How to prevent business email compromise attacks

Business email compromise (BEC) scams are low-tech attacks that use social engineering techniques to exploit natural human tendencies.
While they may not get as much attention from the press as high-profile ransomware attacks, BEC scams are considered one of the biggest threats facing companies today. Between June 2016 and July 2019, there were 32,367 successful BEC scams in the U.S., which cost U.S. businesses more than $3.5 billion, according to figures from the FBI.
Fortunately, there are some very effective and easy-to-implement strategies for stopping BEC attacks. In this post, we’ll show you how you can combine staff training, process implementation and authentication technology to protect your organization from BEC attacks.
What is business email compromise?
A BEC attack is a sophisticated scam that targets businesses and individuals who perform wire transfer payments.
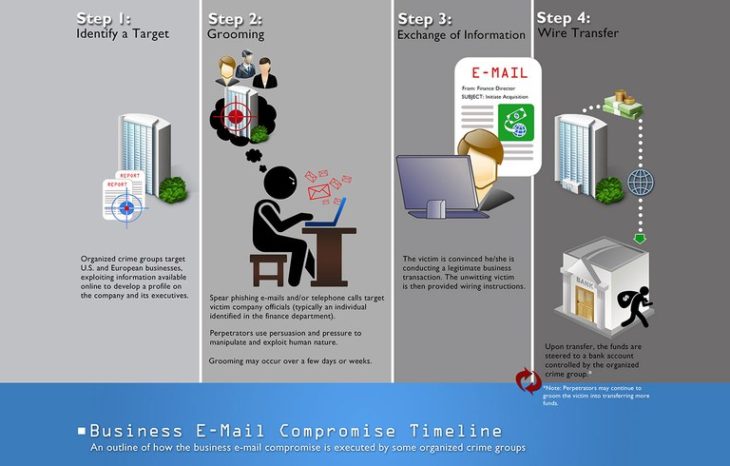
Business email compromise timeline infographic courtesy of the FBI
Unlike regular email scams that are distributed to thousands or millions of users, BEC attacks are carefully planned and highly targeted.
A typical BEC scam involves an attacker gaining access to the email account of a C-suite executive via a phishing campaign, malware infection, password leak or brute force attack. The attacker monitors the compromised email account to learn the victim’s communication habits and gain a thorough understanding of the company’s routine processes and procedures.
Once the attacker has carried out their surveillance, they send an urgently worded email to a target, instructing the recipient to carry out an important request.
What makes the scam so convincing is the fact that the email is sent through legitimate communication channels and appears to be from a familiar and trusted business contact. The target often feels inclined to quickly process the request without question when the email appears to be sent from the target’s boss or boss’ boss.
Monetary gain is usually the primary goal of a BEC scam. Victims are deceived into believing they’re performing a regular transaction, when in reality they are transferring large sums of money directly into the bank account of the scammers.
In other cases, attackers may use BEC scams to extract employees’ personally identifiable information, which can be used in future attacks or sold on the black market.
Business email compromise vs spear phishing and whaling
BEC scams, spear phishing and whaling share a number of similarities. All three are email scams that use social engineering to extract money or sensitive information from a specific target.
However, the way they accomplish this goal is slightly different. Whereas spear-phishing and whaling attacks involve directly attacking a target with phishing emails, BEC scams rely on infiltrating an email account related to the target in order to impersonate a known business contact and gain the trust of the target.
Worst business email compromise cases of 2019
1. Tecnimont SpA
In January, Tecnimont SpA, an international industrial group headquartered in Milan, revealed it had been caught up in one of the largest BEC scams in history. While impersonating CEO Pierroberto Folgiero, attackers sent a series of emails to the head of Tecnimont Pvt Ltd, the Indian subsidiary of Tecnimont SpA, to organize conference calls about a secret business venture in China.
During the bogus calls, the fraudsters assumed the roles of various stakeholders, including Folgiero, a Swiss lawyer and other senior executives. The attackers eventually convinced the head of Tecnimont Pvt Ltd to transfer $18.6 million from India to banks in Hong Kong. The money was withdrawn almost instantly.
2. Cabarrus County
In July, Cabarrus County, North Carolina, admitted it had been scammed out of more than $2.5 million.
In November 2018, the county’s finance department received emails sent from what appeared to be Branch and Associates, a contracting company that was building the new West Cabarrus High School.
The emails included a request to update Branch and Associates’ bank account information. Staff were supplied with all the seemingly valid documentation and approvals required, and processed the request accordingly. The next vendor payments made by the school went straight into the scammers’ account and were quickly funneled through a string of other accounts.
