Protecting your information with hard disk encryption – what you need to know

Ever wondered what you’d do if your laptop, tablet or smartphone was stolen? While the use of security software to protect you from online attacks is common, what about physical threats to your hardware?
Even with a password-protected operating system (OS) your data is still saved to your hard disk in an unencrypted form. Did you know that it can be accessed easily by reinstalling a new OS the over the top of the existing installation?

That’s a big problem. And a big risk to you – and probably your family and employer as well. It’s impossible to protect yourself against physical theft. But it is possible to prevent criminals from getting their hands on the information on your hard disk. This is where your work documents, personal photos and videos, even critical passwords and online banking data lives. So how do you protect your physical hard disk? The answer is by using a technology known as hard disk encryption.
What is disk encryption?
Encryption is a method of making readable information unreadable to people who shouldn’t have access to it. When you encrypt your information, it must decrypted first before it can be read.
Encryption is part of the field of cryptology, a science which deals with the deliberate scrambling of information. While the cryptographic methods of over 2000 years ago were primitive and basic – simply rearranging a few characters – today’s methods use complex mathematical algorithms.
Advanced Encryption Standard (AES) is the most frequently used algorithm, due to its speed and extremely high level of security. At present, there’s no practical way of attacking AES even though the encryption method is well known.
AES, also known as the Rijndael algorithm after its inventors, divides the information to be encrypted into 128-bit data blocks that are encoded with a key of 128, 192 or 256 bits in length. These blocks are written into a 2D table that various mathematical transformations are then applied to.
The binary data can still be read from the hard disk once it has been encrypted, but it no longer makes any sense at all. It’s not even possible to tell what was encrypted. It could be pictures, text files or executable files. Even if the encryption algorithm is known, the data can’t be decoded without having the correct key. So it will remain hidden from strangers.
Is AES secure? Testing all possible combinations (or ‘cracking the code’) of a 128-bit key would take several million years of computing time. However, thanks to modern hardware, accessing encrypted data (in conjunction with the correct key) is almost instantaneous.
In other words, you won’t notice any performance issues when your data is encrypted (while it’s being saved) and decrypted (while it’s being read or unscrambled). That’s because your computer’s CPU works much faster than your hard disk can read or write the data.
Why you should use hard disk encryption?
If someone gets physical access to your computer and you aren’t using disk encryption, they can very easily steal all of your files.
It doesn’t matter if you have a good password because an attacker can simply boot to a new operating system off of a USB stick (and bypass your password) to look at your files. Or they can remove your hard disk and put it in a different computer to gain access.
Computers have become an extension of our lives and private information continually piles up on our hard disks. Your computer probably contains work documents, photos and videos, password databases, web browser histories, and other scattered bits of information that doesn’t belong to anyone but you. You should be running full disk encryption on your computer to keep this information private.
Four good reasons why you should use hard disk encryption:
- Hard disk encryption is built in to all major operating systems.
- It’s the only way to protect your data in case your laptop gets lost or stolen.
- It takes minimal effort to get started and use.
- It makes it impossible for someone who isn’t you to access any of your files.
How does hard disk encryption work?
When you turn your computer on, before your operating system can start, you must unlock your disk by supplying the correct encryption key.
The files that make up your operating system are on your encrypted disk. So there’s no way for your computer to work with them until the disk is unlocked.
Typing in your passphrase won’t unlock the whole disk, it just unlocks an encryption key. And the encryption key then unlocks everything on the disk.
But you need to be careful using hard disk encryption that can only be unlocked with a passphrase you’ve memorized. Forget the passphrase and you’ll be locked out of your own computer forever.
Once your computer is on and you’ve entered your passphrase, your disk encryption is completely transparent. Everything works like normal. Your files open and close. Your programs or applications just work. And you won’t notice any performance impact.
Just remember that when your computer is on and unlocked, whoever’s using it has access to all your files and data. Because the encryption is now transparent.
IMPORTANT: disk encryption doesn’t make your computer ‘secure’
Disk encryption is only useful against attackers who have physical access to your computer. It doesn’t make your computer any harder to attack over a network.
All of the common ways you could become a victim of hacking still apply:
- Attackers can still trick you into installing malware.
