Ransomware statistics for 2020: Q3 report
Ransomware remained a persistent threat in Q3 2020. Threat actors continued to favor post-compromise deployment, often spending significant time preparing the target environment and exfiltrating data before delivering the ransomware payload. We also saw more ransomware groups seek to weaponize stolen data, with threat actors such as Avaddon, Conti, DarkSide, SunCrypt and LockBit, among others, launching new data leak sites this quarter.
Q3 marked the start of the new school year. Some attackers used this as an opportunity to deploy ransomware on school systems that may have been compromised days or even weeks prior. It’s likely that threat actors may have waited for students to return to school before encrypting files in order to increase the impact of an attack and put additional pressure on school districts to resolve the incident and pay the ransom. This may explain why some schools (such as Hartford Public Schools) were hit on the first day back. The heightened risk of online learning may have also contributed to ransomware incidents this quarter.
The Maze ransomware group in particular was a constant threat to educational institutions, infecting Clark County School District and Fairfax County Public Schools, two of the biggest school districts in the United States, which collectively serve more than 500,000 students. In both incidents, attackers exfiltrated sensitive information and published it on their leak site after the districts refused to pay the ransom.
In Q3, we saw what may be the first ransomware-related fatality. In September 2020, attackers infected 30 servers at University Hospital Düsseldorf with ransomware, which forced the German hospital to turn away emergency patients. One of these patients, a woman in life-threatening condition, was sent to another hospital 20 miles away and tragically died as a result of treatment delays. This was the first death directly linked to a ransomware attack. Sadly, it’s unlikely to be the last.
The following statistics are based on 120,368 ransomware submissions made to Emsisoft and ID Ransomware between July 1 and September 30, 2020. Created by Emsisoft Security Researcher Michael Gillespie, ID Ransomware is a service that enables organizations and individuals to identify which ransomware strain has encrypted their files and provides a free decryptor should one be available.
Most commonly reported ransomware strains of Q3 2020
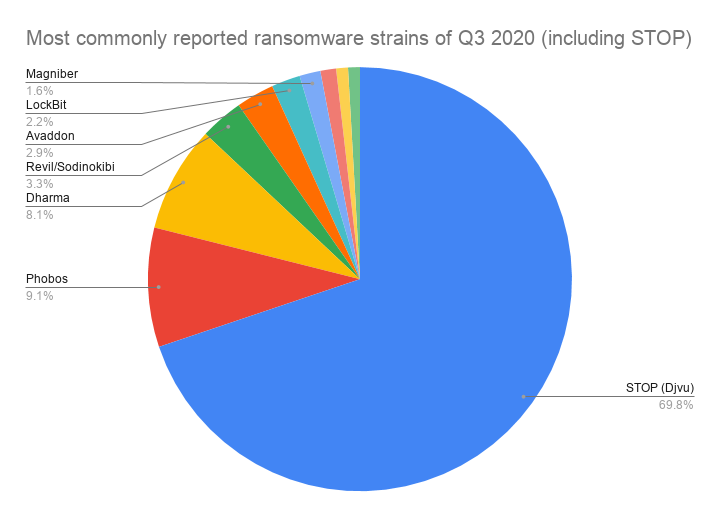
The following chart shows the 10 most commonly reported strains of Q3. A ransomware family known as STOP/Djvu was by far the most common strain, accounting for 69.9 % of all submissions.
