Women in science: cyber security and the gender gap

Like many writers, my passion for words built up slowly and then all at once. Science also appealed to me but not in such a way that I ever considered it as a career option. My desire to study writing drove every thought I’d ever had about my future, but much like science, I was convinced this was another path that would see no fruitful outcome.
Fast forward 12 years and many other jobs later, I work as a tech writer for Emsisoft.
Every day in this role has been a learning experience. Malware research has captured my imagination during my time at Emsisoft. As I now consider pursuing a career in this field, I’m faced with a question:
Am I crazy for looking to expand my role within a field that is notorious for its absence of women?
Despite progress and well-publicized intentions by big tech companies, recent revelations do not paint a pretty picture. Google is being investigated for extreme gender pay discrimination by the US Department of Labor Women make up 31% of Google’s workforce.
Uber is in the spotlight for workplace discrimination after an engineer went public with her experience working for the start-up. “When I joined Uber, the organization I was part of was over 25% women. By the time I was trying to transfer to another engineering organization, this number had dropped down to less than 6%.”
Is this an industry I really want to struggle to get into?
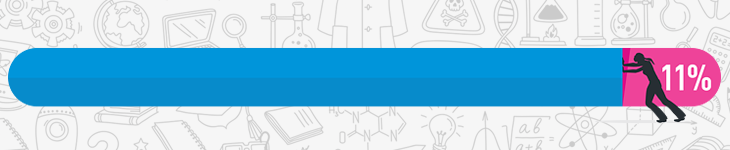
The cyber security industry specifically is made up of only 11% women. Why are there so few of us? What is it really like to work in a lab where women are so heavily outnumbered?
For this Earth Day in support of March for Science, I decided to sit down with Elise and Sarah – two women making their mark in the Emsisoft Malware Lab – to talk about how to become a security researcher and their take on the gender gap. What does this job actually look like? How have they been impacted by discrimination?
Hi guys. Thanks for taking the time to talk to me about your jobs and what it means to be a woman in tech. So before we talk about the role of women, I’m sure our readers are just as excited to know more about how you became a security researcher.
E: I didn’t really set out to become one, it happened after I got involved in malware and its removal and found out how interesting the entire subject was. I was a volunteer malware remover a few years before starting in malware research. When you do that and you want to keep up, you have to learn more about malware, see for yourself what it does, see what it does to protect itself (for example to make removal more difficult) which made me slowly angle towards malware research and all along I really liked what I did, so in a sense I was lucky and was able to make from my hobby my work. It really takes time and what I’d call “fiddling around” (try different approaches, learn new concepts and learn a lot about security and computing principles.
S: Similar to Elise, I originally joined the Bleeping Computer training course where Elise was an admin, as I was interested in the idea of malware. Before that I wanted to be a programmer because of my love of video games, but after hearing more about what Elise did and learning more about malware I became more interested in analysing malware as a job. The thing that really took off for me was reading the Bleeping Computer thread about cryptolocker, which was new at the time. I later became involved with Fabian’s ransomware work, and that’s how I got started, I guess.
What particular skills or talents are most essential to be effective as a researcher? How did you learn these skills? Any formal training programs? Sarah you mentioned Bleeping.
E: I think the most important “skills” any security researcher needs are an affinity to malware (not to its purpose, but to the way it works), tenacity and a bit of “out-of-the-box” thinking.
S: I would say the ability to problem solve, as well as the ability to adapt. Good knowledge of the subject and the operating system is pretty essential. Being able to adapt really important as you may have to learn a new tool, and malware is constantly adapting. Problem solving is important too as dealing with malware is not always simple, sometimes things crash and you have to find ways around it.
E: And yes, flexibility, you need to be able and willing to learn new things on a (very) regular basis.
S: You don’t necessarily need to know everything coming into the industry, either.
E: Also, something that is not always mentioned: the ability to work together; I think a researcher should always look around and work with others to approach a certain issue. That way you can share knowledge and find better solutions.
S: Oh yes, sharing knowledge is quite common and often necessary.
E: It’s one of the nicest trends I’ve noticed in malware research the past years (mostly due to ransomware).
Is that across organisations as well as within teams?
S: Definitely, I’m in a collaboration group about ransomware which has people from different security companies, as well as independent individuals. We don’t necessarily share our technology but if you don’t share research, you miss out on a lot you wouldn’t see otherwise.
E: It also makes sense. For example, if 5 security companies all work on a free decrypter for one piece of ransomware they waste a lot of time. If a few people from various companies share information and one comes with a decrypter, the others can work on something else (because you only need one working decrypter in the end, not five).
S: Yeah, I wish that was the case more often. One example is that when the keys for Crysis ransomware were released, I think about 4 or 5 different decrypters were made. We decided not to when Kaspersky originally made the first decrypter since it simply made no sense when we could spend time on a decrypter for a ransomware without one. We work with Michael (Michael Gillespie at Malware Hunter Team) to make sure we don’t double up on decrypters.
E: That’s very true.
So with that in mind, what does a typical day look like for you? Do you tend to work more as a team across an entire day? or independently?
E: Oh, I have plenty of routine stuff I do every day that is done independently. For example, processing new samples that we receive, handling false-positive requests. Verifying if new malware is adequately blocked, things like that. I think most of my time is spent independently, but at the same time it’s also teamwork (for example; Arief and I do these things mostly together but during different times of the day, so I pick up when he leaves and vice versa).
How are you made aware of new malware?
