How downloading one program can give you six (!) PUPs

There are multiple players involved in the distribution of Potentially Unwanted Programs (PUPs). As a result, you can face something that’s best described as cascading PUPs: you can end up with a sequence of PUP offers after another, depending on your download method.
The multiple ways you can get a PUP
Generally, you can get a PUP from one of the following sources:
1) Directly from the software vendor: The software vendor itself bundles unwanted offers, which means that when you go to the direct source (website) of what you want to download, you’ll still encounter PUPs because the software vendor works directly with the PUP creators. The PUP creator pays the software vendor for each install they can give them. We gave a few examples in this article, in where we showed that most free antivirus vendors bundle PUPs when you download the software from their website.
2) Download portal installers: Many download portals use a special installer (also called a wrapper) in where they can add PUPs. Instead of using the direct installer from the software programs they offer on their site, they “wrap” the program in their installer instead (often without the software maker consent) so they can push PUPs and make money. These extra downloads are traded on PPI (Pay Per Installation) ad networks and displayed dynamically depending on which vendor bids the highest amount, like an ad box on Google.
3) PUP bundles extra PUPs: The toolbars and other PUPs that install with a program, come with and install even more potentially unwanted programs. This is a result of these PPI networks, because they don’t verify which software they install and if that also comes with PUPs.
4) From the PUP itself: PUPs also distribute through ads and pop-ups on certain websites. These are often temporarily created pages with warnings as “software XYZ needs an update”. This method is left out in this article, since we’re only focusing on PUPs you can get from downloading a program.
Example of cascading PUPs
Say you want to install KMPlayer, which is an immensely popular free video player that provides top quality playback of different forms of media. Showcased below is how you can end up with multiple PUPs, coming from different sources, by downloading this program.
1 ) PUPs installed via the software vendor
Increasingly, many PUPs today are pushed directly by the software program you intend to download. If you go directly to the vendor’s website and download their program, you can end up with PUPs. We went to KMPlayer’s website to download the program, and this is what happened.
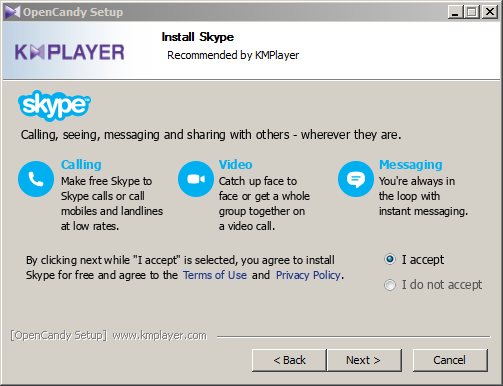
Skype, a useful video chat application is actively being bundled by the vendor. In the installer, it is clear that Skype is “Recommended by KMPlayer”. Even more disturbing is that Skype is part of the “Open Candy” unwanted offer, which is a known adware program.
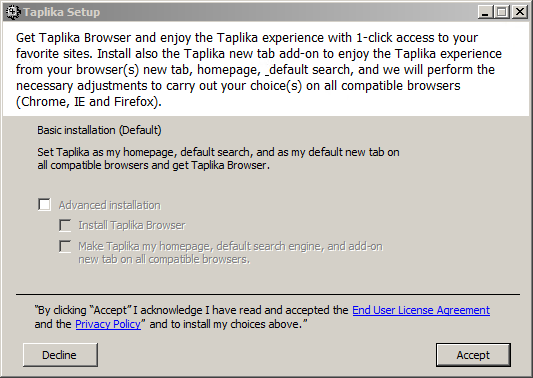
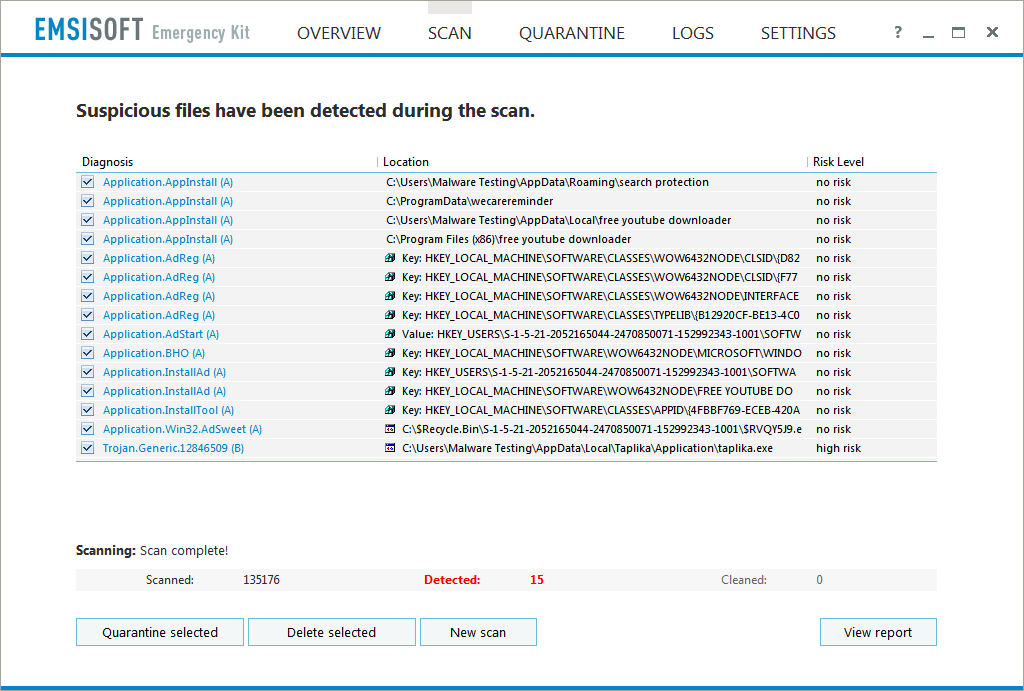
Next, KMPlayer offers SHAREit, which brings the PUP count to 2 so far. At the end of the installation process, KMPlayer bundles one last PUP known as Taplika. It modifies your homepage, search engine, tab settings, and installs its Chromium based Taplika web browser.
