Spotlight on ransomware: Ransomware payment methods

Cybercriminals are getting more brazen, demanding bigger and bigger ransoms to decrypt the files they’ve hijacked – and it’s possible we could see demands from cyber criminals grow even more outrageous in years ahead. The average ransom amount increased from $294 in 2015 to a whopping $1,077 in 2016, according to figures collated in a recent internet security report. The malware has also become more diverse, with the number of ransomware families more than tripling (from 30 to 101) between 2015 and 2016.
Ransomware has never been more lucrative, but what exactly is making it so easy for cybercriminals to cash in on unsuspecting users?
Well, to further encourage victims to fork over the ransom, the payment gateways supporting ransomware have continued to become more advanced, almost rivaling modern online business websites in their professional design and sophisticated functionality. Spora is perhaps the best example of such a payment mechanism, with the ransomware featuring a polished interface, a variety of recovery packages and a chat box where you can communicate with the hackers. Meanwhile, bitcoin and blockchain technologies have set the foundation for payments systems that are easy to use, instant and more or less anonymous, making it substantially more difficult for authorities to trace transactions and hunt down the hackers.
In addition, anonymous online networks such as Tor have made it possible for the criminals to host almost untraceable websites.
In this article, the latest in our ‘Spotlight on ransomware’ series, we’re going to shine a light on the technologies that make ransomware possible, explore a variety of ransom payment methods and reveal why we strongly advise against ever paying the ransom.
What is bitcoin and blockchain technology?
If you’re reading this blog, there’s a pretty good chance you’ve heard of the term ‘bitcoin’, but you may not be familiar with what it actually is or how it works.
Bitcoin is a digital currency. At the time of writing, one bitcoin is worth about $3,500. The currency is both decentralized and distributed, meaning it is powered entirely by its users and functions independently of any organization or middlemen (e.g. banks). It is built on blockchain technology, which is a public ledger that records every bitcoin transaction that has ever been carried out and stores them in groups known as blocks. Once a block has been recorded in the ledger, it cannot be changed or manipulated without altering every single block that succeeds it. Every connected node has and distributes a copy of the blockchain, which ensures a high level of security and makes the system more or less invulnerable to corruption.
What does the blockchain have to do with bitcoin? Well, not only does it help everyone reliably keep track of how many unspent bitcoins are in circulation, it’s also critical for releasing bitcoins into the world.
The key advantages of bitcoin as a currency is that the system is more or less impervious to corruption or tampering, transactions are anonymous and, due to the fact that the currency does not rely on any country’s financial framework, international bitcoin payments involve low fees.
While these benefits offer a lot of real world appeal and have many legitimate applications, they have also contributed toward bitcoin becoming the preferred method of payment among cybercriminals.
How do bitcoin and the blockchain enable cybercrime?
Bitcoin and the blockchain have quickly become integral pillars in the modern malware scene. In the past, hackers attempted to use other online payment systems such as Western Union and PayPal to carry out elaborate phishing scams.
However, because these systems were still linked to a bank account, investigators could usually follow the digital paper trail and track down the criminals.
The covert nature of bitcoin minimizes many of these risks for hackers, but it’s not only the anonymity that makes it so appealing. Transactions are more or less instantaneous and do not require finicky login details, there’s no need for currency conversions and the system – at presently, at least – is entirely unregulated.
These attributes combined provide a high level of flexibility and enable the criminals to set up and close down operations on the go as they attempt to stay one step ahead of authorities.
