Emsisoft explores the worst passwords of 2016


Trying to remember any one of the 500 passwords you need to function in today’s digital society is one of life’s many frustrations. But, opting for convenience over security is basically a written invitation to hackers.
Cyber security experts continue to urge users to become better informed about online threats and the importance of using complex, difficult-to-guess passwords, yet many users continue with insanely unsafe ones.
According to a new analysis of the passwords leaked in the recent Yahoo data breach, the most popular choices are still “123456” and “password”.
The ten most common passwords in the leaked Yahoo database were:
- 123456
- password
- welcome
- ninja
- abc123
- 123456789
- 12345678
- sunshine
- princess
- qwerty
Passwords are your first line of defence
Brute force password hacking is one of the most common ways hackers break into computers. The Worst Passwords of 2016 list reflects the above passwords with the additions of ‘hottie’ ‘loveme’ and ‘flower.’ The force remains strong with the continued use of Star Wars themed ‘solo’ and ‘princess.’ Sadly, all of these passwords and more are known by many hackers and are built into malware.
The Conficker worm, which at its peak in 2008 infected 7 million computers worldwide -and which continues to infect computers today- utilised these passwords and continues to gain access with the use of these passwords. (See full list of Conficker passwords here).
In a massive theft of Twitter usernames and passwords involving nearly 33 million customers, “123456″ was by far the most commonly used passcode, according to security company LeakedSource. More than 120,000 people whose credentials were hacked had used “123456” as their Twitter password.
When it comes to bad passwords, it’s quite discouraging to see that in the last 9 years not much has changed. Many of 2016’s Worst Passwords are utilised by Conficker are largely responsible for the worm’s success then and continued appearance now.
Today, creating a good, unique password for every device and application you use is essential to securing your digital information. Having a solid online protection suite such as Emsisoft Anti-Malware is important, but it’s also kind of irrelevant if you’re just handing out the keys to get in.
How to create an impenetrable password
There’s a lot of talk today about what comprises a good password. Most sources will tell you that you need at least 16 characters and that those characters need to be a unique combination of numbers, letters, and symbols. For example, g43h3982D219Qtt7 is a pretty darn good password. It makes absolutely no sense, and it is pretty much impossible to remember.
Unfortunately, what makes a password impenetrable is also what makes it hard for you to keep track of and use. Creating a g43h3982D219Qtt7 for every device and app you use is easy enough – in fact, there are even password generators that will do this for you – but remembering which is which is tough. Keeping track of everything with an excel sheet or word document is a big no-no. In light of this, companies like SplashData will manage your passwords for you. If you’ve got the money and you stand to lose a lot, purchasing one of these services isn’t a bad idea at all.
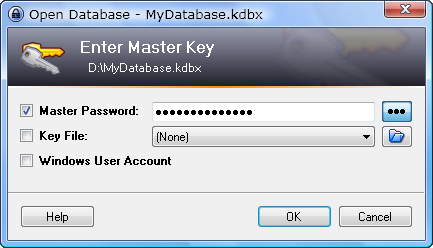
But what about those of us who are looking for password security on a budget, who want something a little more effective than a bucket of water perched atop the threshold of our front door? Keepass is a free service that stores your passwords locally on your computer. You only need to remember one password for access, the master. Make the master password strong and add an extra layer of security with the use of a key file.
Get creative with random personal information
If you’re trying to manage your own passwords, the very best thing you can do is to be random. Create passwords that only you could think of, and they’ll become the best passwords. Don’t use anything associated with the facts of your life or that can easily be gleaned by perusing your social media. Just gather some of the thoughts circling around in your head that you’ve never shared with anyone, and combine them to create a password you can call your own.
Have secret ambitions of becoming the next international tap dancing sensation, owning 6 iguanas, and retiring in Guam? Excellent. How about 6tappingiGUAMnas91a7, with some random characters added at the end for good measure.
Want to join the circus, buy a pony, and eat nothing but ½ pound burgers for the rest of your days? Great! Your new password is 0.500ponyClown4Life!
Editor’s note: After we first published this post, one of our amazing followers sent us as additional method that is too good not to share. (Thanks Dennis!)
The personal algorithm method
Using easy-to-remember algorithms can provide unique and strong passwords for each account. Here’s how it’s done:
If we use the word Emsisoft as an example, you first select the keyboard character next to each letter in the word “emsisoft”. (This applies to the English QWERTY keyboard).
Depending on the algorithm you choose, you may wish to select the keyboard character to the immediate upper-right. The “e” becomes “4”. Do this with each character such that the “m” becomes a “k” and so forth. This provides a “4ke9e0t6” character string for the password that is unique to the website. Then add to this your own special password portion which can be anything; for example the name of a town, pet, favorite dessert, hairdo or a calendar date.
For example the date “March 28 2017” using the same algorithm will create the string “Kw5fu-@*-@)!&”.
Note: we used the shift key on the “M” in March and on all numbers plus a “-“ character for the “space”. On numbers we could have also used an algorithm that used a down-left key substitute which would have created “Kw5fu-qu-qo!y”. We also had to adjust the algorithm to account for no down-left key for“1” by using the shift key instead.
Using these two algorithms give me unique passwords of “4ke9e0t6Kw5fu@*@)!&” or “4ke9e0t6Kw5fuquqo!y”. They are complex and strong passwords but easy to remember and reproduce.
Now using the first algorithm the password for “Amazon” and date “March 28 2017″becomes “Wkws0jKw5fu@*@)!&”. The password for “Netflix” becomes “J46tp9dKw5fu@*@)!&”.
Algorithms can be more complex to give even more variety such as changing the next-to key with each character. For example the letter “g” has the letters “y”, “h”, “b”, “v”, “f” and “t” surrounding it. The algorithm could use the upper-left key for the first character, the immediate-left key for the second character and so forth moving counterclockwise around each character in the website name. The word “Emsisoft” would the result in a translated string of “3nzkd0t5”. By adding your own special down-left date string the password becomes “3nzkd0t5Kw5fuquqo!y” By using the same algorithm for each password it is an easy to regenerate a unique strong password for each and every account.
For more algorithm variations the standard special section string used in each password can be entered in backwards for accounts that begin with certain letters such as forwards in letters “A through M” and backwards for letters “N through Z”.
If you are required to change your password each month then simply add a date component to the password which is tied to the current date. For example upper-right keys for the month name and lower-right keys for the year numbers but reversing the numbers for the year for each even numbered month (Feb., Apr., Jun., Aug, Oct., and Dec.). This results in the password date section for March 2017 being “Kw5fuwpqu” and using the same algorithm for April 2017 being ”W-59puqpw”. By reversing the numbers for the year the password date section entirely changes from the past month. There are many algorithms that can be used on dates that can make the monthly password section completely unique. Usually when monthly password changes are required the first login of the month uses the last password and a new password in immediately required. Both of these are easy to provide using your own password algorithm.
The variations of algorithms are extremely large and can be as complex as you need. Just decide on your own algorithm and enjoy having unique, strong passwords for each account without having to memorize each or without having to write them down.
Important: Do not reuse passwords. Sites are hacked often and the more websites that utilise your one password, the greater risk you face. Create unique passwords for each account you have and your digital life will be safer for it.
As you can see, the secret to good passwords is that they’re secret. Things like g43h3982D219Qtt7 certainly work, but if you’ve got a colourful enough imagination the possibilities are limitless.
In either case, the important take away is that choosing passwords is not just some flippant activity. It’s your first line of defence against malware. For the best protection, use passwords that are random and unique. And, whatever you do, stay the hell away from the Top 25.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialHave a great (malware-free) day!