Antivirus software: protecting your files at the price of your privacy


“Privacy” is the ability of an individual or group to seclude themselves, or information about themselves, and thereby express themselves selectively. [Wikipedia]
We have to make a statement here: Privacy is important. Period.
Large companies and governments unfortunately tend to disagree with us these days. They want to make us believe that security and comfort always come at the price of privacy. We think that the risks for potential misuse of collected mass data always outweighs any argument for the advantages of gained functionality that is based on big data analysis.
Only a few people are aware that one of the biggest threats to their privacy is actually a piece of software running on almost all computers. A software they have bought believing it would actually protect their data: antivirus software.
Antivirus features that rely on techniques which affect your privacy
There are a couple of highly questionable features in everyday’s protection software that we’d like to analyze a bit more in detail:
1) Scanning and blocking of dangerous URLs
Almost all internet security products claim to prevent you from accessing dangerous and fraudulent websites to keep you safe from malware downloads and fraud attempts. To do that, they typically forward all website addresses you visit to a centralized server which scans the domain names and paths against a massive database of dangerous URLs.
You may ask why these scans can’t be done on your local computer. The reason behind this requires a bit of technical knowledge: to check addresses locally would require the whole database to be constantly transferred and synchronized via online updates onto your computer. The problem with that approach is that there are literally millions of known bad website addresses that change very frequently. Online updates of protection software would become far too heavy for most users and every day hundreds of megabytes of data would need to be updated, which is simply impractical. That’s why it is more efficient to send each visited address to a server who does all the work and just returns a “safe” or “dangerous” flag.
The bad thing about this technology is that the antivirus vendor can track ALL your visited websites. Even worse: some vendors can read encrypted data that you enter on online banking websites or other private communication channels. These massive database servers are of course protected at the highest level, but history shows us that data is never 100% safe. Just think for a second about what would happen if that antivirus vendor lost control over their servers for any reason, and what would happen if your surfing habits were shared with criminals.
2) Cloud based file scanning
A few years ago, any software company who didn’t join the “cloud” hype was considered lame and old-school. There is no doubt that cloud computing—which means shifting heavy computing jobs from the local PC to a server ‘somewhere’—can be a very useful thing to speed things up. Since the early days of antivirus software, file scanning is typically done on the local computer. Antivirus vendors create a database of fingerprints/signatures of viruses and other threats, then send that collection of unique markers to the antivirus software on your computer where it compares all local files with each of those signatures.

Cloud scanning sort of reverses that process. It creates signatures of all potentially suspicious files on your hard disk and uploads them to cloud servers where these signatures are scanned against a large database of known threats. Signatures are typically short sequences of letters and numbers, so they don’t allow any antivirus vendor to restore your file content. Though they know which programs you run on your PC if the same pattern was seen before and other meta data can be linked to the data set.
Many antivirus vendors go one step further: They don’t just upload a unique file identifier, they upload the whole file so it can be analyzed on a cloud server. For program files that typically doesn’t mean any danger, but has any antivirus vendor ever published their rules for selecting files that are to be uploaded? You are forced to blindly trust that they don’t send any of your private data files.
3) Collecting the computer’s meta data
Sometimes, collecting meta data about a computer can even be more helpful than collecting data files. Meta data describes all sorts of information such as computer name, user logon name, IP address, country, operating system, running programs, their version numbers, hardware components or similar. Collecting and combining these data points allows someone to sketch a quite precise picture of each computer and derive a certain level of exposure to online threats.
But that data also reveals a lot about the person sitting in front of the PC. Combining data can tell which software you have used for how long. Where you live, what your areas of interest are, your age group, how much you spend on hardware, etc.
AV-Comparatives, a well respected security software testing organization, conducted an analysis of Data Transmission in Internet Security Products in 2014. A quick overview of their findings:
- 8 out of 21 antivirus submit hardware information, and 5 didn’t disclose that information.
- 6 out of 21 submit information about running programs, and 4 didn’t disclose that.
- 18 out of 21 submit website addresses (malicious and non-malicious).
- 5 out of 21 submit “suspicious” non-executable files (such as documents), and 7 didn’t disclose that.
- 6 out of 21 don’t allow their users to opt-out of sending files.
