The Inside Joke: Ransomware hackers need attention, too


Cybercrime is on the rise in many different forms. However, 2016, the year of ransomware, has seen profits growing for new ransomware families who are popping up by the week. The Emsisoft Malware Lab battles them daily on the frontline and our security researchers are often contacted by malware developers to mock, taunt and even congratulate them on their ability to crack hacker’s software. But it is quite a different thing for a malware developer to contact us to sell decryption keys.
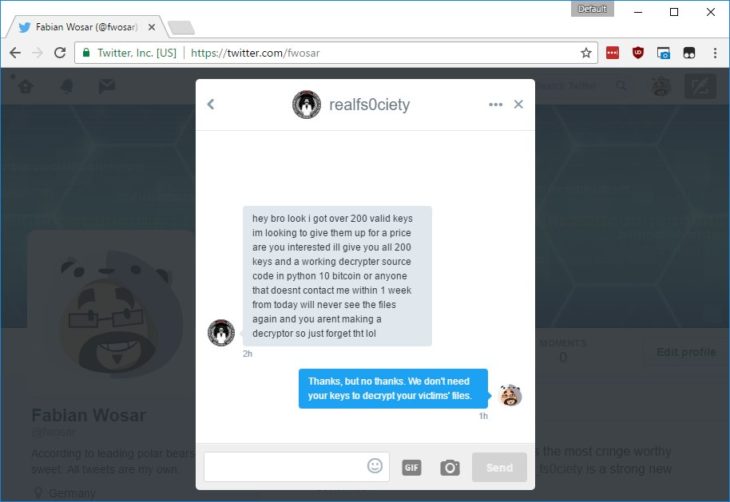
For some time, Security researcher and Chief Technology Officer at Emsisoft, Fabian Wosar has been collecting decrypter keys for fs0ciety’s ransomware. So when an fs0ciety developer got in touch and tried to sell him 200 decrypter keys for 10 bitcoins, the only result was a rather comical exchange on twitter.
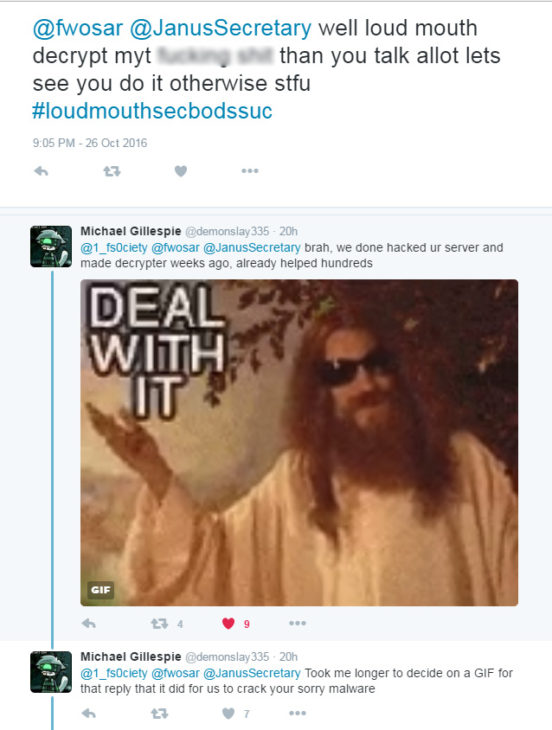
Bleeping Computer reports that Fabian Wosar and Michael Gillespie have been using their collected keys to decrypt victim’s files for free.
“This has been done secretly through BleepingComputer’s Fsociety Locker Ransomware Help and Support Topic, Twitter, Emsisoft’s site, and other forums or support sites.”
While the weakness that the malware contains can’t be revealed, it is estimated that in total “Fabian had collected 11,366 keys before the ransomware developer suspended operation.”
The Emsisoft Lab also work in conjunction with Michael Gillespie from the Malware Hunter Team. He is the creator of ID Ransomware, a website that will help you to figure out what kind of ransomware you have been infected with based on the specific signatures that can be found in the ransom note you receive. In a recent interview, he walked us through the process of identifying ransomware families and revealed how various techniques can be used to identify ransomware such as by the filename of the ransom note, certain known email addresses or BitCoin addresses in the note, the pattern of the encrypted file’s name (e.g. a certain added extension), and even some hex patterns that some ransomware leave in the files. Once a strain has been identified, weaknesses can be explored and free decryption offered to users who have been targeted.
When a hacker’s ransomware is no longer threatening, it loses momentum. Like any profitable business, hackers need customers. In an online market, lack of press or a reputation of poor quality will see a malware developer disappear almost instantly until they have a new strain worthy of release.
As a result of our history of cracking such strains, this is not the first time that Fabian has been the target of malware developers. Recently, he had his own strain named after him after he repeatedly cracked the ransomware of the Apocalypse family.
Coming to security researchers directly, such as in this case, aside from an obvious call for attention, almost demonstrates delusion. “We are so smart and scary that only we can offer the solution to the problem we have created.” Luckily, this has rarely been the case. The tireless work of the Emsisoft Lab, good guys such as Michael Gillespie at MalwareHunterTeam – and the free tools they offer – mean solutions are never far away.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialHave a nice (malware-free) day!