Jaff ransomware: The new Locky?


Ransomware continues to be a growing security threat, with new families cropping up every week. Emsisoft researchers are often involved in the discovery and analysis of new threats, and this ransomware is no different. Originally spotted earlier today, Jaff ransomware caught our attention due to it being spread via the Necurs botnet, which before spread ransomware such as Locky, and already having a large number of submissions to ID-Ransomware.
The payment page that Jaff presents is very reminiscent of Locky’s, but despite this, they share little similarities:
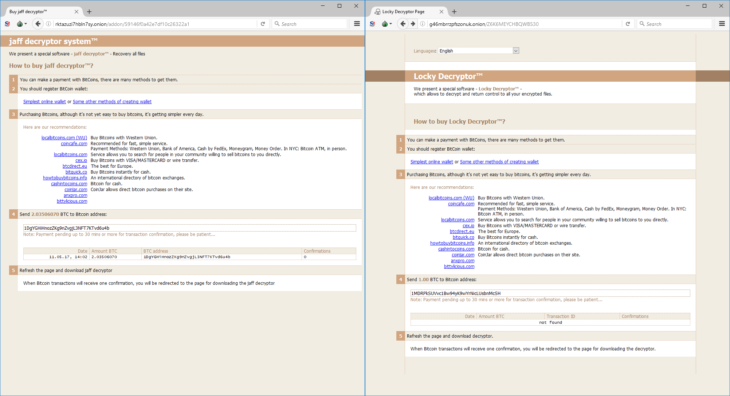
Comparison of payment pages: Jaff ransomware (left) versus Locky (right)
While the last Locky variants consist of almost 800 different functions, the Jaff code consists of only about 50, making Jaff a lot less feature complete and sophisticated.
Meet Jaff ransomware
Jaff is written in C and is packed using a custom malware obfuscator. Obfuscators are tools that are used by malware authors to hide malware underneath potentially multiple layers of encryption and compression in order to make their analysis more difficult.
Like most ransomware families, Jaff renames the files it encrypts, adding the .jaff extension. When infecting a system, it drops HTML-based, text-based and picture-based ransom notes named ReadMe.htm, ReadMe.txt and ReadMe.bmp, respectively:
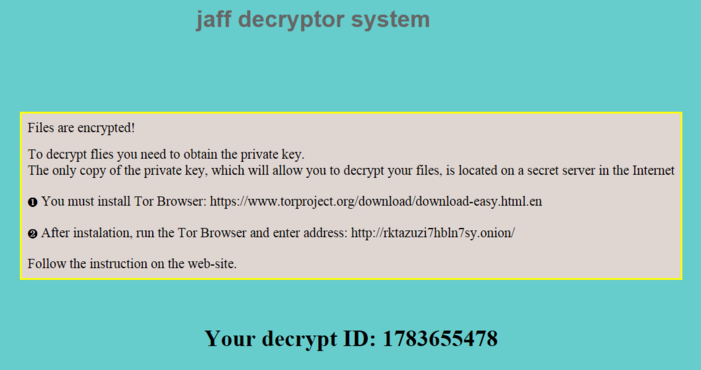
The ransom note Jaff displayed after successful encryption of a system
Jaff only contains English ransom note texts at the moment. Current versions ask for a ransom of about 2.036 bitcoins, which is currently worth around 3500 Euros, 3800 US Dollars or 3000 British Pounds.
How does a user get infected with Jaff ransomware?
Jaff is spread via the Necurs downloader/botnet. Previously Necurs was used to distribute Dridex and Locky, which led many researchers to believe that Jaff may be an evolution of the Locky ransomware. However, after analyzing both Locky and Jaff it can be concluded that Jaff ransomware is a completely different and much less sophisticated ransomware family.