KMPlayer’s once decent reputation is at risk by bundling this aggressively. PUPs offers in this download method are unavoidable if the software of your choice bundles unwanted programs in exchange for pay-per-install money.
2) PUPs are installed via a download portal wrapper
As you can see above, when you download KMPlayer directly from their website you can end up with three PUPs (Skype, SHAREit and Taplika). Say that instead of downloading from the vendor directly, you decide to download KMPlayer from a download portal. In this case we went to Download.com and used their “secure” installer to download KMPlayer, and were presented with various unwanted offers before an actual application installation can begin.
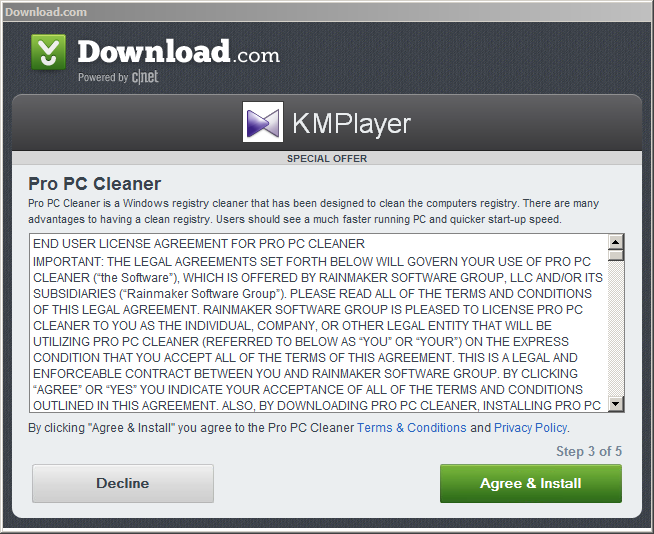
Upon launching the CNET “secure installer”, Pro PC Cleaner is a “special offer” that is bundled by Download.com when you attempt to download KMPlayer. Similar to a rogue, Pro PC Cleaner will scan your computer for supposed issues and then present several annoying pop-ups and fake error results. After the PRO PC Cleaner offer, Download.com’s installer offers Spigot, a PUP frequently bundled by download portals. After these two PUPs Download.com finally installs KMPlayer, which already comes with 3 PUPs from the vendor, bringing the total to 5 PUPs.
![]() PUP-count: 5 PUPs if you were to download KMPlayer through this method.
PUP-count: 5 PUPs if you were to download KMPlayer through this method.
3) PUP itself installs more PUPs
In this instance, an already unwanted program comes with one or more additional unwanted program(s). In this case, one of the five PUPs we encountered so far by going through this download process installs even more: Taplika, the PUP that came directly when you download KMPlayer from their website, installs another PUP. At this point, perhaps your antivirus will kick in and do its job blocking the resulting unwanted program(s) in realtime, but if that’s not the case you’ll never know how this PUP got onto your computer.
