Ransomware group ups pressure on victims with new extortion tactic

The Alphv ransomware group, also known as BlackCat, has come up with an innovative new strategy to put additional pressure on victims. First, to provide some background, Alphv is a rebrand of the BlackMatter operation which was itself a rebrand of Darkside, the ransomware used in the attack on Colonial Pipeline.
Ransomware gangs used to simply encrypt their targets’ systems, however, that changed in 2019 when the Maze group began to also steal a copy of the data, using the threat of releasing it online as additional leverage to extort payment. Since then, gangs have A/B tested multiple other tactics to pressure victims, including DDoS attacks, press outreach and publicizing breaches via Facebook ads. Now, Alphv has taken it a step further.
On 14th June 2022, the group released details of an attack on a hotel in which they claim 112GB of data was stolen. They also created a website that enables the hotel’s employees and guests to check whether their information was among that which was stolen.
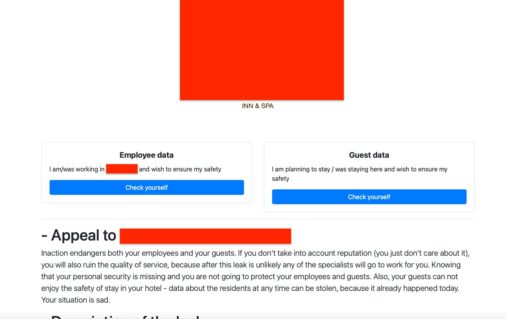
The purportedly stolen information includes names, addresses, phone numbers, email addresses and social security numbers and has been compiled into individual packs for each employee.
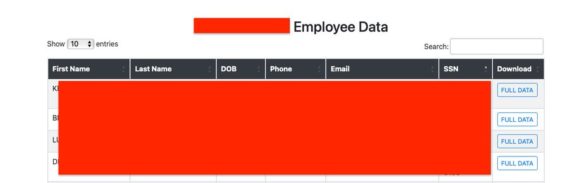
While ransomware gangs typically release information on the dark web, Alphv has created this website on the normal web, meaning it’s easily accessible by anybody – including other criminals who could potentially misuse the information for their own purposes.
Will the strategy be effective?
Alphv no doubt hope that the employees and guests will put pressure on the hotel’s management to pay the ransom so that their personal information will be removed from the website. In fact, Alphv may well have used the stolen email addresses to contact them suggesting they do exactly that.
Alphv will probably also be hoping that the tactic will increase the risk of angry employees and guests taking costly legal action against the hotel – or, at least, that the hotel and its insurers believe there will be an increased risk. Businesses typically carry out a cost-benefit analysis when deciding whether to pay a ransom demand. The greater the potential costs associated with non-payment, the more likely it is that they’ll decide to pay.
Emsisoft Enterprise Security + EDR
Robust and proven endpoint security solution for organizations of all sizes. Start free trialWhether Alphv’s strategy proves to be effective remains to be seen. If it does, the tactic will probably become more commonplace and be copied by other groups. Ransomware gangs are very predictable. If they find a particular strategy that increases their conversion rate or return on investment, they’ll repeat it over and over.