At present, Necurs is targeting users via emails with one of following the subjects:
- Scan_<numbers>
- File_<numbers>
- PDF_<numbers>
- Document_<numbers>
- Copy_<numbers>
The emails contain a PDF document as an attachment and ask the user to open the embedded document-macro (DOCM) file embedded within the PDF document:
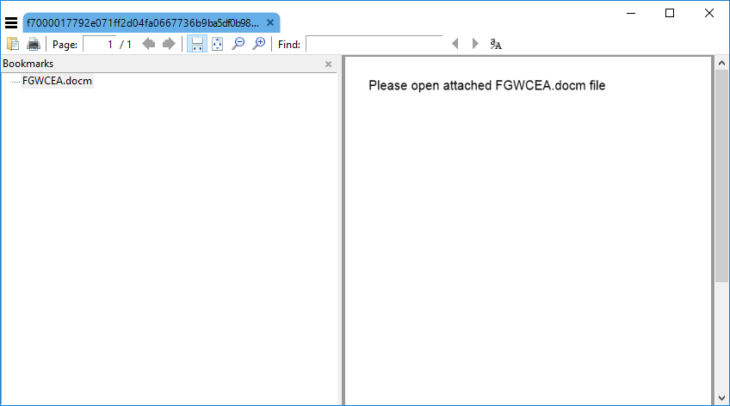
Necurs PDF document containing the Macro dropper and requesting the user to open it
If the user chooses to open the DOCM file, it will then prompt the user to “Enable Content” in order to view the document properly:
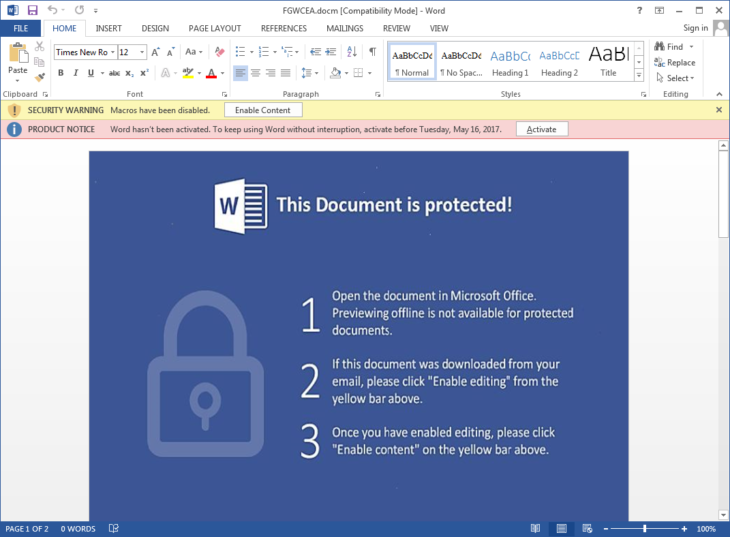
Necurs employs social engineering techniques to tempt the user into enabling macros.
If the user clicks the “Enable Content” button, the malicious macro contained inside the document becomes active and starts executing. The macro will contact its command and control server and downloads various other XOR encoded executable files, that it then decodes and executes on the user’s system.
Jaff ransomware: Key generation and encryption
Jaff uses a mix of RSA and AES to encrypt the user’s data. To facilitate encryption on a system, the Windows CryptoAPI is used. When Jaff arrives on a system, it will first import the malware author’s public RSA key. Once the malware author’s public RSA key has been successfully imported, the malware continues by creating a new 256 bit AES key.
The ransomware then searches all available drives and network shares for files with one of the following extensions:
.xlsx, .acd, .pdf, .pfx, .crt, .der, .cad, .dwg, .MPEG, .rar, .veg, .zip, .txt, .jpg, .doc, .wbk, .mdb, .vcf, .docx, .ics, .vsc, .mdf, .dsr, .mdi, .msg, .xls, .ppt, .pps, .obd, .mpd, .dot, .xlt, .pot, .obt, .htm, .html, .mix, .pub, .vsd, .png, .ico, .rtf, .odt, .3dm, .3ds, .dxf, .max, .obj, .7z, .cbr, .deb, .gz, .rpm, .sitx, .tar, .tar.gz, .zipx, .aif, .iff, .m3u, .m4a, .mid, .key, .vib, .stl, .psd, .ova, .xmod, .wda, .prn, .zpf, .swm, .xml, .xlsm, .par, .tib, .waw, .001, .002, 003., .004, .005, .006, .007, .008, .009, .010, .contact, .dbx, .jnt, .mapimail, .oab, .ods, .ppsm, .pptm, .prf, .pst, .wab, .1cd, .3g2, .7ZIP, .accdb, .aoi, .asf, .asp., aspx, .asx, .avi, .bak, .cer, .cfg, .class, .config, .css, .csv, .db, .dds, .fif, .flv, .idx, .js, .kwm, .laccdb, .idf, .lit, .mbx, .md, .mlb, .mov, .mp3, .mp4, .mpg, .pages, .php, .pwm, .rm, .safe, .sav, .save, .sql, .srt, .swf, .thm, .vob, .wav, .wma, .wmv, .xlsb, .aac, .ai, .arw, .c, .cdr, .cls, .cpi, .cpp, .cs, .db3, .docm, .dotm, .dotx, .drw, .dxb, .eps, .fla, .flac, .fxg, .java, .m, .m4v, .pcd, .pct, .pl, .potm, .potx, .ppam, .ppsx, .ps, .pspimage, .r3d, .rw2, .sldm, .sldx, .svg, .tga, .wps, .xla, .xlam, .xlm, .xltm, .xltx, .xlw, .act, .adp, .al, .bkp, .blend, .cdf, .cdx, .cgm, .cr2, .dac, .dbf, .dcr, .ddd, .design, .dtd, .fdb, .fff, .fpx, .h, .iif, .indd, .jpeg, .mos, .nd, .nsd, .nsf, .nsg, .nsh, .odc, .odp, .oil, .pas, .pat, .pef, .ptx, .qbb, .qbm, .sas7bdat, .say, .st4, .st6, .stc, .sxc, .sxw, .tlg, .wad, .xlk, .aiff, .bin, .bmp, .cmt, .dat, .dit, .edb, .flvv, .gif, .groups, .hdd, .hpp, .log, .m2ts, .m4p, .mkv, .ndf, .nvram, .ogg, .ost, .pab, .