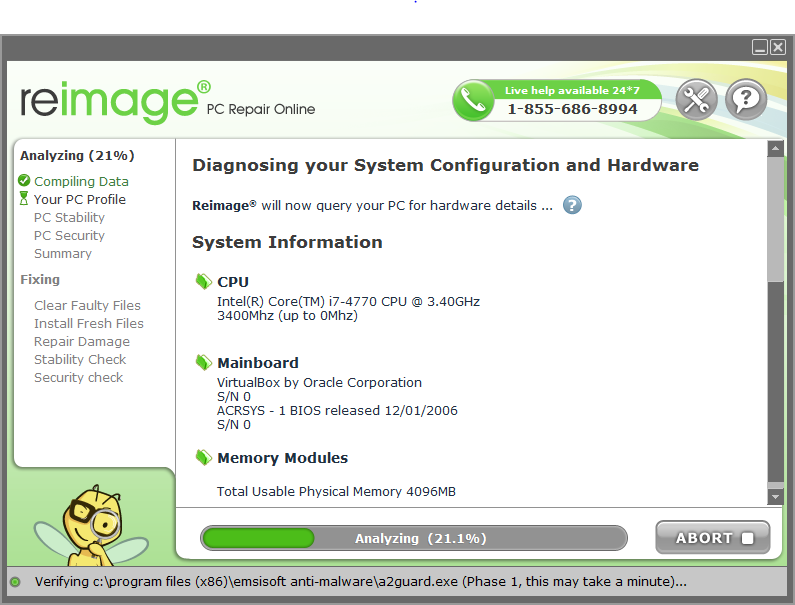
The Taplika PUP left Reimage PC Repair Online on the computer. This is an example of a PUP that installs silently in the background, which is perhaps a strategy more PUPs are going to use if too many people uncheck boxes during installation. Reimage PC Repair scans your PC under the premises of several different categories and reports information about your system. Reimage seemingly reports errors concerning “PC Security” and “PC Stability Issues” that it can repair. While this software is not necessarily malicious, it keeps nagging the user without cause, due to that – it is recommended to remove it.
![]() Total PUP-count: 6 PUPs if you were to download KMPlayer through this method.
Total PUP-count: 6 PUPs if you were to download KMPlayer through this method.
Money is the root of all “PUPs” – What does everyone involved get out of the deal?
In the example in this article you can end up with six unwanted programs on your computer in the worst case scenario. Why is everyone involved in this game so eager to get PUPs onto your computer? The popular saying “money is the root of all evil” is often thrown around, but where does its relation to PUPs come in? Bundling or creating PUPs can be a very lucrative business. In this case, all players involved make money: the software vendor, the download portals and the PUPs itself.
Software vendor: the software vendor gets money from the PUP developers for each install of the PUPs they deliver. In the example we used in this article, KMPlayer gets money for each of the three PUPs a user installs. We provided more examples in this article.
Download portal: the download portal gets money for the PUPs they install through their installer (wrapper). In this case, from the makers of Pro PC Cleaner and Spigot. The software vendor is generally not involved and benefiting in the download portal wrapper installations.
PUPs: some PUPs also work together to install each others products, and pay each other in the process.
As discussed earlier, PUPs then have several ways of making money. The most common form is by hijacking your browser: they can then show you ads where they get paid for, monetize or sell your search and/or browser behavior or redirect your homepage. Each PUP generally comes with its own privacy policy, which is another reason you need to be cautious. Additionally, some PUPs can cause potential security holes. The PUP (adware) Superfish is a good example of that.
What are the best ways to avoid falling victim to aggressive PUP bundling?
Listed below are tips on how to defend your PC from PUPs and how to remove potential infections that may slip by.
The 1st Defense – Use caution and good judgement when downloading software. Users should always stay visually and mentally aware and on the lookout for anything that may be suspicious. Also be cautious for ad-banners that contain download buttons, they are often very irritating and distract from the real downloads on portals.
The 2nd Defense – If at all possible, avoid the use of download portals that are known to use PUP wrappers and bundle junkware from the software vendor without clear disclosure or warnings. Make it a point to also be weary of installing software from specific vendor websites as they distribute PUPs a well. Last but not least, avoid suspicious freeware applications as “free” is not always the best choice. Not all freeware is bad, but think about how the freeware you use makes money off of you before you install it, so you can make a choice whether you’re OK with that or not.
The 3rd Defense – Some users like using a program called Unchecky, an application that unchecks unwanted offer boxes for you during installation. Some PUPs may install silently on the background or use different methods than opt-out to install, so still use caution during installation.
The 4th Defense – Use an up-to-date antivirus software with sufficient zero day threat protection and choose an antivirus program that has PUP detection, such as Emsisoft Anti-Malware, which can detect, block, and remove malware and potentially unwanted programs. If you don’t have antivirus protection or if you use a different antivirus than Emsisoft, you can use second opinion scanning software such as the free Emsisoft Emergency Kit to scan for and remove PUPs and other malware.
 The 5th Defense – Although not always recommended for novice users, using a whitelisting application may be an option for more advanced users. Whitelisting is the exact opposite of blacklisting that is used by antivirus software to detect threats. A whitelist is used to prevent unauthorized software or programs from running. An example of such an application is Microsoft Windows AppLocker.
The 5th Defense – Although not always recommended for novice users, using a whitelisting application may be an option for more advanced users. Whitelisting is the exact opposite of blacklisting that is used by antivirus software to detect threats. A whitelist is used to prevent unauthorized software or programs from running. An example of such an application is Microsoft Windows AppLocker.
If you make use of excellent security practices and take all the necessary precautions, you should have little to nothing to worry about. In the event you do manage to encounter potential intruders, it is great to know that you have two awesome sidekick’s to back you up during the removal process.
Have a great (PUP-free) day!