Fabiansomware: when hackers lose it


Cybercrime has existed for as long as the internet has. However, 2016 has well and truly been the year of ransomware. New ransomware families are popping up weekly and the Emsisoft Malware Lab battles them daily on the frontline.
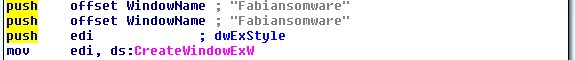
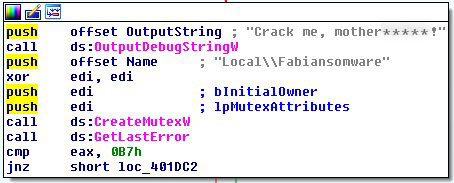
As a result, our lab is often at the receiving end of hate from authors of such ransomware. This was the case a few months ago when we were able to break the amateurish code that makes up a ransomware family known as Apocalypse. Recently, the hate has become more personal and directly focussed at Fabian, our CTO and head of Emsisoft’s Malware Research Lab. Abusive comments have been embedded directly into Apocalypse’s malware. They recently even named their most recent strain ‘Fabiansomware’ in his honour.
So, why are we being targeted?
Online, Fabian is a comical malware hunter who shares decryption tools and online security advice. At Emsisoft, he is the head of our malware lab. He and his team investigate new threats, develop new -and adapt existing- protection technologies and makes sure our users are protected from current and future malware threats.
Why it’s getting so personal
In June 2016, we published an article after the lab broke three variants of Apocalypse and shared a free decrypter to all Apocalypse victims. Since then, the lab has broken six new variants.
Currently, the malware authors are changing their malware to try to stay a step ahead of our lab and other malware hunters online. Currently, it takes us only an hour or two to break the new variant. And the insults continue.
The abuse has become so offensive we won’t share it here but it can be seen on Fabian’s twitter account.
Apocalypse’s crush on the head of our lab has become so out of control that in their newest variant, the contact email has been listed as [email protected]
Essentially, their idea is to try to blame him for the most recent strain. It has been working to some degree as can be seen in this sprightly conversation between Fabian and a very unhappy victim.
So looks like the Apocalypse degenerates decided to rename their project to Fabiansomware. They fell hard for me. pic.twitter.com/pYkXp1vEap
— Fabian Wosar (@fwosar) August 29, 2016
A bit about Apocalypse
The Apocalypse ransomware was first seen on the 9th May 2016. The main attack vector is weak passwords on insecurely configured Windows servers running the remote desktop service. This allows an attacker to use brute force to gain access and means they can easily interact with the system as if they had access in person. Abusing remote desktop has become increasingly common over the last few months, especially for running ransomware like Apocalypse.
The earliest variants install themselves to %appdata%windowsupdate.exe and create a run key called windows update to both HKEY_CURRENT_USER and HKEY_LOCAL_MACHINE. This variant uses the .encrypted extension. A ransom note is created for every file in the form of *filename*.How_To_Decrypt.txt. The [email protected]/[email protected]/[email protected]/[email protected] email addresses are used in the ransom note.
On June 9th, another version of the Apocalypse was discovered. This variant uses a different location, run key name and email address. The ransomware installs itself to %ProgramFiles%windowsupdate.exe, and creates a run key called windows update svc. The email address used in this variant is [email protected].
On June 22nd, the newest variant was discovered, which changed a lot more. Instead of using windowsupdate, it uses firefox as a name instead. The newest version installs itself to %ProgramFiles%firefox.exe, and creates a run key called firefox update checker. The new extension is “.SecureCrypted” and new name for ransom note *filename*.Contact_Here_To_Recover_Your_Files.txt. The email address used is [email protected].
Our lab continues to find and crack new strains.
What you can do
The most important line of defence is a proper password policy that is enforced for all user accounts with remote access to the system. This applies to rarely used accounts created for testing purposes or by applications as well.
Apocalypse and many other families spread via Remote Desktop Protocol (RDP). If you are a small business owner or even a large company, make sure your RDP and remote control ports are closed.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialEven better would be to disable Remote Desktop or Terminal Services completely if not required or at least to use IP address based restrictions to allow the access to these services from trusted networks only.