- STOP (Djvu): 69.90%
- Phobos: 9.10%
- Dharma: 8.10%
- Revil / Sodinokibi: 3.30%
- Avaddon: 2.90%
- LockBit: 2.20%
- Magniber: 1.60%
- Makop: 1.20%
- GlobeImposter 2.0: 0.90%
- Cryakl: 0.90%
Most commonly reported ransomware strains of Q3 2020 (STOP excluded)
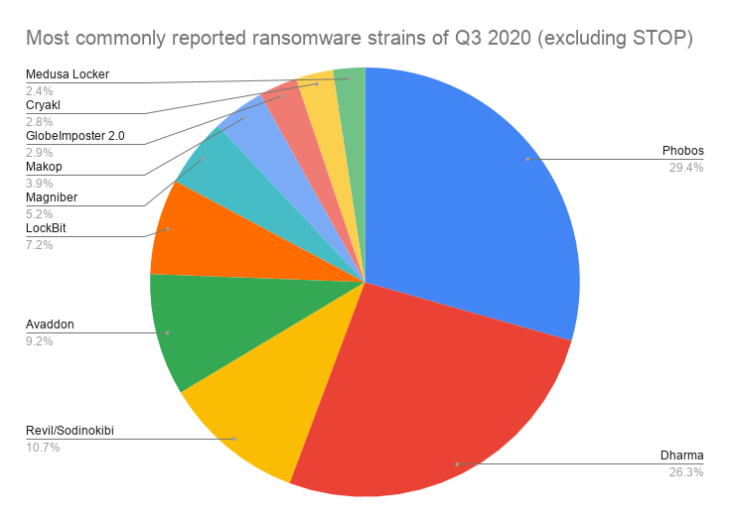
The following chart shows the 10 most commonly reported strains of Q3 with STOP submissions excluded.
- Phobos: 29.40%
- Dharma: 26.30%
- Revil / Sodinokibi: 10.70%
- Avaddon: 9.20%
- LockBit: 7.20%
- Magniber: 5.20%
- Makop: 3.90%
- GlobeImposter 2.0: 2.90%
- Cryakl: 2.80%
- Medusa Locker: 2.40%
Most ransomware submissions by country
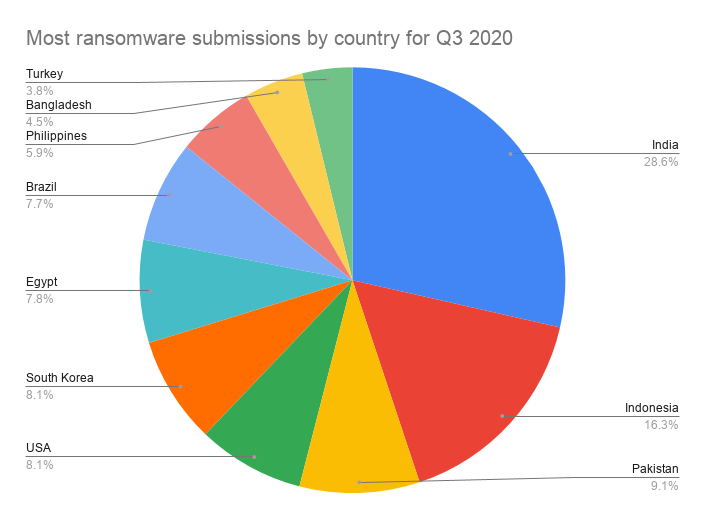
The following chart shows the 10 countries that accounted for the most ransomware submissions, with STOP submissions included.
- India: 28.50%
- Indonesia: 16.30%
- Pakistan: 9.10%
- USA: 8.10%
- South Korea: 8.10%
- Egypt: 7.80%
- Brazil: 7.70%
- Philippines: 5.90%
- Bangladesh: 4.50%
- Turkey: 3.80%
Discussion
STOP/DJVU, the most commonly reported ransomware strain in Q1 and Q2 2020, was again responsible for the most ransomware submissions this quarter. With more than 160 confirmed variants, STOP is one of the most widespread ransomware strains in existence and accounted for 69.90% of all submissions, down slightly from 71.7% in Q2.
When we compare Q2 to Q3, we can observe some changes in the most commonly reported ransomware strains. Payment45 and GoGoogle fell out of the top 10 and were replaced by Avaddon and Cryakl, which entered the list at number five and number 10 respectively. There were no changes among the four most commonly reported ransomware strains (STOP, Phobos, Dharma and REvil/Sodinokibi).
In terms of geography, submissions were heavily skewed toward Asia. Asian nations accounted for more than 3 in 4 (76.2%) of all ransomware submissions in Q3, up from 60% in Q2. There was no change to the top position, with India’s submissions increasing slightly from 28.4% in Q2 to 28.5% in Q3.
In Q2, the U.S. experienced the largest change of any nation, with submissions increasing by 5.9%. This quarter, we saw a reversal of that trend, with U.S. submissions dropping from 16.1% in Q2 to 8.1% in Q3, representing a significant decrease of 8%. Bangladesh, accounting for 4.5% of submissions, was the only new entry, with Algeria dropping out of the top 10 in Q3.