Hacked abandoned webservers: The invisible helpers for malware authors


You’ve been working in the same job for 5 years, feeling undervalued and overworked. To kill the boredom, you start visiting job sites in your spare time to see if maybe the grass is greener somewhere else. You search for your dream role and as the search results appear, you see a popup to a recruitment firm offering your exact role. You click on the link and are taken to a third party site. BAM! Your computer is crawling with malware.
The site you were led to may have once been a legitimate recruitment site or someone’s blog, but it has been hacked and worst of all, when you contact the administrator of the site to let them know their site is injecting malware, there is no response.
Forcepoint describes an attack that takes this shocking scenario one step further:
“The injection hijacks visitors to the compromised sites and redirects them to rogue anti-virus sites that attempt to trick them into downloading and installing a Trojan onto their computer.”
In this example you play an active role in downloading the malware simply because you thought you had found a way to remove the malware!
So how does it work?
Abandoned websites are sites that have been left unattended by their owners
Just as it sounds, a website that has been abandoned isn’t tended to at all, or, the company/individual who owns the site doesn’t have proper contact information. When the site gets hacked, there is no one to contact to have the site cleaned. These sites then deliver malware to visitors without any knowledge or control over what is happening. The only option for someone who has found malware on an abandoned site is to contact the web host directly to take it down, which won’t always work as seen in the below image. Michael Gillespie, a security researcher for MalwareHunterTeam, sent us pages and pages of attempts to alert abandoned site admins that their sites were injecting ransomware and other malware, all of which received a vague or no response. Professional security researchers spend hours trying to remove these sites, meaning an everyday user has very little chance of having the issue resolved. The responsibility must lie with the site administrator.
Since these admins don’t tend to their websites, it is fair to assume they usually operate on an outdated Content Management System (e.g. older Drupal, WordPress, etc.), outdated plugins, or even just plain bad configuration of the web server. This is what makes abandoned sites the perfect host for URL injection.
The Google Search Console defines URL injection for admins as follows:
“This means a hacker has created new pages on your site, often containing spammy words or links. Sometimes these new pages contain code that does things you didn’t intend, such as redirecting your users to other sites or making your webserver participate in a denial-of-service attack against other sites.”
Abandoned sites look like every other site
The biggest issue with abandoned sites is that most of the time they can be legitimate! Such as a small business, for example, or someone’s blog. Some sites even deliver exploit kits that can download ransomware which will lock up your files until you agree to pay a cyber criminal to have them released, or they may just be hosting the malicious files, where another hacked or malicious site redirects the victim to download from.
Though it is difficult to always figure out how, a number of websites on the WordPress content management system (CMS) have been hacked to deliver ransomware and other malware using this exact method.
Admins: You are responsible and should always aim to prevent attacks
An attacker will attempt to use any or all of these methods to take advantage of your site:
- Creates a malicious website of their own that your website diverts visitors to.
- Exploits a vulnerability on your web server or in its configuration such as weaknesses in your outdated CMS.
- Gains entry via a vulnerability in the applications your website relies on, such as Twitter, Facebook or Instagram widgets.
An obvious clue that your site has been hacked is random folders in your FTP account. You may also receive an alert from Google that a potential customer was infected with malware when visiting your site. When you log into your FTP account, there may be thousands of randomly-named folders just sitting there – each one with a full website that an attacker was spoofing.
This poses another threat; that an attacker will hijack your site just to host a whole other website. This could be a phishing site for bank credentials for instance, or spoofing another company to possibly hit or abuse their reputation or to act as a hosting page for ransomware victims to make their payment.
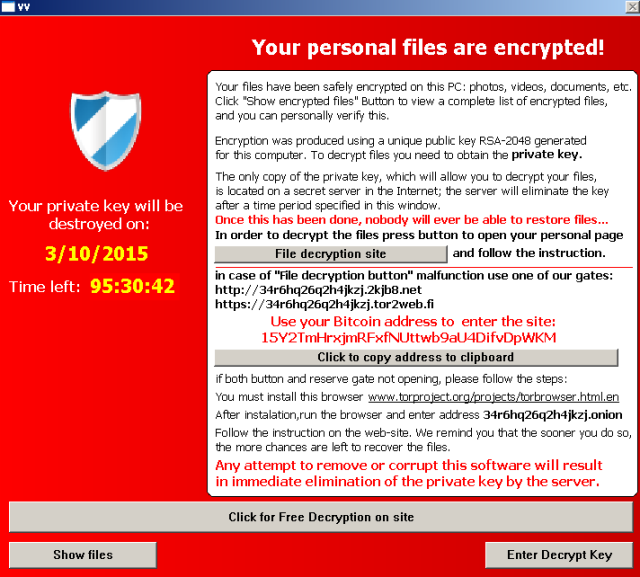
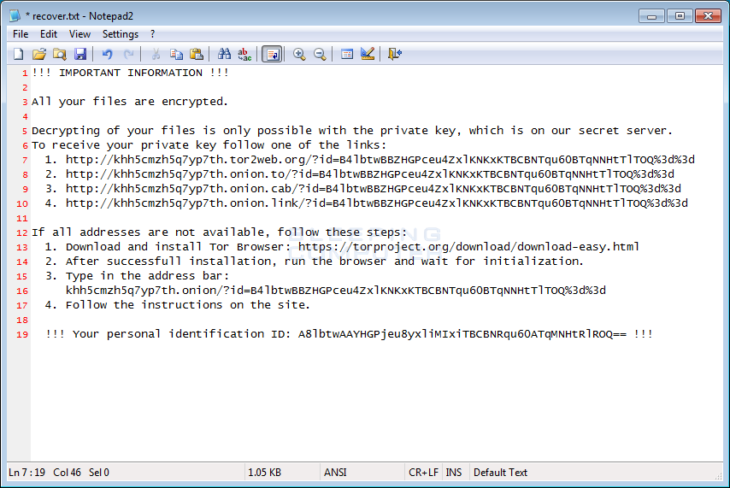
Nemucod injects ransomware and hosts ransom payment pages
A real world example of a common attack was Nemucod. This malware family hacks websites, adds a folder to the FTP (usually named counter), and uses that site as the website to host not only the malware that gets downloaded to infect victims (drops their own weak ransomware, and the Kovter banking Trojan typically), but also hosts the “payment portal”, where the victim then goes to get the decrypter if they chose to pay. Essentially, the site you have been ignoring is being used to exploit victims and without your intervention this can go on for months.
Though these sites get taken down constantly, the attackers just add 5 domains to the initial malware (technically the Nemucod dropper), and it checks for one of those 5 that is actually still up to pull the malware files from. They then change it up with 5 more for the next version at random. Nemucod has been active since early 2015 and Michael Gillespie, security researcher at MalwareHunterTeam, says that his ID Ransomware tool is still seeing submissions of it today!
If you have been infected by Nemucod or any other family of ransomware we have your back with our list of decrypters.
A tip for Admins to keep malware out of their site
Always, always, always keep website software (CMS, plugins, themes, etc.) up to date, and passwords strong for anything like FTP and cPanel that allows access to your site.
Users can avoid infection if surfing with caution
Use common sense when you’re online. If you are being redirected to unrelated sites, close your browser and run your anti-malware software. Protect your computer with a quality anti-malware program that includes web protection. Web protection ensures you are alerted if you unintentionally reach a site that injects trojans or other malware and prevents you from connecting.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialHave a great (malware-free) day!