to your computer. An overabundance of warnings is not a good thing because it desensitizes the user to alerts.
![]() Too many warnings can be like the boy who cried wolf, or in firewall terms “the security software that shows multiple alerts every single day.” Who has not dealt with a product like that? You see so many warning messages that you eventually just click “Allow,” no matter what the warning says. These types of software firewalls are in reality just a waste of computing resources because even when they detect real threats, their users unknowingly (and understandably) allow those threats to get through.
Too many warnings can be like the boy who cried wolf, or in firewall terms “the security software that shows multiple alerts every single day.” Who has not dealt with a product like that? You see so many warning messages that you eventually just click “Allow,” no matter what the warning says. These types of software firewalls are in reality just a waste of computing resources because even when they detect real threats, their users unknowingly (and understandably) allow those threats to get through.
A good software firewall is also one that doesn’t block needed applications. This is after all what most users get so annoyed about with hardware firewalls (maybe you’ve experienced this at work ;). Granting permission to a certain legitimate application on a hardware firewall can be quite laborious. First, you have to open the admin interface; then, you have to find the right configuration tab and set up a complicated rule – provided of course you can understand the rule set.
![]() Software firewalls are better here as well because they are always locally at hand, and they are actually even smart enough to discern harmless actions, eliminating the need to configure new rules all by yourself.
Software firewalls are better here as well because they are always locally at hand, and they are actually even smart enough to discern harmless actions, eliminating the need to configure new rules all by yourself.
When do you need a software firewall, then?
The truth is, if you exclusively connect to the Internet via a local home DSL or cable account that works with NAT, you should save the money you’d spend on a software firewall and get your best mates a cup of coffee instead. A reliable antivirus software with a great detection rate and a powerful behavior blocker is all you will need. If however you are using a computer that frequently connects to the Internet via third party networks, a software firewall is worth the investment.
![]() Think of public WLANs, like at the coffee shop you took your friends to, or plugging in a network cable at some foreign hotel. Once you are connected, every other computer user on such a network can try to connect to your machine. And why would they want to do that? To try to find a leaky component that can be exploited to take control of your computer for financial gain, or to steal private data (also for financial gain). A software firewall that hides all the open ports on your computer effectively reduces the surface area and success rate of such attacks.
Think of public WLANs, like at the coffee shop you took your friends to, or plugging in a network cable at some foreign hotel. Once you are connected, every other computer user on such a network can try to connect to your machine. And why would they want to do that? To try to find a leaky component that can be exploited to take control of your computer for financial gain, or to steal private data (also for financial gain). A software firewall that hides all the open ports on your computer effectively reduces the surface area and success rate of such attacks.
Frequent misconceptions about software firewalls
Misconception 1: Firewalls detect malware
The main purpose of a software firewall is to eliminate potential entry points attackers could use to get onto your computer from the outside. Software firewalls are not made to detect active malware that is already on your PC and communicating with some stranger half way across the world.
![]() Why not? In short: Once there is active malware on your PC, it is too late. There is simply no point in blocking outgoing connections sourced by malware, because if the malware managed to run it probably also managed to disable your entire firewall and manipulate all sorts of system settings. This is not because firewalls are incompetent – it is simply because they are not designed to block malware. Blocking malware is the work of anti-malware. A firewall instead “hides you” from the outside, by denying communication with other programs through certain “channels” or ports.
Why not? In short: Once there is active malware on your PC, it is too late. There is simply no point in blocking outgoing connections sourced by malware, because if the malware managed to run it probably also managed to disable your entire firewall and manipulate all sorts of system settings. This is not because firewalls are incompetent – it is simply because they are not designed to block malware. Blocking malware is the work of anti-malware. A firewall instead “hides you” from the outside, by denying communication with other programs through certain “channels” or ports.
Misconception 2: Firewalls are always HIPS (host-based intrusion prevention systems)
Not so long ago, all software firewall products available did exactly what users expected them to do: Filter network data. Today, that’s still the classic definition of the term “firewall;” however, since firewall technology was soon developed to death (no more space for innovation -> all vendors offering a similar level of quality), vendors started to add new and somewhat overkill features to their firewall products, such as monitoring of all sorts of operating system changes and detection of all sorts of non-standard-compliant code executions by programs and thousands of other ‘suspect’ things that tend to fall under the term HIPS today.
The major problem with these technologies is that for all their monitoring and detection capability they are relatively dumb. They tend to raise an alert for each and every action that could possibly lead to an attack, but the truth is that about 99.9% of all such alerted actions are not malicious. As mentioned before, such alerts are annoying and even dangerous because they can train users to click “Allow,” day in, day out.
![]() HIPS are therefore recommended for experts only, who can fully understand the large amount of alerts they produce and take advantage of the extra protection layer this can provide. This doesn’t make HIPS irrelevant to everyday users, though. In fact, the technology behind HIPS is what eventually evolved into behavior blocking, an essential component of modern anti-malware.
HIPS are therefore recommended for experts only, who can fully understand the large amount of alerts they produce and take advantage of the extra protection layer this can provide. This doesn’t make HIPS irrelevant to everyday users, though. In fact, the technology behind HIPS is what eventually evolved into behavior blocking, an essential component of modern anti-malware.
Thanks to what behavior blocking borrows from HIPS, false alarms from antivirus software using the technology are now extremely rare. Behavior blocking isn’t HIPS though, and neither term is freely interchangeable with “firewall.”
Firewalls and Emsisoft
Emsisoft has gathered knowledge on firewall-, HIPS- and behavior blocking technology for almost a decade now. Emsisoft Internet Security packages this knowledge to improve your digital life online.
Emsisoft Internet Security adds a software firewall component to the proven technology of Emsisoft Anti-Malware, which means it can protect you from malware AND keep you invisible to network intruders. This makes it a perfect fit for home users and small businesses, who frequently travel beyond their home network and who want something simple-yet-intelligent that will keep their information secure, no matter where they go.
Have a great (firewalled) day!
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trial