Ransomware statistics for 2020: Q2 report
In Q2 2020, we saw the continued trend of ransomware groups exfiltrating data prior to encryption and using the stolen data as additional leverage to extort victims. Throughout the quarter, dozens of non-paying victims had their data published on leak sites or sold off to the highest bidder. There is now a greater than one in ten chance of data being stolen in a ransomware attack.
COVID-19 remained an influential force in the Q2 threat landscape and helped cement remote desktop protocol (RDP) as the attack vector of choice for ransomware operators. Many organizations evidently failed to securely implement RDP in their rush to roll out work from home arrangements, leaving RDP connections vulnerable to compromise.
Despite the promises made by some threat actors during Q1 to avoid targeting the healthcare sector, a number of healthcare organizations fell to ransomware in Q2. In the U.S. alone, at least 12 hospitals and other healthcare providers were impacted by ransomware this quarter, as discussed in our U.S.-specific ransomware report.
We also observed some rare cooperation between ransomware groups, with Maze teaming up with LockBit and Ragnar Locker to share intelligence and use of data leak platforms. Whether this was a one-off display of teamwork or the dawn of a new generation of cybercrime cartels remains to be seen.
The following statistics are based on ransomware submissions made to Emsisoft and ID Ransomware between April 1 and June 30, 2020. Created by Emsisoft Security Researcher Michael Gillespie, ID Ransomware is a service that enables organizations and individuals to identify which ransomware strain has encrypted their files.
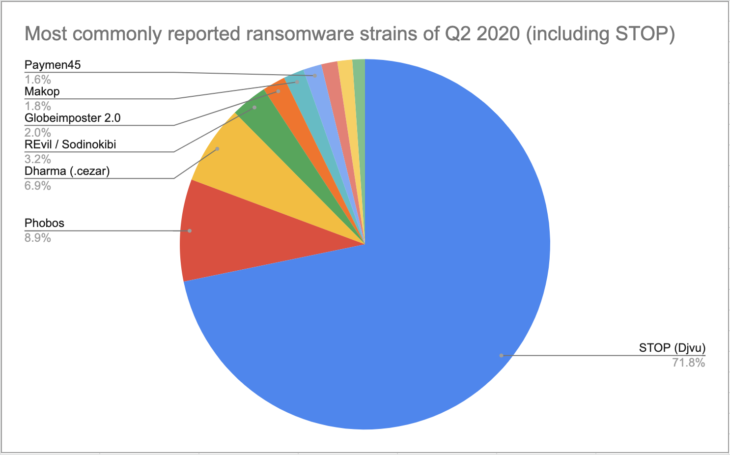
Most commonly reported ransomware strains of Q2 2020
The following chart shows the 10 most commonly reported strains of Q2. A ransomware family known as STOP/Djvu was by far the most common strain, accounting for 71.7% of all submissions.
- STOP (Djvu): 71.70%
- Phobos: 8.90%
- Dharma (.cezar): 6.90%
- REvil / Sodinokibi: 3.20%
- Globeimposter 2.0: 2.00%
- Makop: 1.80%
- Paymen45: 1.60%
- LockBit: 1.40%
- GoGoogle: 1.30%
- Magniber: 1.10%
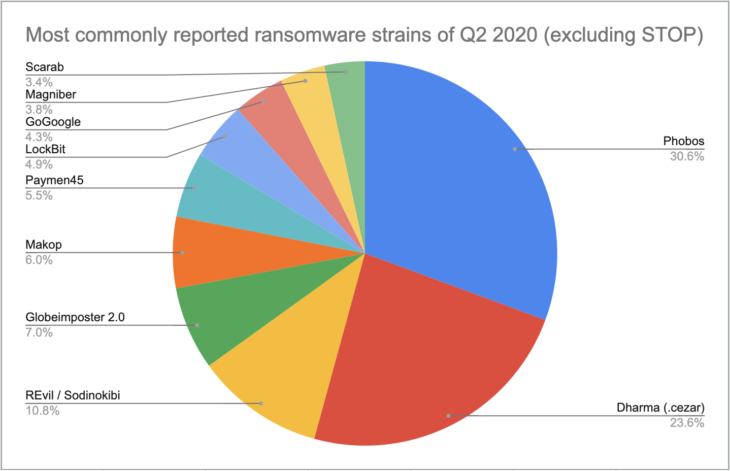
Most commonly reported ransomware strains of Q2 2020
The following chart shows the 10 most commonly reported strains of Q2 with STOP submissions excluded.
- Phobos: 30.60%
- Dharma (.cezar): 23.60%
- REvil / Sodinokibi: 10.80%
- Globeimposter 2.0: 7.00%
- Makop: 6.00%
- Paymen45: 5.50%
- LockBit: 4.90%
- GoGoogle: 4.30%
- Magniber: 3.80%
- Scarab: 3.40%
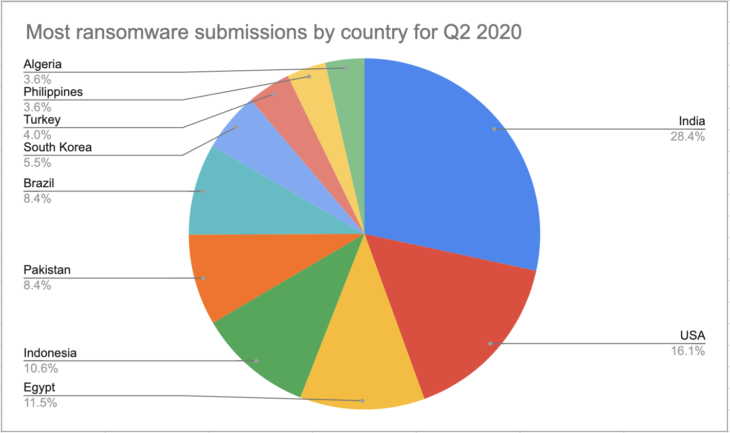
Most ransomware submissions by country
The following chart shows the 10 countries that account for the most ransomware submissions, with STOP submissions included.
- India: 28.40%
- USA: 16.10%
- Egypt: 11.50%
- Indonesia: 10.60%
- Pakistan: 8.40%
- Brazil: 8.40%
- South Korea: 5.50%
- Turkey: 4.00%
- Philippines: 3.60%
- Algeria: 3.60%
Discussion
STOP/Djvu, the most commonly reported ransomware family in Q1 2020, continued its legacy this quarter. The prolific strain, which typically spreads through cracked software, key generators and activators, accounted for 71.7% percent of all submissions in Q2, up slightly from 70.2% in Q1.
Comparing Q1 to Q2, there were a number of changes in the most commonly reported ransomware strains. Rapid, Rapid 2.0, Ryuk and Zeppelin fell out of the top 10 and were replaced by Makop, Paymen45, LockBit, and GoGoogle, while Maoloa lost its spot to Scarab in the list of the most commonly reported ransomware strains with STOP submissions excluded.
Geographically, the data shows us that ransomware is a global threat. Asian nations (including transcontinental Turkey) made up six of the top 10 countries responsible for the most ransomware submissions and accounted for more than 60% of all submissions.
India retained the number one spot, with ransomware submissions increasing from 25.8% in Q1 to 28.4% in Q2. Meanwhile, the U.S. saw the largest change of any nation, with submissions increasing from 10.2% in Q1 to 16.1% in Q2, resulting in the U.S. climbing from fourth to second position. Algeria, home to oil giant Sonatrach, which was impacted by a Maze attack in early April, was the only new entry on the list, replacing Italy.