Prevention vs Cure: Why you shouldn’t just rely on malware cleaning


Another strange pop-up or unexpected crash, and it’s time to take your computer back to the shop, right?
But what if you could avoid losing precious data and time spent with your computer? What if this whole cleaning step could be eliminated entirely?
This is why protection is a pivotal topic in the antivirus industry. Cleaning and protecting seem like two methods that aim for the same goal: a computer that is free of any online threats. While a few people still believe that they have nothing important to lose on their devices, we’d like to analyze two significantly different approaches for security conscious people: cleaning an infected PC versus keeping a PC clean.
The end result or effect may look the same at first glance, but once you learn a few technical details and understand how things truly work, you’ll be surprised how different both approaches actually are.
No need to wear a seat belt, the doctors will fix me!
Not practicing protection because you’ll clean your computer later is like choosing to ride in a car without your seatbelt because the doctors will patch you up in the event of an accident.
If you can imagine how ridiculous that is, then you can understand how important protection is for your PC. You’re basically acknowledging that your computer could be permanently damaged, very expensive to fix, or at the point of no return!
Prevention is more than just the preferred method or smartest choice. Below we’ve included some scenarios to illustrate what’s possible if you rely exclusively on cleaning instead of protection.
Infection case #1: Home user with PUPs that continue to collect data after removal
You’re at your PC hoping to do some online banking, but your screen is obscured by nasty, adult pop-ups and you have no clue how they got there or how to get rid of them. Your next thought is to download one of the many cleaning tools out on the internet to get rid of them. After all, that worked for you before.
The infection you had was a PUP (Potentially Unwanted Program). It doesn’t put much effort in hiding itself, so luckily for you, it can be removed relatively easy.
The price you have to pay for that experience: maybe a few hours of research, downloading tools, and conducting the scans and clean runs. The hidden price: that software collected personal information about you and your computer usage habits. You may still encounter weird occurrences in the future while surfing the web, and you may be recognized by various websites and their ad network partners.
Infection case #2: Business PCs manipulations that can hardly be reverted
Some computer guy told you to make sure automatic Windows updates are enabled on all the office computers. You check the update settings and realize that the service is completely disabled and won’t allow you to turn it on. Something is obviously wrong with your computer. Just recently you wondered why all Google ads look a bit different, larger, and more prevalent. You pick a malware scanner and run a thorough scan.
Whoa! 104 infections found! Most of them are harmless PUPs, but there are also a couple dozen active “Agent” trojan findings. They are remote controlled by a server and form huge botnets with hundreds of thousands of other victim computers. It’s the ideal tool to send billions of spam emails, or even run coordinated DoS attacks on big online services (unless, of course, they’re willing to pay a huge ransom).
Another listed infection on your scanner is labeled “Rootkit,” which is actually a well-hidden piece of malware that could easily go unnoticed, but watches your online banking activities and redirects some money to an anonymous account in a foreign country.
Your malware scanner does a great job in cleaning all those infections, so you have nothing to worry about, right?
Well it appears that even though all of the malware was properly removed, your Windows updates are still not working and some operating system components used to enable them don’t even exist anymore. This is because it’s just not the scope of your malware scanner to re-download missing files from Microsoft onto your system. Additionally, your malware scanner can’t know which of your system settings are intentional and which ones are malware-manipulated. As a result, there may be one or more open gates inviting new attackers to take over your computer again.
Just imagine a newly created user account with full administrative rights, or new network shares that make all of your data accessible to the public.
Bottom line: you need to be a real expert with years of malware analysis experience to be able to reconstruct everything the malware changed, down to the smallest level. It would take days to do that properly, and to make sure there is absolutely no hidden setting left that could compromise your entire security framework again.
Infection case #3: Local hospital irreversibly loses patient data
It’s Tuesday morning and you have the early shift, and the first patients of the day are waiting for their examination. But something is wrong with the IT. Very, very wrong! Instead of pulling up the patients’ details, all your computer shows is an FBI-branded screen that tells you to send $1,000 USD via an anonymous online payment system! You have 48 hours to do this, or else your entire patient database will be lost forever.