- You can still visit malicious websites that exploit software bugs in your software, your web browser, or countless other ways.
- When you visit ‘friendly’ websites, network attackers can still secretly make them malicious by modifying or intercepting the web pages in transit.
- Attackers can still exploit services running on your computer, such as network file sharing, music playlist sharing, or torrent service, to name a few.
- And disk encryption doesn’t do anything to stop internet surveillance.
Ways to encrypt your hard disk
There are many encryption programs available, with the main differences being their level of complexity and whether they are free or paid software. Here are just some of the many options:
Bitlocker Drive Encryption (for Windows)
BitLocker is Microsoft’s disk encryption technology. It’s only included on:
- Ultimate and Enterprise editions of Windows Vista and Windows 7
- Enterprise and Pro editions of Windows 8 and 8.1
To see if BitLocker is supported on your version of Windows:
- Open Windows Explorer
- Right-click on your C-drive,
- Look for the “Turn on BitLocker” option
If you see a “Manage BitLocker” option, your disk is already encrypted.
If you’re a Windows 10 user, here’s how to turn on device encryption.
BitLocker is designed to be used with a Trusted Platform Module. This is a tamper-resistant chip built in to new PCs that can store your disk encryption key. Because BitLocker keys are stored in the TPM (by default) you’re not required to enter a passphrase when booting up.
If your computer doesn’t have a TPM (BitLocker will tell you as soon as you try enabling it), it’s possible to use BitLocker without a TPM. You can use a passphrase or USB stick instead.
If you only rely on your TPM to protect your encryption key, your disk will get automatically unlocked just by turning it on. This means an attacker who steals your computer while it’s fully powered off can simply power it on in order to extract the key.
If you want your disk encryption to be much more secure, in addition to using your TPM you should also set a PIN to unlock your disk or require inserting a USB stick on boot. This is more complicated but it provides an extra layer of security.
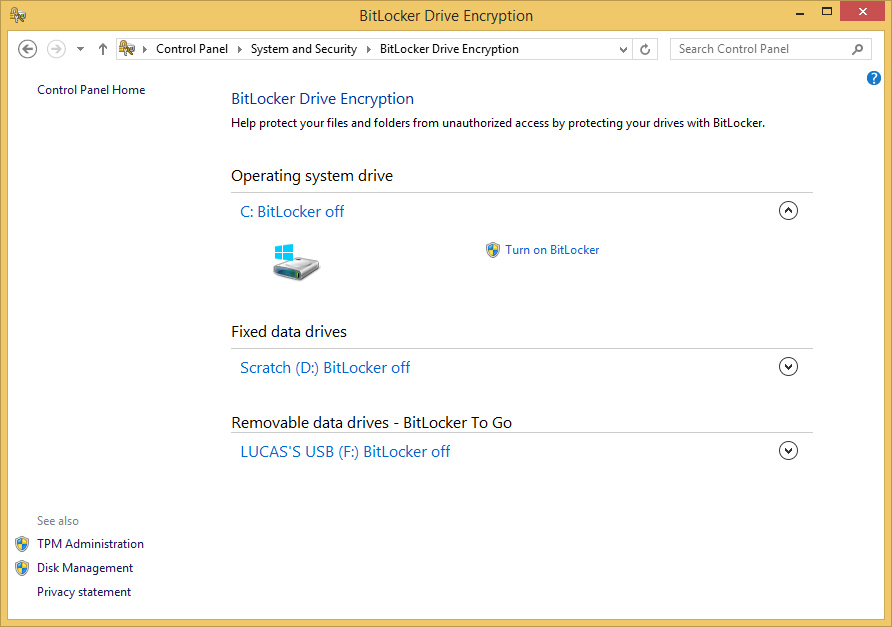
Bitlocker’s design is user-friendly and comes with advanced options. If you use one of the correct versions of Windows and don’t need additional features, Bitlocker is a solution with no further cost to you.
Steganos Safe
As the name suggests, Steganos Safe is a virtual vault to “lock” your files inside. For example, you can secure your Office documents by saving them directly to the safe. It’s easy to use and offers some special features such as the ability to hide data in images. Your data can be considered very secure thanks to the use of 384-bit Advanced Encryption Standard (AES).