E: There are various ways really. You can spot it in submitted samples, you can encounter it on social media/forums where people report encountering it (they can be computer users, technicians who encountered it, or just enthusiasts). This is also where collaborations like the one Sarah mentioned are efficient.
How do your roles differ?
S: I work part time as I’m currently still in education, but also my role is slightly different. I work closely with Fabian on ransomware, so that we can see what needs looking into, whether a ransomware is decryptable and if so, working on a decrypter if we know there are victims. I also spend a lot more time working with other researchers, as I mentioned, so we can help users who have been hit with ransomware.
I guess that comes back to having people working across different areas for efficiency. If you were all focussed on ransomware or only samples, things would get missed.
E: Yes, also, verifying if one particular ransomware variant can be decrypted takes quite some time.
Is it a 24/7 job do you think? Do you both still do research outside of work hours? Elise you mentioned it was a hobby. Has it remained one?
E: Yes, it definitely has remained a hobby. It’s not a 24/7 job, but I do have the tendency to want to try to remain up to speed with what is happening. I still volunteer in the online malware removal community (mainly at Bleeping Computer) aside from what I do at Emsisoft. On the other hand, I also have a personal life so I also think it’s important to have some (time) limits in place.
Being part of a remote team must make that difficult?
E: Yes, I guess it’s a personal thing, but you need to make sure you’re not spending all your time in front of a computer.
Speaking of computers, what does your desk look like? E.g. what equipment are you using, how many screens do you have, etc.?
E: I like a tidy work space, but I only work using a PC (sometimes a mobile device for quick messages, but nothing more than that). I only use one screen (which might be a bit of an exception) and I think a reasonably equipped PC with plenty of resources and disk space.
Desktop?
E: Yes, I like custom builds.
S: I have both a laptop and desktop, since the desktop is more powerful I use that for my VMs (Virtual Machines). But a lot of research is also done on my laptop.
What do you consider success as a security researcher? What does a win look like for you or your team?
E: 100% malware prevention.
S: Good test results help. But also user feedback. Hearing that you helped saved someone’s files is always nice and reminds you of why you do it.
E: User feedback is amazing.
Let’s switch gears. A recent study revealed that more than half of women in the cybersecurity industry have experienced some form of discrimination throughout their careers from their male peers. Tell me about an experience you have had.
E: At Emsisoft: none. Recently someone complained about being helped by a woman though.
How did that make you feel?
E: To be honest, I had a good laugh at that. If they really do think that, it’s their loss, not mine.
Gender inequality is an ongoing issue in tech-related fields. Have you ever had an experience like that one from a peer? Sarah?
S: Not from Emsisoft and in general I’ve had a good experience, however I haven’t been around that long. I know from social media that a lot of women have had bad experiences.
E: I can’t remember having encountered this in the years that I’ve been a volunteer either but yes, it does happen unfortunately.
Do you feel that the discrimination is an unconscious bias?
E: That depends on the discriminator I guess. If someone has worked in security for years and only with men, they may unconsciously assume men are just better at it.
S: Hmm, interesting question. In some cases, it may be. In most cases, the person is just usually a bad person, or badly misinformed (not that it makes it right).
You both make good points. And I do wonder for example, females account for just 11% of all cybersecurity professionals. So if men have only worked with men there is that idea that they must just be better at it. Why do you think there is such a gender gap in this industry? (Even among tech writers there’s a huge gap.)
E: I think that might even start with education, where computer-related studies are more a guy-thing.
S: I think it’s people’s ideas about computer science, and I think girls growing up may have the idea that it’s more a boy thing to do.
E: Cultural maybe? Thinking about this, I don’t know that many women who are interested in cyber security (outside Emsisoft or the online anti-malware community). Maybe it’s just more cool for guys to be interested in it than it is for women.
I think women are just as influenced by other women in pursuing other activities.
S: That’s very true. In certain STEM subjects, [sic] numbers of women are a lot higher, so it’s not that women just don’t like science. It’s a problem with multiple correct answers as to why computer science doesn’t attract so many women. In my computer science class, I was the only girl. We did have another class and that had two other girls. I think about 30 – 40 guys though.
What do you think needs to change to attract more women to STEM and computer science jobs?
E: That’s a difficult one. When looking for further education, don’t let yourself be discouraged by the men/women ratio in whatever study you think you’d like.
S: I think just making people more aware of women in the industry.
Tell me about your first mentor in cyber security?
S: Technically I would say the Bleeping Computer instructor staff were mentors. A wide range of ages and backgrounds. I liked interacting and learning from multiple different people.
E: Yes, I also did not have one real first mentor, I’ve learned a lot from a number of people over the years.
S: You could say Fabian is my mentor though, as often I’ll ask him a question and he’ll take the time to explain it to me in detail so I understand. I’m able to bother him with my random questions whenever.
Editor’s note: Fabian Wosar is Emsisoft CTO and the head of Emsisoft Malware Lab. He is a recognised and well-respected ransomware expert.
E: Yes, he’s very good at explaining things.
Lastly, any advice for readers wondering how to become a security researcher or learn more about malware?
S: Read, read, read. Keep up to date with security news, read security blogs.
E: Enjoy what you’re doing, don’t force yourself to hurry towards that one goal, but enjoy the way that leads to it and never stop learning.
S: If you’re specifically looking to get into malware analysis, I suggest looking up reverse engineering courses and videos too. I like MalwareAnalysisForHedgehogs, who happens to be a friend of mine and we did some videos talking about malware analysis with Fabian, as he covers different techniques and specific parts.
Never stop learning – 100% this.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialHave a nice Earth Day!