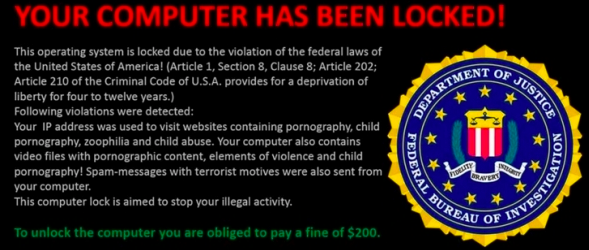
FBI Warning screen
You understandably panic and call the most expensive IT company for advice. All they can tell you is that your files have been encrypted with a secret key that can’t be cracked in less than 2 million years. After some further investigation they give you more bad news: Your automatic backup system failed a couple of weeks ago because nobody noticed the alerts that the software gave on the server. Bummer! All you can do is reinstate an outdated backup and try to reconstruct all data that has been added since then, or pay that hefty ransom.
This is the situation when malware cleaning has reached its limits. You may be able to remove the crypter if it’s still present, but you have most likely no way to decrypt all your files. It’s a nightmare scenario, and yet it happens to thousands of home users, businesses and institutions around the world every day.
Cleaning is like patching up holes only larger than 2″ on a leaky boat
It will probably give you enough time to rescue your most valuable goods, but sooner or later your boat will sink. It’s the exact same thing with your computer. In the best situation you will earn a cleaned PC that allows you to make a backup of all your documents, pictures and other data, but it is nearly impossible to get a truly clean system back ever again.
The more effective solution: clean, backup and then “nuke and pave”
To make this very clear, as there are still loads of misconceptions about it all over the internet:
A once-infected computer can’t be trusted anymore.
After cleaning and making backups of your data, you always have to wipe and reload your entire operating system from scratch. We fully understand that many IT people will moan about that idea and argue, “but it takes sooo long to do that, and who’s going to pay for it?” or maybe, “there is necessary old software on that PC that can’t be found/installed anymore”. But honestly, if you really want to clean a system well, it always takes a long time. Furthermore, if the software is truly so old that you can’t find it anymore, isn’t it probably time to replace it with something more modern anyway?
How to avoid all the hassle: protect your PC!
Protection is ideally established in multiple layers that complement each other:
- Make sure all software is up-to-date.
Windows updates should never be avoided for any reason. Never postpone them, for your own sake. On almost every patch-day (that’s when Microsoft releases a new set of updates for Windows) multiple critical security leaks are being fixed. Many of the patches close critical security leaks that potentially allow attackers to take over your PC remotely. Don’t forget, internet browsers and their plugins like Flash and Java need to be updated as well! Often you don’t even need to download and run a malware file manually to become a victim. Most infections occur via drive-by attacks while you’re surfing the web, or through fully automated bots searching for new victims around the world all day long.
- Use the best malware protection money can buy
Needless to say that you can’t go wrong with Emsisoft Anti-Malware or Emsisoft Internet Security. Emsisoft’s protection software had the smallest number of compromised systems across all 6363 real-world test cases performed by AV-Comparatives in 2014. If you’re using a pre-installed antivirus program that came with your computer when you bought it, make sure the license has not expired. They typically only last for 6 months and stop protecting after that period. Free software is typically limited in functionality or shows average protection capabilities. Compare test results from well known testing agencies like AV-Comparatives or VirusBulletin (VB100).
- Make regular backups of all your data.
How much would it costs to recreate all your files from zero, and could you afford losing all data? Choose your backup intervals based on that question. If you create relatively few files throughout the week and could recreate them easily in the event of an infection, conduct weekly backups. If you create new data every day that can’t be re-done at all (such as pictures, videos, patient data, etc.), do daily, or even intra-daily differential backups.
As the saying goes, an ounce of prevention is better than a pound of cure.
Have a great, malware-free day!
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trial![]()