AV-Comparatives recommends reading the privacy policy and EULA of vendors carefully, so that users can make an informed decision. They state: “Users should also avoid being lured into using free products that require submitting personal data (data mining is a business model too, as well as the inclusion of third-party toolbars which collect information on their own).”
Antivirus vendors that trade user data
 Users who run Avast’s security software should be aware that their surfing habits are tracked by a company called Jumpshot who creates statistics based on visited websites, as Avast recently announced. These might be impressive and interesting statistics, but keep in mind that once data is sent to countries with different legislation, there is little control left on what really happens with all the information. Avast’s installer also preserves the right to submit usage data without specifying further what that means.
Users who run Avast’s security software should be aware that their surfing habits are tracked by a company called Jumpshot who creates statistics based on visited websites, as Avast recently announced. These might be impressive and interesting statistics, but keep in mind that once data is sent to countries with different legislation, there is little control left on what really happens with all the information. Avast’s installer also preserves the right to submit usage data without specifying further what that means.
Alternative ways to protect that don’t compromise privacy
Some good news for all of you who have been told that there are no alternatives to collect data in order to keep you safe from malware: there are alternatives. They may require a bit more effort in programming and may be a little less convenient for software vendors, but they are proven to be just as efficient as methods that impact your privacy.
Blocking website domains instead of website addresses
Instead of blocking individual website addresses, Emsisoft Anti-Malware and Emsisoft Internet Security use a locally stored blacklist with bad domain names. Most malware today is spread by hacked web servers. If a specific server is hacked, we don’t trust any website on that server anymore until it is clean again. So we simply block access to the whole server, which reduces the amount of data to be stored in a blacklist-file significantly, effectively allowing us to avoid cloud based scanning and do the checks locally on your computer only. Updates of that file are provided every 15 minutes. Tests confirm that this approach often beats cloud based scans.
Avoiding file uploads for cloud scanning
Emsisoft products never upload any files to our servers without asking you first. Any scans that require information to be obtained from a server rely on a minimum amount of data. In most cases, only a file hash (32-40 letter checksum sequence) is required to verify if a program is safe or not. User documents are never uploaded at all.
Minimizing meta data collection
AV-Comparatives confirmed in their report that Emsisoft is one of the most privacy conscious antivirus vendors around. Our products avoid sending any information that may be used to create detailed user profiles.
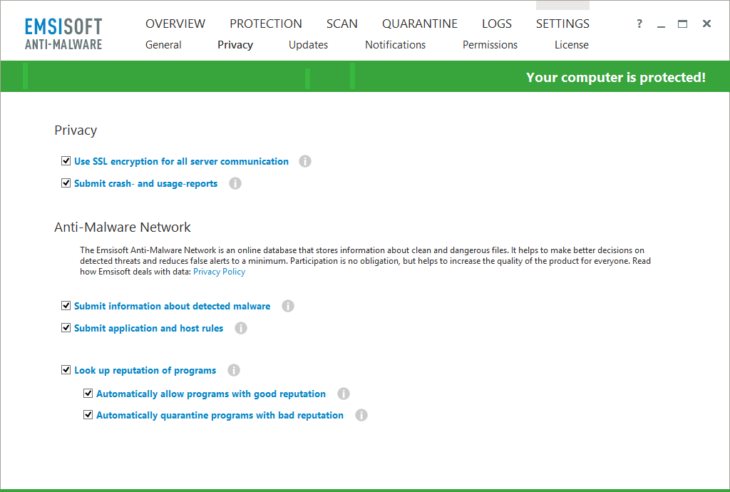
Privacy options we provide our users
With the recent release of our version 10 protection product series, we are once again one step ahead of our competitors in terms of privacy. You can find all settings that may have an impact on your privacy in a newly formed Privacy settings dialog. There you can choose whether you want to allow us to create statistics based on detected malware, or configure your participation in the Emsisoft Anti-Malware Network, which helps to improve the malware detection quality for all users. Options for disabling SSL in server communication and creating crash reports are included too.
During installation of our software you are asked whether you are fine with sharing some of your data or not. We don’t force you to participate at all and we don’t even set a default option for these things— it’s totally up to you.
Conclusion: Privacy doesn’t need to be given up on
Emsisoft is the living proof that privacy doesn’t need to be traded for security. There are ways to provide the same, if not a better level of protection, without harming your privacy.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialHave a nice, private day!