Emsisoft Anti-Malware takes care of the dirty work for you …
While the exact payment system can vary a little between ransomware families, the process typically looks something like this:
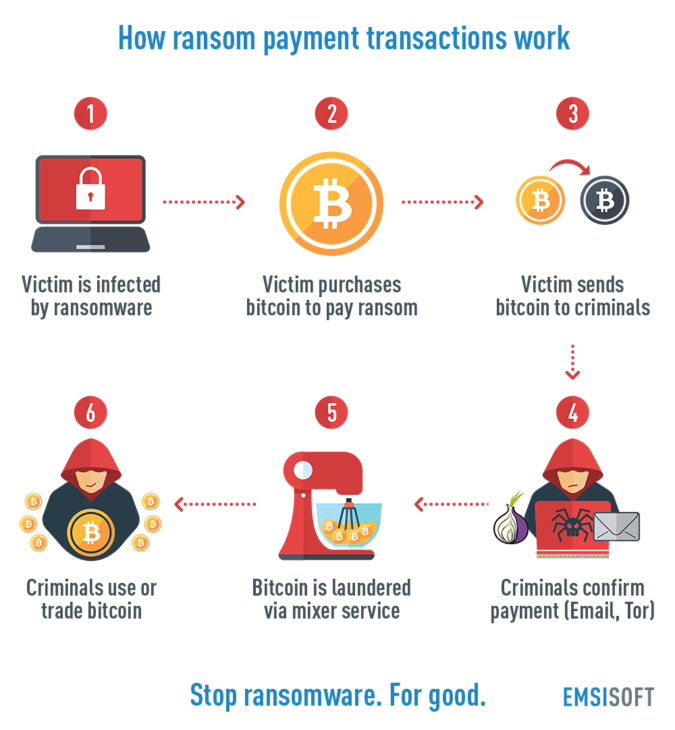
How a ransom payment transaction works
- The victim is presented with a ransom screen with the hackers’ demands, which often includes instructions detailing how the victim can purchase bitcoins in order to make the payment.
- The victim purchases the bitcoins required to pay the ransom.
- The victim sends the money via a bitcoin exchange to the hacker’s bitcoin wallet..
- The criminals confirm payment via email or a Tor site and, if the victim is lucky, will provide the means to decrypt the victim’s files.
- The bitcoins may be laundered via a bitcoin mixer service, which exchanges bitcoins for different bitcoins of the same value minus a small commission. Alternatively, the ransom bitcoins may be passed through a peer-to-peer tumbler, a network of bitcoin wallets (sometimes numbered in the tens of thousands) that scramble the currency and help the criminals conceal their tracks.
- The criminals may use the bitcoins to purchase goods directly or, more rarely, they may trade the bitcoins for other currencies on one of the many bitcoin exchanges.
Ransom payment examples: the “good”, the bad, and the plain stupid
Just like other forms of crime, ransomware can be executed in a clever, professional manner, or it can be rolled out ad hoc by opportunist cowboys.
As we touched on earlier, the Spora ransomware boasts one of the best payment systems we’ve ever seen. Upon infection, Spora presents the victim with a website featuring a beautifully designed user interface which, unlike most other ransomware, does not require users to download Tor to access. Spora also offers a variety of recovery packages: $190 worth of bitcoins will decrypt all your files; $30 of bitcoins will remove the ransomware (but not restore your files) or give you immunity from future infection; and $40 of bitcoins will restore some (but not all) of your files. Spora has its own communications server and chat box, making it much more challenging for law enforcement to track.
Crucially, Spora generates a new bitcoin address for every victim, therefore making it much that much harder for law enforcement agencies to track the ransom payments and therefore the criminals themselves.
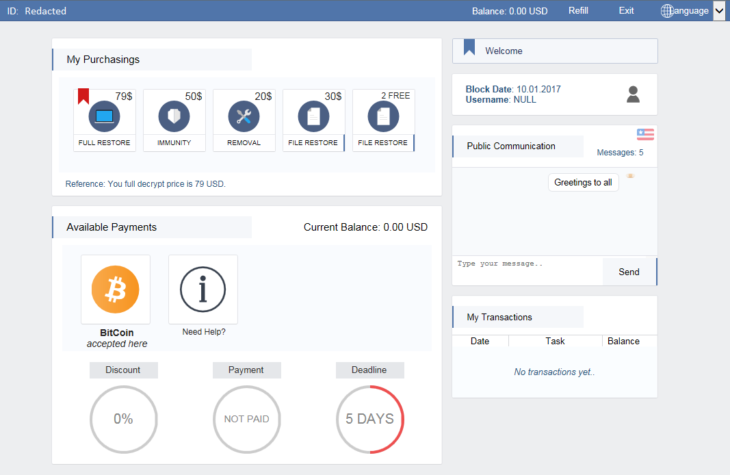
English version of the Spora ransom payment site.