The bank was able to freeze and recover $776,518 of the $2,504,601 payment, leaving the county to pay the remaining balance of more than $1.7 million to the real Branch and Associates.
3. Toyota Boshoku Corporation
In August, the European subsidiary of Toyota Boshoku Corporation, a major supplier for Japanese car manufacturer Toyota, fell for a costly BEC scam.
Attackers persuaded an employee with financial authority to update the account information on a wire payment transfer, which ultimately resulted in the company transferring more than $37 million directly into the hands of the criminals.
After learning it was the victim of fraud, Toyota Boshoku quickly assembled a team to try and recover the money. The company noted that it may have to amend its March 2020 earnings forecast if it is unable to recover the lost funds.
How to prevent business email compromise attacks
A layered approach that includes multiple checks and controls is the best way of avoiding a BEC scam. There are three main components to focus on: staff training, company policy and email authentication technology.
Training
A company’s employees are the first and most important line of defense against BEC attacks. Training staff to recognize the signs of a scam can go a long way toward reducing the risk of compromise and preventing fraud.
While BEC attacks tend to focus on the C-suite and other higher-ups with financial authority, the initial point of entry can happen at any level of a company. As such, it’s important that staff receive regular training on how to identify and respond to BEC attacks.
Prevent attackers from gaining initial access to a corporate email account
To carry out a BEC scam, attackers first need to gain access to a company email account. Preventing this initial point of compromise is critical for stopping BEC attacks.
Here are some common ways attackers use emails to gain access to corporate email accounts:
Domain name spoofing
Commonly used in BEC attacks and other phishing scams, domain name spoofing involves forging the sender’s address so that it appears an email has been sent by someone else. This is surprisingly easy to do, and only requires a working SMTP server and certain mailing software. The attacker may use domain name spoofing to convince an employee to divulge their email login credentials in order to gain access to their email account.
To check for domain name spoofing, view the source code of the email and locate the “reply-to” field. If the reply-to address is different from the sender’s address, the email may be a BEC or phishing scam.
Display name spoofing
Attackers commonly use display name spoofing to impersonate someone within the target company. This can be accomplished by simply registering a free email account and changing the display name to the same name as a trusted business contact, such as a high ranking executive. The attacker hopes that the recipient will look at the display name without checking the email address, and will consequently perform the request, engage in dialogue or open a malicious attachment.
Display name spoofing is immune to verification technologies such as DMARC, DKIM, and SPF (more on those later). The simple solution here is to encourage staff to check the sender’s email address and not rely solely on the display name.
Phishing attacks
Attackers will often use traditional phishing techniques to gain initial access to an email account. As such, staff should be vigilant of emails that create a sense of urgency. Phishing emails are usually worded in a way that hits certain psychological triggers and compels the recipient to take immediate action. According to Security Awareness Training company KnowBe4, the most-clicked phishing general email subject lines in Q2 2019 were:
- Password Check Required Immediately
- De-activation of [[email]] in Process
- Urgent press release to all employees
- You Have A New Voicemail
- Back Up Your Emails
How to recognize when an attacker has gained access to a corporate email account
While the above steps can help reduce the risk of an account being compromised, there’s no preventative system that is 100 percent secure. Consequently, employees should remain cautious and always be on the lookout for indicators of a potential scam.
Here are some of the most common signs of a BEC attack:
Out-of-character emails from senior management
Scammers often impersonate people in positions of power to gain psychological leverage over their victims. Encourage employees to be mindful of who they’re receiving emails from and consider whether or not the communication is out of the ordinary.
For instance, employees should be very suspicious if the CEO requests an urgent transaction that bypasses the usual procedures, or the CFO demands access to a restricted part of the network.
Spelling and grammatical errors
Emails laden with spelling and grammatical errors should also raise some red flags. While attackers do spend a lot of time learning the communication habits of their target, they’re still prone to making mistakes. Of course, a typo isn’t necessarily proof of a BEC scam, but it should be cause for suspicion – particularly if the message is regarding an important request.
Requests to bypass policies
Most organizations have strict procedures in place when it comes to payments or requests for sensitive information. Employees should be very wary of any emails that ask them to bypass company policies, regardless of the sender’s position in the organization.
Review processes
BEC scams prey on natural human flaws. Implementing robust communication policies with multiple checks and controls can help fortify these flaws and protect organizations from attacks.
Staff across every level of an organization – particularly executives, HR and those in the finance department – should know and adhere to clearly defined processes for handling financial transactions and important email requests.
