Decrypter for HydraCrypt and UmbreCrypt available
Our research team became aware of two new malware families being distributed via exploit kits earlier this month: HydraCrypt and UmbreCrypt. After a quick analysis it turned out that both families are closely related to the CrypBoss ransomware family whose source code leaked onto PasteBin last year. While HydraCrypt and UmbreCrypt both change some of the implementation details in the encryption scheme, the original flaw that allowed us to break CrypBoss last year allowed us to break both HydraCrypt and UmbreCrypt as well.
Unfortunately the changes made by the HydraCrypt and UmbreCrypt authors cause up to 15 bytes at the end of the file to be damaged irrecoverably. However, for most file formats the last trailing bytes are not crucial or can be repaired relatively easily by just opening and saving the files. For other file formats there may be dedicated repair and recovery tools available.
In order to determine the correct decryption key for your system, the decrypter will require some help from you. Look for any encrypted file on your system, where you have the original unencrypted version of the file as well. If you can’t find such pair of files, look for an encrypted PNG file and get any random PNG image from the internet. Select, and then drag and drop both the unencrypted and encrypted files at the same time onto the decrypter executable. If that sounds confusing, just take a look at this little animation:
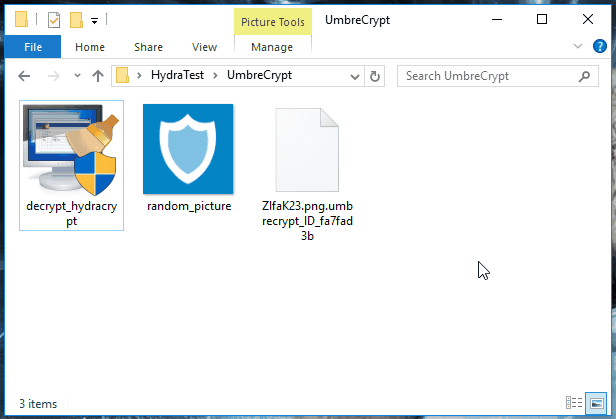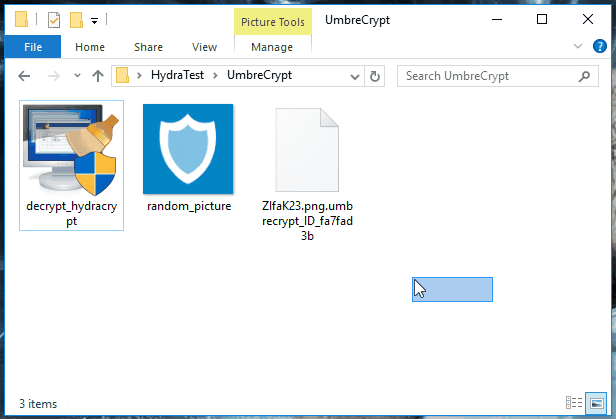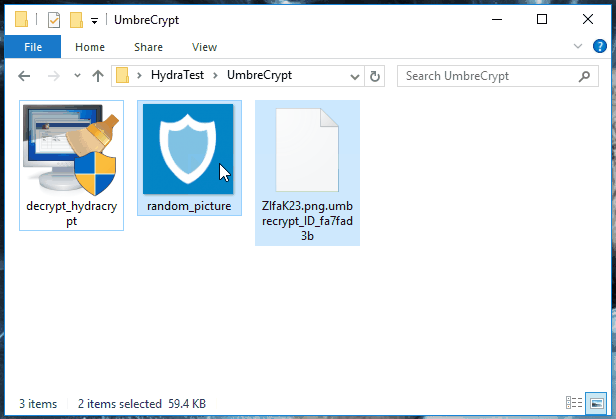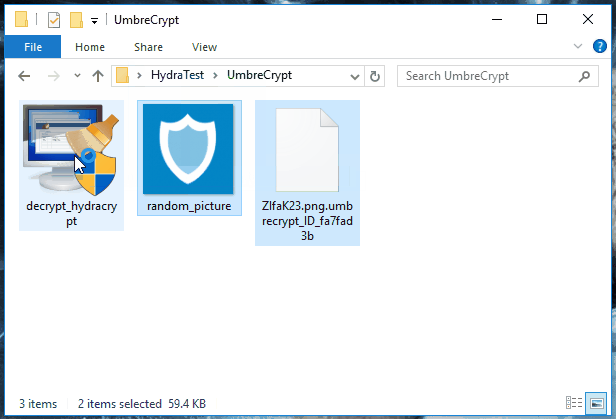
Just drag and drop either an encrypted file and its unencrypted version or an encrypted PNG file and any PNG image onto the decrypter.
The decrypter will then try to determine the encryption key for your system based on the two files you provided. This process can be rather time consuming and depending on your CPU and system can take up to several days.
Once the decryption key was determined, you will get a message like this:
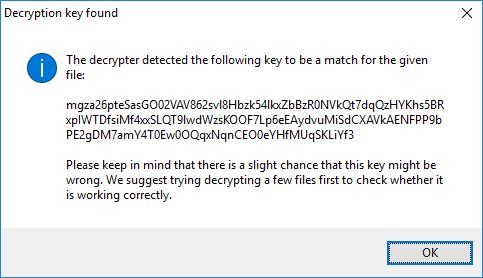
The message you receive after the decrypter determined the correct key for your system.
Just click OK and the decrypter will start up as normal. If you get an error message instead, please make sure you drag and dropped the correct files. If you did, you may have either been targeted by a completely different malware family or by a new variant that this decrypter doesn’t support yet.
All folders you add to the folder list will be decrypted recursively, which means files located in the sub-folders of the selected folder will be decrypted as well.
In any case we suggest trying to run the decrypter on a limited number of files first and manually check that those files were decrypted properly before you move to decrypt large number of files. This makes sure the decrypter figured out the correct key and may save you a lot of time in the long run in case it turns out the malware author changed the encryption algorithm in a later variant that the decrypter doesn’t support.
The malware unfortunately does not leave any information about the original file behind. That means the decrypter can’t be sure that the result of the decryption is correct. For that reason, the decrypter will not delete the encrypted files on your system just to be sure. That also means, that you need to make sure your disks have enough space before you start the decryption. If you are low on disk space and you have no way of making room either, the decrypter also has an option to delete the encrypted version of the file after it has been decrypted. We strongly discourage anyone from using that option though.
The download for our HydraCrypt and UmbreCrypt decrypter is available here:
http://emsi.at/DecryptHydraCrypt
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialIf you need help with performing the decryption on your system or if the decrypter does not work, please don’t hesitate to reach out to our technical support.