pdb, .pif, .qed, .qcow, .qcow2, .rvt, .st7, .stm, .vbox, .vdi, .vhd, .vhdx, .vmdk, .vmsd, .vmx, .vmxf, .3fr, .3pr, .ab4, .accde, .accdt, .ach, .acr, .adb, .srw, .st5, .st8, .std, .sti, .stw, .stx, .sxd, .sxg, .sxi, .sxm, .tex, .wallet, .wb2, .wp, .x11, .x3f, .xis, .ycbcra, .qbw, .qbx, .qby, .raf, .rat, .raw, .rdb, rwl, .rwz, .s3db, .sd0, .sda, .sdf, .sqlite, .sqlite3, .sqlitedb, .sr, .srf, .oth, .otp, .ots, .ott, .p12, .p7b, .p7c, .pdd, .pem, .plus_muhd, .plc, .pptx, .psafe3, .py, .qba, .qbr.myd, .ndd, .nef, .nk, .nop, .nrw, .ns2, .ns3, .ns4, .nwb, .nx2, .nxl, .nyf, .odb, .odf, .odg, .odm, .ord, .otg, .ibz, .iiq, .incpas, .jpe, .kc2, .kdbx, .kdc, .kpdx, .lua, .mdc, .mef, .mfw, .mmw, .mny, .moneywell, .mrw.des, .dgc, .djvu, .dng, .drf, .dxg, .eml, .erbsql, .erd, .exf, .ffd, .fh, .fhd, .gray, .grey, .gry, .hbk, .ibank, .ibd, .cdr4, .cdr5, .cdr6, .cdrw, .ce1, .ce2, .cib, .craw, .crw, .csh, .csl, .db_journal, .dc2, .dcs, .ddoc, .ddrw, .ads, .agdl, .ait, .apj, .asm, .awg, .back, .backup, .backupdb, .bank, .bay, .bdb, .bgt, .bik, .bpw, .cdr3, .as4
Once a file matching one of those extensions has been found, the malware will encrypt up to the first 512 KB using the 256 bit AES key in CBC mode. It will then encrypt the AES key using the malware author’s public RSA key and stores it together with a magic header value, the size of the encrypted block and the encrypted bytes inside a new file. Last but not least it appends any non-encrypted data to the file.
This procedure may look convoluted at first but essentially allows the malware author to operate without the need of a command and control server that the malware would have to talk to during infection and that could be taken down. This means that Jaff can and does encrypt files without an internet connection.
Unfortunately, after evaluating the way Jaff performs its encryption, there is no way to restore encrypted files without access to the malware author’s private key. However, due to some oversights by the ransomware authors, it may be possible to restore some files via other means.
You can contact us via email for more information.
How can I protect myself from Jaff ransomware?
As explained in our ransomware article, the best protection still remains a reliable and proven backup strategy, especially since the encryption used by Jaff is secure and the only way to get the data back is through the help of the ransomware author or via restoring from backups.
Apart from regular backups, you will be glad to hear that the Behavior Blocker technology used by Emsisoft Anti-Malware has proven to be the next best defence, as it catches Jaff ransomware before it can encrypt any files and thus once again keeps our users protected from this and hundreds of other ransomware families without the need for signatures or updates:
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trial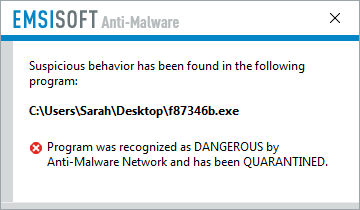
Jaff ransomware being blocked by the Emsisoft Behavior Blocker.
We consider ransomware one of the biggest present threats and plan to do our best to continue our excellent track record, to keep our users as protected as possible.