Diskcryptor
DiskCryptor is open-source software which means users are free to download and modify its source code. You can also choose the encryption algorithm. DiskCryptor is ideal for beginners with a clean, simple user interface, which makes it very easy to navigate through the menus.
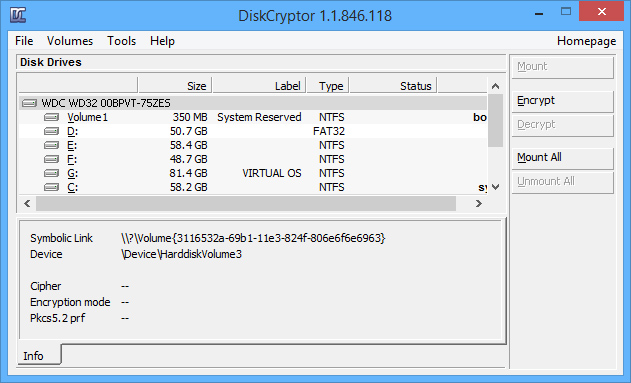
Like all good encryption programs, DiskCryptor loads before the OS. Windows will only boot if you enter the correct password, which then automatically grants you access to the data.
Understand the risks with ‘free software’ such as TrueCrypt
TrueCrypt was one of the most frequently recommended encryption programs and was used by millions of people. In May 2014, however, the security community was shocked when the software’s anonymous developers shut down the project. The homepage was replaced with a warning that “using TrueCrypt is not secure as it may contain unfixed security issues.”
TrueCrypt recently underwent a thorough security audit showing that it doesn’t have any backdoors or major security issues. Despite this, we don’t recommend using software that isn’t maintained anymore.
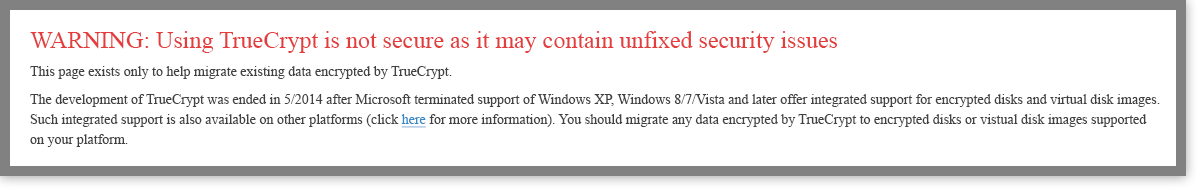
When good freeware goes bad. You can still migrate from TrueCrypt to BitLocker following the instructions on TrueCrypt’s website.
Is cloud storage the solution? Not necessarily …
If you use services like Microsoft’s OneDrive, Google Drive or Apple’s iCloud you’re using a cloud storage service. These are a great way to back-up your data but they do come with some risks:
- Your data’s still with a third-party commercial entity. You must understand their security measures and protocols before trusting them with your information.
- Cloud service providers come and go all the time. If your provider disappears will your data be lost forever or backed up somewhere trustworthy?
- Your cloud service provider might be reliable – but they’re only as reliable as your Internet connection. A poor connection may mean you’re unable to access your data when you need it most.
- Security laws vary in different countries. So you really need to understand where your information actually resides. If the physical storage of your data is in a different country, does it need to comply with your local laws and regulations? If not, what legal recourse do you have (if any) should the provider disappear or fail?
No system is perfect. And cloud storage is just the same. Minimize your risk by choosing a reputable provider and always ensuring your data is encrypted.

So much information – what’s the right thing to do?
If you’re using any computer, laptop, tablet or smartphone, you should be using hard disk encryption technology to encrypt your data and personal information.
The time and effort required is minimal. And even if you don’t feel that your data is important now, it’s possible that it could be used against you in the future. Take the time time to learn about the technology options first. It’s very important you don’t risk losing your data by configuring the encryption software incorrectly.
REMEMBER: Hard disk encryption is only designed to prevent access to your data. It’s there to protect you if someone who shouldn’t gains physical access to your device. Other network threats such as malware can still infect your computer and access your data. Even while your OS is still running!
So in addition to using hard disk encryption, we also recommend the use of proven, reliable and widely-used anti-virus software with real-time protection such as Emsisoft Anti-Malware.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trial



