Emsisoft Releases Free Decrypter for Globe3 Ransomware

Today, Emsisoft CTO/researcher Fabian Wosar released a new version of the Emsisoft Globe Ransomware Decrypter that can recover files locked by the latest version of this threat that made its presence felt for the first time during the summer of 2016.
Version 2, also referred to as Globe2, appeared two months later, in October, but both versions were no match for Emsisoft’s team, who released free decrypters for both variants shortly after Globe and Globe2 started hitting users.
Around New Year, the Emsisoft Lab team was alerted to the presence of a new Globe variant, Globe3, which was infecting users using a new mode of operation.
Globe3 samples created using ransomware building kit
Just like the two previous Globe versions, Globe3 ransomware binaries were put together using a “builder,” a term that describes a software application which automates the process of customising a malware executable.
The Globe actors are using this builder to tweak various settings in Globe3’s behaviour, customising ransomware binaries depending on the targets they want to infect, altering ransom demands to larger sums in case they infect enterprises or using different Bitcoin addresses per different spam campaigns.
Because all Globe3 binaries included a configuration file, it was easy to determine what were some of the features available in the recent version of the Globe ransomware builder. [A sample Globe3 configuration file is available here.]
- [MELT] – Causes the ransomware to delete the file it originally executed from after successful infection
- [TASKNAME] – Ransomware process name
- [AUTOEXEC] – Instructs the ransomware to establish persistence
- [PROFILE] – Causes the ransomware to encrypt the user profile first
- [DRIVES] – Instructs the ransomware to encrypt all connected drives
- [SHARES] – Triggers the ransomware to search for and encrypt network shares
- [NAMES] – The ransomware will also encrypt the file names, hiding the original file names
- [EXTENSION] – The file extension to append to the file name of encrypted files
- [TARGETS] – List of file types to target during the encryption process
- [MESSAGE] – Ransom note (supports HTML code). Here is where crooks will also control the Bitcoin address and ransom demand value.
- [N] and [E] – RSA key parameters used by the ransomware to encrypt the AES key
- In addition there are options to allow the attacker to configure the wallpaper as well as the ransom note name
As you can see, the builder allows individuals with access to the builder to produce extremely varied Globe3 variants.
At the time of writing, based on information gathered by the Emsisoft team, users can recognise Globe3 infections by the two most commonly used extensions appended at the end of files, which are .decrypt2017 and .hnumkhotep.
Nevertheless, users that want to be sure they’ve been hit by a Globe3 variant can use the ID-Ransomware or Crypto Sheriff services, just to be sure.
The ransom note dropped by Globe3 is usually called “How To Recover Encrypted Files.hta” and an example can be found below.
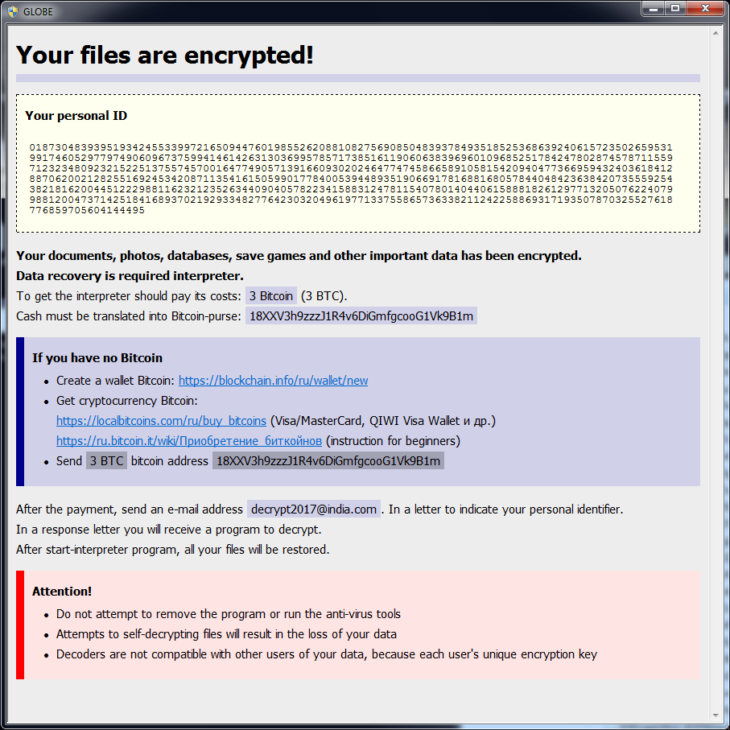
The biggest change to the previous two Globe versions is at the level of encryption operations. While the first Globe variant used the Blowfish encryption algorithm to lock files, and Globe2 used RC4 and RC4 + XOR, Globe3 relies on AES-256, a powerful symmetric encryption algorithm.
We won’t reveal how our Lab Team found a way to recover Globe3 encrypted files, but the decrypter released today supports all possible variants that can be produced by the Globe3 builder.
Nevertheless, due to a bug in the ransomware, decrypted files smaller than 64kb will be up to 15 bytes larger than the originals. This file size increase is due to the fact, that the ransomware rounds file sizes up to the next 16-byte boundary without saving the original file size.
For most file formats this is unlikely to cause problems. However, if applications show errors about corrupted file formats, users may have to manually remove trailing zero bytes at the end of the recovered file using a hex editor.
Users affected by Globe3 can download the free decrypter from here. The decrypters for Globe and Globe2 are also available, just in case anyone still has files encrypted by those versions, even if they’re not actively distributed anymore.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialThis blog post is based on the Globe3 ransomware sample with the following SHA-256 hash: f2e0199eb54e3e51cd8ff11aa5b1ae0ef823cfd7b91e24d27c6bafa38c86cae0.


