Leaked files from state-sponsored hackers reveal which protection their trojans can’t get past

Your typical anti-malware provider has their products tested in a lab to bolster credibility. But with recent leaks on massive surveillance companies, there’s new data available to help measure how good popular anti-malware products are at detecting unwanted threats.
What do surveillance companies have to do with anti-malware?
There is a lot of controversy that surrounds big surveillance firms, and for good reasons. These companies help their clients (often times government agencies) spy on people and on other organizations or countries.
While many claim that this is for the safety of their people, big governments often have to hire these firms that specialize in making malware, breaching the privacy of unassuming individuals. How these firms develop their malware deeply involves anti-malware programs – they must test leading anti-malware software so that they can develop undetectable trojans that successfully infect systems.
Normally, this kind of internal information is kept incredibly private. These firms have highly sensitive data concerning their products and their customers that could really compromise international intelligence agencies.
But some high-profile leaks in the last twelve months are not only political, they’re practical. Below we’ll discuss two surveillance hacks that reveal which anti-malware providers are actually most effective in keeping unwanted programs off your computer.
Hacking Team’s trojan detected by 5 out of 34 antivirus vendors
Hacking Team is a Milan-based company that provides surveillance technology to clients from all over the world, including governmental agencies in countries such as Russia and the United States.
In early July, an unknown hacker released a torrent of 400 GB of company data. This included internal communications and code, as well as records of anti-malware testing. This screenshot of one of their internal documents shows a number of anti-malware suppliers and how Hacking Team’s trojan, Galileo, fared against their products in performance tests.
Green means the malware bypassed the antivirus and was able to infect the system. Yellow means it was able to infect the system and was operational, but during the process some unspecific pop-ups may have appeared (like a generic firewall alert). Red means that a malware detection was triggered. A few vendors were ‘blacklisted’ by Hacking Team’s trojan. That means, the malware doesn’t even bother to start any action when it notices that a specific protection software is running. That way it remains hidden, but also can’t do any spying. As you can see in the full table, only 5 out of 34 vendors were able to detect the Hacking Team malware.
FinFisher’s malware agent FinSpy able to bypass 31 out of 35 vendors
FinFisher is a German-based firm responsible for programs that enable governments to surveil citizens. This type of surveillance, called “lawful interception malware” is very controversial, as it’s questionable if these programs actually help protect people at all.
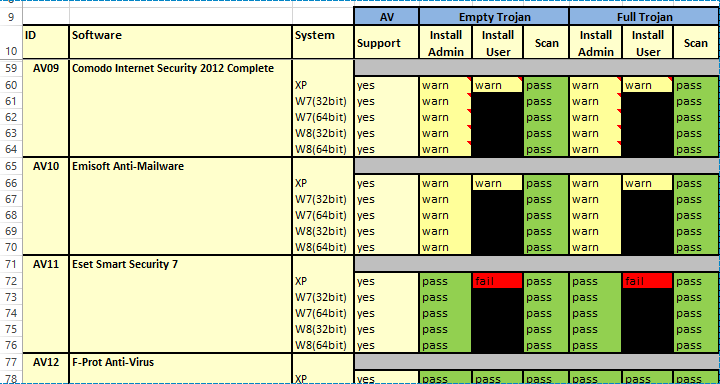
In September 2014 Wikileaks took a stand against FinFisher and accused the surveillance firm of selling their products and services to oppressive regimes. This leak involved the company’s malware as well as internal documents. Among the information leaked was a table of anti-malware softwares, which reveals what programs their malware agent FinSpy was able to dupe and which ones it wasn’t. FinFisher tested different programs with different versions of the trojan, and recorded how the different anti-malware programs responded to each threat. The following table gives an overview of the results. In the “Full Trojan” column (Install Admin) you can see which vendors warned or blocked the full trojan.
The green “pass” means that the antivirus didn’t detect any threat. The yellow “warn” means that the antivirus detected the trojan as suspicious and alerted the user about it. The red “fail” means that the trojan was detected as malicious. As you can see, the majority of vendors were not able to detect FinSpy at all (green). Only 4 out of 35 vendors reliably detected the threat as suspicious (yellow) or malicious (red) and therefore blocked it completely.
Consider your privacy needs when choosing software
In studying the tables above, it’s important to remember that products that failed to detect these trojans may be just as likely to fail to detect others. It’s also possible that these products are run by companies that work with state-sponsored firms rather than against them. What are your privacy needs? Are you concerned with protecting yourself against government surveillance?
Choosing a program that keeps you safe from all types malware may seem impossible, but the tables above give you an unbiased look at what really works against surveillance trojans:
1. Vendors that detect Hacking Team’s trojan
Emsisoft was able to block the Hacking Team trojan and was given the great honor of being blacklisted as a result! Sophos and CMC AV were the other programs that Hacking Team blacklisted. Comodo and Rising also did a great job by detecting and blocking Hacking Team’s trojans in most cases. A few other vendors showed “not-so-worrysome” popups for Hacking Team, while all other vendors were not able to detect the trojan at all.
2. Vendors that detect Finfisher’s malware
Emsisoft Anti-Malware, Comodo Internet Security, Outpost Security Suite Pro and Trusport Total Security are the only vendors that were able to detect Finspy’s full trojan in all cases.
As shown above, Emsisoft performed very consistent since both Hacking Team and Finfisher’s malware had issues getting past (if at all). Whatever program you choose, know that your privacy is important — don’t put it in the wrong hands.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialHave a great, malware-free day!