antivirus2010, userinit and then some more
There is a new rogue variant making rounds going by the name Antivirus2010. The malware copies itself to the System32 directory with a name similar to commonly used Windows file present in same directory.
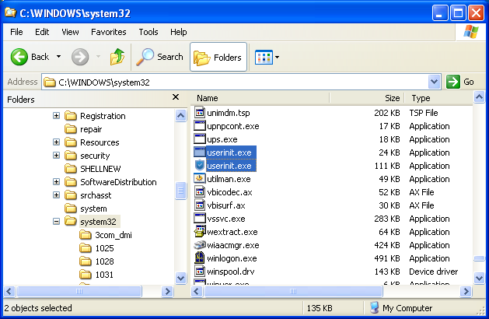
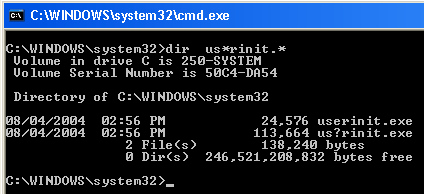
If looked through naked eye, there seems to exist two userinit.exe though one has a unique icon and the other doesn’t. We traversed through the System32 directory in command prompt and the non-english character in the malicious userinit.exe came out quite easily.
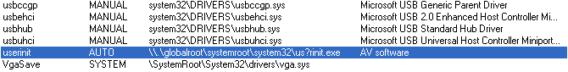
The malware registers itself as a service to start automatically with Windows.
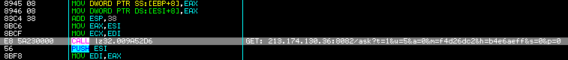
On execution, the malware extracts and builds PE file on memory with the name lz32.dll, and makes a remote connection to download another dll component.
Remote address connections established are
- 213.174.130.36:8082/ask?t=1&u=5&a=0&m=aa26135f&h=b4e6aeff&s=0&p=0
- 213.174.130.39
- 213.174.130.39:80/update.db
- http://213.174.130.32/verify.js?key=
- http://213.174.130.39/uninstall.js
- https://secure.avsbilling.com/order/get.php?i=antvir&advert=
- https://secure.avsbilling.com/order/activate.php?orderid=
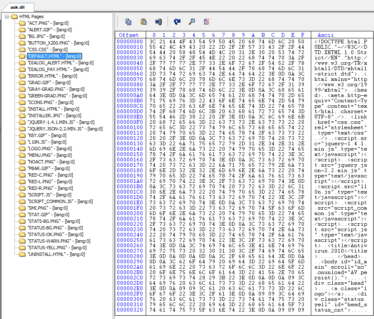
Downloaded malicious DLL is dropped under the System32 directory. The DLL is normally an eight lettered randomly named file, for example mswmqnei.dll or mspnxdcm.dll and is encrypted. The DLL is loaded into the memory to display the main UI of the rogue security product. The UI was created using HTML/Javascript, which as we can see, the malware stores the UI in the resource area of the DLL.
Analysing the HTML file, in the INSTALL.HTML we can notice a url which is currently inactive. Incidentally the IP in the url is the same one that the malware uses to download malicious file.
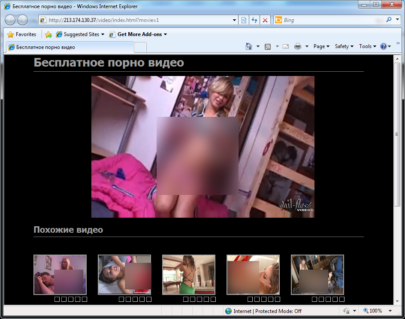
The front end of the IP if visited presents a website with adult content.
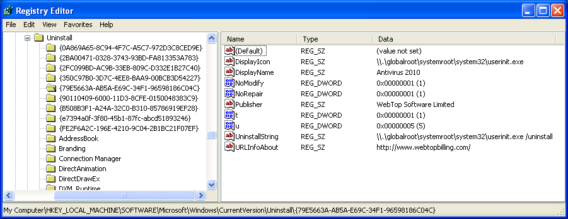
Looking the registry modification we found some more informations about the rogue product and we decided to do some more research.
A simple dns information on hxxp://www.webtopbilling.com revealed
Domain Name: WEBTOPBILLING.COM
Registrant:
N/A
Nick Besmark ([email protected])
P.O. Box 2494
Victoria
Mahe,00000
SC
Tel. +7.9263901779
Creation Date: 04-May-2010
Expiration Date: 04-May-2011
Domain servers in listed order:
ns2.unitedplatform.com
ns1.unitedplatform.com
Not specifically suspicious about an website registered by someone residing in Mahe, Seychelles and which currently gives a 403 Forbidden message. We then looked at unitedplatform.com and the first thing we noticed about it is that we actually land at domaincontext.com which is a domain registrar website.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialBut we didn’t want to leave unitedplatform.com yet, and we stumbled upon http://www.malwareurl.com/ns_listing.php?ns=ns2.unitedplatform.com. The malware domains listed there shows more than one instance of malicious activity and maybe coincidence again that all are recently created domains. There maybe a distant connection we can assume, which proves again the inter-relationship between various rogue security products and exploits in the web. It is more than a billion dollar industry out there, but we are always more than a step ahead from them.