5 ways to protect yourself against encrypted email attachment malware

Your email inbox is a digital minefield. Phishing can lure unsuspecting users into willingly giving away their personal information, while seemingly innocuous links can lead to click-happy employees inadvertently installing disruptive malware on the company network. One particularly interesting type of threat is password-protected email attachment malware, which uses macros to drop malicious software onto the host PC.
Have you received an email with a password-protected attachment? Before you open it, take a moment to read this article – there’s a good chance it could be malicious. Let’s take a look at how password-protected email attachment malware works and what you can do to protect yourself.
What is password-protected email attachment malware?
It’s no secret that email is one of the most common delivery vehicles for most types of malware. In fact, in 2016, about two-thirds of all malware was installed via email attachments, according to figures collated by Verizon.
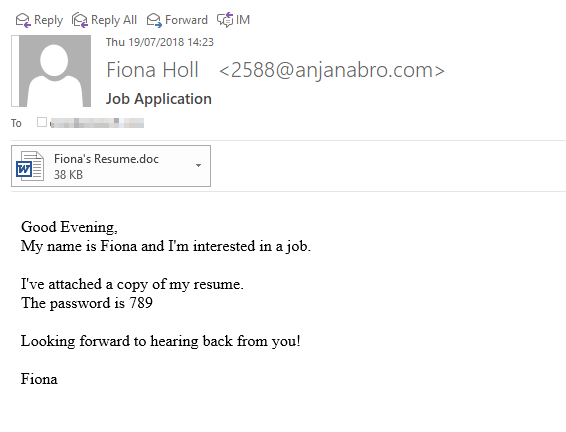
Password-protected email attachment malware is slightly different from conventional email attachment malware in that it requires you to enter a password in order to open the file. In years gone by, most password-protected email attachment malware were archive files, but increasingly we’re seeing a resurgence of attackers use encrypted DOC and PDF files.
The emails usually look fairly legitimate and the attachment is often presented as a common business document, such as a shipping receipt, financial report or resume. When you input the password (included in the body of the email) to decrypt the document, your software (e.g. Microsoft Word if you’re trying to open a DOC file) will ask if you want to enable content. If you click “enable content”, you’ll also be enabling macros, which can automatically drop malicious software onto your PC.
What are macros?
In this context, a macro is a small program or script, often embedded inside another program, that automates common tasks. This can be used to simplify time-consuming processes and turn them into tasks that can be completed with the press of a button. For example, you could record a macro in Microsoft Word to create pre-formatted tables or insert a company letterhead, while in Microsoft Excel you might use a macro to format imported data or change row height and column width (in addition to myriad other things).
As you can see, macros have a wide range of legitimate uses. However, they can also be used for nefarious purposes. Their simplicity and configurability have made them highly popular among cybercriminals, who use macros to automatically execute malware when you open the encrypted attachment.
Why do hackers use this type of malware?
In the past, Microsoft software had macros enabled by default, which meant that the malware would be unleashed the moment you opened the offending document. Since then, Microsoft and other software vendors have disabled macros by default. This has left malware authors with the tricky task of convincing users into not only downloading and opening email attachments, but also enabling the macros that the malware needs to function. That’s where password-protected email attachment malware comes in. Here are just some of the reasons why attackers use this type of malware:
1. Avoid email filters
From a criminal’s point of view, one of the key benefits of using password-protected email attachment malware is that it can’t really be detected by email filters. Although modern email gateway scanners are capable of detecting and removing malicious attachments, they can’t do anything when it comes to encrypted files. That’s right – regardless of your provider, your email filter has no way of distinguishing whether an encrypted attachment is malicious or harmless.
It’s worth noting that some scanners can detect malware hidden in encrypted ZIP archives if the file appears frequently (in the same shape and size) by doing a simple hash check, but these types of files are almost always unique, meaning any type of smarter signature or heuristic detection does not work.
2. Easy to use
Another factor that contributes to the popularity of email attachment malware is how easy it is to create. Malicious macros are usually built using the scripting functionality in Microsoft Office, which is typically written in Visual Basic or JavaScript – two simple programming languages that require relatively little expertise to use. This low barrier to entry enables criminals with modest technical skills to create harmful and effective macro malware.
3. Social engineering tactics
Looking beyond the technical aspect, attackers tend to use encrypted email attachment malware simply because it’s an effective form of social engineering that increases the chances of infection. Rather than coercing users into downloading dodgy executable files that will probably be caught by antivirus software or the email scanner, criminals use encrypted files to exploit human nature. The malware is distributed via convincing attachments that look like any other business document an employee might open without a second thought. What’s more, the addition of password protection creates a sense of security and authenticity, which makes it more all the more likely a user will open the file.
How can you protect yourself against encrypted email attachment malware?
1. Stay vigilant
Perhaps the most important thing you can do to reduce the risk of becoming a victim of encrypted email attachment malware is to stay vigilant and keep yourself informed about social engineering techniques. Always take the time to verify that your email is safe and sent from a legitimate source. Avoid opening any attachments unless you know and trust the sender, and remember that the sender’s name and address can be faked quite convincingly.
Some organizations, especially those that handle sensitive data such as financial or legal firms, routinely send password-protected documents to ensure that only the intended recipient accesses its contents. The key is to ensure that you’re receiving the document from a legitimate source as mentioned above.
2. Be cautious with your clicks
On a similar note, never blindly click on attachments or hyperlinks in the body of the email. If you have to open an attachment, make sure the file extension is appropriate (e.g. a picture of your friend’s holiday probably shouldn’t be an EXE or JS file) and carefully inspect the full URL of any link before clicking. Be extremely wary if any email, attachment or website asks you for your password or login details.
3. Manage your macros
Generally speaking, it’s probably a good idea to leave macros disabled in your software unless you have very good reason not to. Of course, many businesses rely heavily on macros in their day to day operations, which means this may not be a viable option. Digitally signed macros can be effective in the short term, but can be challenging to manage as the company grows. In this scenario, using reliable antivirus software and training staff on the basics of IT security are your best options and can go a long way toward reducing the risk of macro malware infection.
4. Update your software
As noted, old versions of Microsoft Office have macros enabled by default. Newer versions disable macros by default and also offer Protected View, a read-only mode that prevents the execution of potentially harmful content, thereby reducing the risk of malware infection. Invest in new software where possible and always apply the latest patches to resolve any security flaws the vendor may have recently resolved.
5. Use reliable antivirus software
Last but not least, reliable antivirus software can play a critical role in protecting you against encrypted email attachment malware. Endpoint protection software that makes use of behavior blocker technology can identify suspicious patterns of activity and stop the malware before it can execute. You can rest assured that you’ll be safely protected, even if you happen to open a harmful email attachment.
The ultimate defense against macro malware
Password-protected email attachments can be an effective way for attackers to deliver malware directly to your inbox without any way of your email filter knowing. Thankfully, there are a number of things you can do to keep yourself safe. Staying wary of social engineering tactics, being mindful of macros and using trusted antivirus software can significantly reduce the risk of being affected by this type of threat. If you’re in the market for antivirus software that provides reliable protection against email attachment malware, please feel free to download your free trial of Emsisoft Anti-Malware.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialHave a great (malware-free) day!