Rogue Antivirus. Again?
We blogged about Antivirus2010 and tried to find out a little more than what normal analysis could have done. Our series of exposing latest rogue security product variants continue this week with another of its kind, Security Suite.
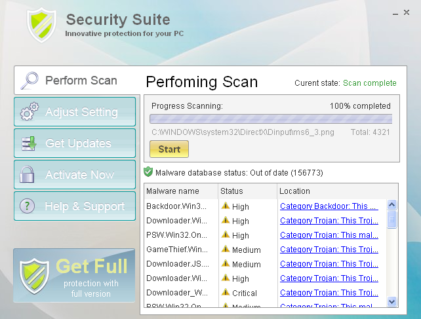
Back in 2008 with AntivirusXP and then with few others, a trend started in rogues which were creation of randomly named executables as main malicious binary and also in similar randomly named folders. Security Suite carries on the trend, dropping the rogue application under %userprofile%Local SettingsApplication Data%random%%random%.exe.
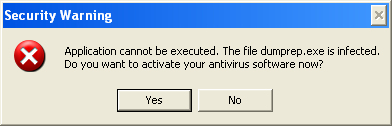
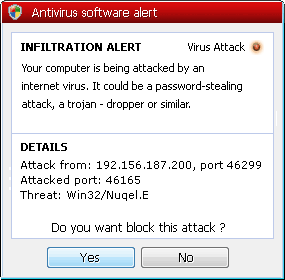
Fake alerts have always accompanied rogue security products, and few instances of such in this variant are below.
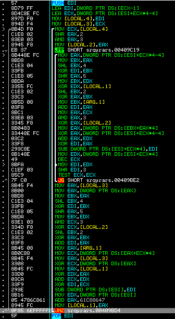
Digging deep into the rogue product, we see that as most recent variants, this one is also packed and encrypted to protect itself from further analysis and make an attempt to make the job analysts harder. The decryption routine for the same
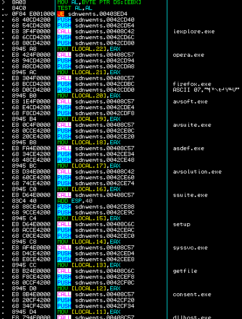
Security Suite marks its presence in the infected system with a unique mutex named “MSFT.Notepad”, another continuous attempt to confuse end users. The malware also disables execution of most applications barring few with following executable names.
- Iexplore.exe
- Opera.exe
- Firefox.exe
- Avsoft.exe
- Avsuite.exe
- Asdef.exe
- Avsolution.exe
- Ssuite.exe
- Setup
- Syssvc.exe
- Getfile
- Consent.exe
- Dllhost.exe
We also saw instances of remote connection attempt by the rogue product to the following malicious urls
• hxxp://antivirone.com/percer.php?login=NjguOTQ3
• hxxp://antivirone.com/check?pgid=5
We did some domain specific research and ofcourse the domain was created as recently as
Name: Kese Done
Organization: Done inc
Address: Lee st 66
City: AL
Province/state: AL
Country: US
Postal Code: 36022
Phone: +1.9957737722
Fax: +1.9957737722
Email: [email protected]
Nameserver Information:
ns1.antivirone.com
ns2.antivirone.com
Create: 2010-08-11 17:05:19
Update: 2010-08-11
Expired: 2011-08-11
Nothing really stands out. We then visited the mentioned “websites” antivirone.com and antivirstrong.com, which are not surprisingly completely similar. Malware authors are always trying to bring out new different ways to fool end users, and when one visits accidental redirections or popups, the “polished” look will surely confuse him. But that is why we are constantly carrying on our attempts to educate and make users aware.
Lets have a look here, http://antivirone.com/aboutus and the first thing we notice is, “Founded in 2000, the company’s mission is to bring security, productivity and privacy to the Internet.” And then this, “Our products and services are used by millions of people, with registered customers in over 150 countries. Our products are actively used by individual users, small businesses, non-profit and community organizations, educational institutions, government agencies, right through to a number of the worlds leading Fortune 500 companies.” Interesting, but did we just see the domain itself being registered on 11th August 2010!
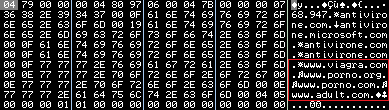
We carried on our reverse analysis simultaneously, and discovered that the malware will also try to open adult content related websites on the victim’s computer as time passes by
• www.viagra.com
• www.porno.org
• www.porno.com
• www.adult.com
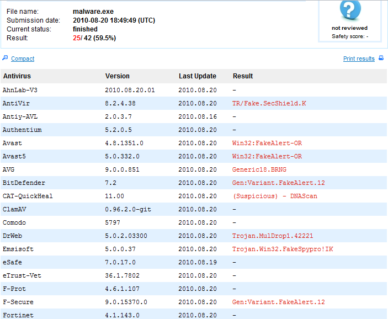
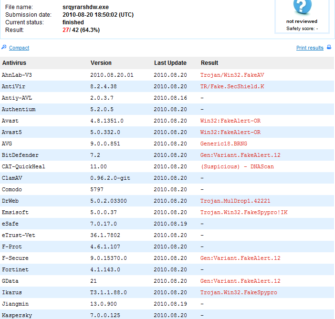
We are as always ahead of these rogue products, and Emsisoft AntiMalware detects this threat as Trojan.Win32.FakeSpypro!IK or Adware.Win32.SecuritySuite!A2.
Detailed Report – http://www.virustotal.com/file-scan/report.html?id=9ef86655b73e16648f9ac9d079ea0c76fce26ee34a0073ea4d3a38fdbb17d948-1282330189
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialDetailed Report : http://www.virustotal.com/file-scan/report.html?id=622ee856d56f127324d245b23f10b893e964c4e8e7175d61ebe9d5f742ed7a4b-1282330202