At the other end of the spectrum we have NotPetya, ransomware which recently caused widespread disruption across Europe and the rest of the world. NotPetya’s payment system had some significant flaws, meaning that despite its relatively high infection rate, the ransomware authors only managed to extort about four bitcoins from their victims.
What went wrong?
Firstly, the campaign relied on a regular email address, which was quickly taken down by the email provider, leaving the cybercriminals with no way of communicating with their victims. Secondly, and contrary to Spora, NotPetya ransomware had only one hard-coded bitcoin wallet for victims to send money to, making it easy to track how much money the hackers had generated and giving authorities a slight edge when it comes to hunting down the perpetrators.
Should you pay the ransom?
It’s tempting to give in to ransom demands when your files have been compromised, and even more so when it’s business data at stake.
In a study of 600 business leaders, research from IBM found that as many as 70 percent of companies hit with ransomware paid the cybercriminals to restore their files, with more than half the ransom amounts totaling more than $10,000.
Regardless of how badly you might want to regain access to your data, we strongly recommend that you do not become a part of this statistic. Here at Emsisoft, we always advise against paying the ransom for a few reasons:
- There is no guarantee: although the criminals assure you they will decrypt your system after receiving payment, ultimately there’s no guarantee that they’ll deliver on this promise. After they have received your bitcoins, the only incentive for the hackers to unlock your files is maintaining credibility among victims that they will in fact decrypt your system and incentivise payment. These days, however, the line between profit-seeking ransomware and disruption-focused ransomware (e.g. NotPetya) is more blurred than ever, which means it’s difficult to tell what the hackers’ motivations really are. Simply put, there is no guarantee!
- There are free tools to help: just about every ransomware author insists that your files are irretrievable without paying for the decryption, but that isn’t always the case. A range of ransomware can be undone with freely available decryptor tools from Emsisoft and other security firms, and more are always in development. Don’t even consider paying the ransom until you have checked if there is a decryptor tool that can help you.
- It incentivises more cybercrime: paying the ransom promotes criminal behavior and encourages the creation and spread of even more ransomware. Ransomware is almost always financially motivated; if no one paid the ransom, there would be little reason for the hackers to continue releasing it.
Of course, it’s not always easy to rationalize things when your system has been locked and you’re staring at a threatening ransom note. Nevertheless, try to keep your cool and avoid giving into ransomware wherever possible, and remember to follow the right steps in case disaster strikes.
Ransomware: the perfect crime?
While bitcoin and the blockchain do a pretty good job of concealing their users’ identities, it’s important to note that law enforcement is often still able to track down the criminals involved in ransomware and take out their operations by focussing on the weakest link:
The criminals themselves.
In September 2015, for example, the Dutch National High Tech Crime Unit, working in conjunction with Kaspersky Lab, arrested two men who were allegedly involved in a variant of CoinVault, a piece of ransomware that encrypts files and holds them to ransom. Unlike other versions of the ransomware, the code of this particular iteration was peppered with flawless Dutch phrases. Given how difficult it is to write perfectly in Dutch, investigators suspected a link to the Netherlands, and this geographical connection proved to be a critical part of the hackers’ arrests.
Other high-profile ransomware authors who have been busted by authorities include 11 members of the Reveton ransomware gang, who were arrested by Spanish police in early 2013; and three British citizens involved in the Metropolitan Police ransomware who were arrested, somewhat ironically, by the real Metropolitan Police.
It’s highly likely that we’re going to see bitcoin and blockchain technologies play an increasingly important role in the modern world – and that role will be a mostly positive one. At the same time, however, there’s no denying that these systems are at least partly responsible for supporting the massive wave of ransomware attacks that have taken the world by storm in recent months.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialHave a great (ransomware-free) day!


