Caution! Ryuk Ransomware decryptor damages larger files, even if you pay

Ryuk has plagued the public and private sectors alike over the past years, generating hundreds of millions of ransom revenues for the criminals behind it. Usually deployed via an existing malware infection within a target’s network, Ryuk wreaks havoc on any system that can be accessed, encrypting data using a combination of RSA and AES.
Just because Ryuk has been hugely successful, doesn’t mean its creators stopped evolving and improving it, however. So it comes to no surprise that we have seen multiple new features added to Ryuk over the past year.
One of these features that isn’t well documented is its capability to partially encrypt files. Essentially, whenever Ryuk encounters a file that is larger than 57,000,000 bytes (or 54.4 megabytes) it will only encrypt certain parts of it in order to save time and allow it to work its way through the data as quickly as possible before anyone notices.
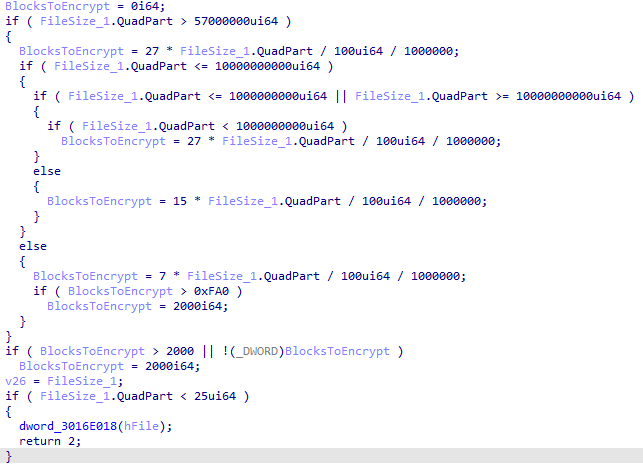
The code used by Ryuk to determine how much of a file to encrypt if the file exceeds a size limit of 57,000,000 bytes
Files that are only partially encrypted will show a slightly different-than-normal footer at the end of the file, where Hermes usually stores the RSA-encrypted AES key that was used to encrypt the file’s content. In addition to the HERMES files marker used by Ryuk, you will also find a clearly visible counter of how many 1,000,000 bytes blocks have been encrypted for this file. If that indicator is missing, the whole file is considered to be encrypted.
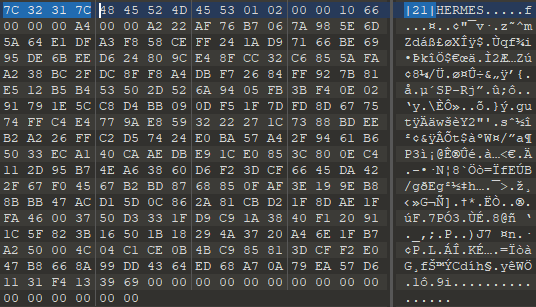
The extended version of the Ryuk file footer highlighting the number of encrypted blocks for partially encrypted files
In one of the latest versions of Ryuk, changes were made to the way the length of the footer is calculated. As a result, the decryptor provided by the Ryuk authors will truncate files, cutting off one too many bytes in the process of decrypting the file. Depending on the exact file type, this may or may not cause major issues. In the best-case scenario, the byte that was cut off by the buggy decryptor was unused and just some slack space at the end created by aligning the file towards certain file size boundaries. However, a lot of virtual disk type files like VHD/VHDX as well as a lot of database files like Oracle database files will store important information in that last byte and files damaged this way will fail to load properly after they are decrypted.
One of the services we provide at Emsisoft is to help ransomware victims who paid the ransom to recover their files even if the ransomware authors left them hanging by either being uncooperative or providing tools that do not do the job properly, both of which are increasingly common outcomes.
So if you are a Ryuk victim that was hit within the last two weeks and have files which will not load, please contact us so we can provide you with a properly working decryptor. Please understand that this will only work if you still have copies or backups of your encrypted data, as the Ryuk decryptor will usually delete files it thinks were decrypted properly. Similarly, if you’ve paid for a decryptor but have yet to use it, either back up your files before running it or get in touch with us instead. Our tool will enable you to safely recover your data whereas the tool supplied by the bad actors will not.
Note our decryption tool does not remove the need for ransoms to be paid; it is simply a replacement for the criminal-supplied tool.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialA final word of advice: prior to running any ransomware decryptor – whether it was supplied by a bad actor or by a security company – be sure to back up the encrypted data first. Should the tool not work as expected, you’ll be able to try again.