Below are a few security processes organizations should consider:
Enable 2FA on email accounts
Two-factor authentication (2FA) requires the user to input a secondary piece of information (such as a dynamic verification code) in addition to the user’s login credentials. Securing work email accounts with 2FA reduces the risk of an attacker gaining unauthorized access to an employee’s email account, which is critical for preventing ensuing BEC scams.
While 2FA is not a perfect solution (there have been cases of attackers intercepting verification codes via phone number spoofing, malware and social engineering), it can be very useful for preventing low-effort BEC scams.
Minimize financial authorization
The more people who have authority to process wire transfers, the more potential targets there are within the organization and the higher the chances of someone inadvertently sending funds to the scammers.
As such, companies should minimize the number of employees who are authorized to process wire transfers and ensure authorized staff understand and adhere to company processes and can reliably identify the signs of a BEC attack.
Verify requests for payments
Organizations should implement a two-step verification process for all wire transfer requests. Additional validation controls (such as requiring a second person to authorize transfers) can be enforced for large payments that exceed a certain threshold.
Given that BEC attacks typically involve the use of hacked email accounts, the verification process should involve another form of communication such as a phone call.
Ideally, these communication channels should be established early in the relationship and arranged outside the email environment to minimize the chances of compromise or interception.
Verify requests for different payment processes
Many BEC attacks involve persuading an employee to replace an existing vendor’s account information with the attacker’s account. With this in mind, organizations should seek telephone confirmation for all requests to update payment information using a verified contact number that has been provided earlier in the relationship. Telephone numbers contained in the request may be spoofed and should not be used for verification.
Technology
There are a number of authentication mechanisms that can be used to verify the authenticity of an email. Using a combination of these mechanisms offers the best protection against BEC scams.
Sender Policy Framework
Sender Policy Framework (SPF) is an email authentication standard that can be used to detect forged sender addresses during email delivery. Designed to supplement SMTP (a communication protocol for electronic mail transmission), SPF is an important layer in preventing BEC scams and phishing attacks.
SPF allows the owner of a domain to specify which servers can send emails on its behalf. It enables the receiving mail server to check during delivery that the incoming email originated from a domain that was authorized by that domain’s administrator. If the email is sent from a non-authorized server, the receiving server considers the message fraudulent and can step in to prevent delivery.
However, it’s important to note that SPF has some significant limitations, which make it far from a perfect solution for BEC scams. This is due to the way SPF validates the sender.
Emails come with two FROM addresses:
- Envelope FROM: The address where the email originated and to which error notifications are sent.
- Header FROM: The email address used by the email client to populate the FROM Field.
SPF was primarily designed to protect the envelope sender. As a result, it cannot validate header FROM addresses, which are commonly spoofed in BEC scams as they are more visible to email recipients during attacks.
Please see this Wikipedia page for more information on implementation and SPF best practices.
DomainKeys Identified Mail
DomainKeys Identified Mail (DKIM) provides another form of email authentication. Similar to SPF, DKIM allows the recipient of an email to verify that an email was sent and authorized by the owner of that domain. DKIM accomplishes this by attaching a digital signature to outgoing emails.
The recipient’s system can determine if an email has been signed with a valid DKIM signature, which signifies that the email is probably legitimate. On the other hand, the absence of a valid DKIM signature signifies that the email may be forged.
Contrary to SPF, DKIM signatures do not validate the message envelope (including the envelope FROM address), which means it can’t protect against misaddressing attacks. Instead, it focuses on authenticating the address in the header, which is more commonly used in BEC and phishing scams.
Domain-based Message Authentication Reporting and Conformance
Domain-based Message Authentication Reporting and Conformance (DMARC) is one of the most effective mechanisms for combating BEC scams and phishing attacks.
The email security protocol extends the capabilities of SPF and DKIM, and enables domain owners to specify which authentication method (SPF, DKIM or both) is used when sending emails from that domain. Domain owners can also choose what happens to an email message if it fails authentication (e.g. reject the email or quarantine it). In addition, DMARC can be used to generate aggregate and forensic reports, which can be useful for monitoring email traffic and identifying potential security risks.
Despite the benefits of DMARC, the majority of organizations have failed to implement it. According to figures from email security and analytics firm 250ok, almost 8 in 10 (79.7 percent) companies in 2019 did not use DMARC.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialSummary
BEC attacks are one of the biggest cybersecurity risks facing organizations today. Due to the low-tech nature of BEC scams, mitigation isn’t so much about state-of-the-art protection technology as it is about fostering a proactive attitude toward security. Training staff to be vigilant, implementing policies and procedures for wire transfer payments and enabling email authentication mechanisms can help companies of any size reduce the risk of becoming a victim of a BEC scam.