Efficient protection against new malware: Emsisoft’s Behavior Blocker
What is behavior analysis and how does it work?
Emsisoft Anti-Malware’s File Guard checks all executed programs through signature scans, just like any other anti-virus software does. Even though we rely on a high-performance dual-engine scanner, new malware can only be detected if there is already a signature for this file. A signature is similar to a fingerprint that makes it possible to identify an offender – or malicious software in our case.
Precious time is lost during the gap between the appearance of new malware and the release of signature updates that detect it, leaving your PC unprotected in the meantime. This is why we have been developing Emsisoft’s Behavior Blocker since 2005. It is a technology that is able to detect and block dangerous malware without the need for signatures.
Any type of malware, whether virus, trojan, keylogger, rootkit or spyware, has unique characteristics. Each type has main goals to achieve, which helps to easily identify them. A virus infects, a worm spreads, a keylogger saves keyboard input, a backdoor trojan sends data, and so on. An example: Within the single category of trojans, individual trojans can differ in HOW they send data. While the methods different trojans use to send data may differ, the end goal, the characteristic of sending data, is the same for all trojans.
This is where Emsisoft’s Behavior Blocker comes in. It analyzes the behavior of all active programs in real-time and warns you if any programs exhibit dangerous behavior. Let’s continue using the analogy of an offender: Imagine meeting a suspicious person on the street at night. Based on various criteria such as nervous looks, a determined approach towards you or even reaching for a weapon, you will decide at one point or another that the situation is going to become dangerous. This is exactly how Emsisoft’s Behavior Blocker evaluates all actions carried out by active programs, in particular, invisible background processes which you would not normally notice.
If you’re thinking this sounds too good to be true, you’re right. This technology also has a disadvantage. Behavior analysis detects malware through behavior patterns, but the behavior within a type of malware is always the same. This is why behavior analysis is not able to tell two different malicious files apart by name. Behavior analysis cannot tell you if the worm’s name is NetSky or Bagle or if the trojan is Optix or SubSeven. It can only tell you that it is a worm or a trojan. However this is a small trade off, when you weigh up the benefits of this very powerful protection.
What does Emsisoft Behavior Blocker detect?
The Behavior Blocker is currently trained to detect the following types of malware:
- Backdoor trojans (backdoors)
- Spyware/adware
- HiJackers
- Worms
- Dialers
- Keyloggers/Banking password sniffers
- Trojan downloaders
- Viruses
- Rootkits
It is also able to detect and stop the following potentially dangerous actions:
- Installation of unknown drivers and services
- Any kind of process manipulation such as DLL injection, code injection, patching, termination, etc.
- Installation of new BHOs (Browser Helper Objects) and toolbars
- Modification of browser settings
- Invisible installation of software
- Modification of the hosts file (redirecting of websites)
- Installation of debuggers in your system
- Creation of auto-run entries
- Simulated mouse and keyboard input
- Direct access to hard-drive sectors
- Modification of system security policies
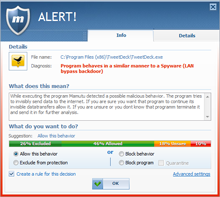
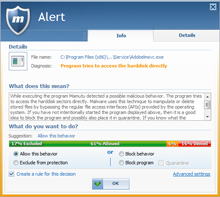
What to do when you receive an alert
Emsisoft’s Behavior Blocker is a system that has been designed to detect suspicious behavior patterns. As behavior patterns of regular programs and malware partially overlap, there are some cases where it may be mistaken. Therefore you should take all evidence into consideration before prematurely blocking a program. If in doubt, you may submit a suspicious file to us at any time for analysis.
While false alerts are possible in principle, they occur rarely. On one hand, Emsisoft’s Behavior Blocker works in an extremely efficient manner thanks to years of fine tuning; and on the other hand, you can rely on the intelligence of the masses through the use of community-based alert reduction. This function gives you a recommendation when an alert occurs, based on the decisions of all the other users. Please see the clearly understandable graphic which illustrates the percentage of users that have performed the action. This enables you to quickly decide if you would like to allow the program’s current behavior (other behavior patterns will still be alerted to), exclude it from monitoring ( trust completely), block it (the process will be terminated) or quarantine it (the process will be terminated and the exe file will be quarantined so it can no longer be started).
In addition, you can specify whether applications that have been allowed by a certain percentage of community members, will be automatically allowed. Working without the interruption of annoying pop-ups is thus possible, and you do not have to make potentially difficult decisions when encountering unknown processes. Sharing statistical information with the Emsisoft Anti-Malware Network regarding your own decisions is of course voluntary and can be disabled at any time.
A general hint for use of the Behavior Blocker:
Once you have installed the software, please ensure that the guard is up and running and then run any programs you use frequently to avoid potential false alerts in future. This will only take a few minutes, and Emsisoft’s Behavior Blocker will then be set up optimally for your PC.
It is a common misconception that Emsisoft’s Behavior Blocker uses conventional heuristics. Heuristics checks files on your hard-drive for malicious routines and then classifies a file as dangerous or safe based on a calculation of probability. Emsisoft’s Behavior Blocker works on a higher level though, and directly monitors how active programs behave on your system.
Who to turn to if you have questions
If you are ever in doubt as to whether a program is really dangerous, our support team will be happy to provide assistance. You can contact us via our Support Forum or by e-mail at any time to quickly receive answers from our security experts.
Have a nice (malware-free) day!
Your Emsisoft Team