Rogue Security Software – Evolution, Protection and Awareness
Internet has come of age, and with it malicious software and related infections. Viruses, Trojans and advertising software and popups have been there and the numbers have increased with time. With the advent of new century, especially in last 5 years, there has been an introduction to newer types of malicious software, namely spywares and rogue security software. The evolution of rogue security software is no less interesting than human evolution; from a simple windows installer based malware to the recent web exploit or even fake warnings and blue screens, the path is incredible. Today the industry is billion dollars based, and there is a new variant/rogue or more every day, and the main strategy lies in exploiting social engineering to fool users to get scared and buy/purchase their fake products to have false sense of security. Let’s go a little deeper. The rogue security industry has either big fishes those have been around for some time and just spoons out new variants every now and then, or one time malwares those come , spreads like epidemic and then suddenly vanishes. There is a strong “maybe”, that most of them are inter connected somewhere but, that’s another story. Two notable big fishes are winfixer and XPAntivirus, with Spysheriff being one of the early trouble makers.
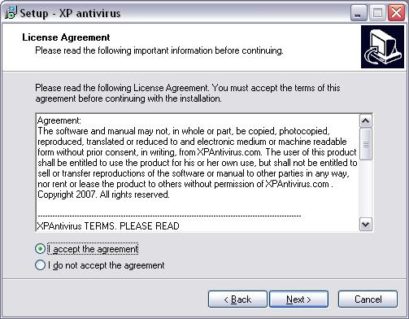
The initial ways of infection were not something that stands out.
Just like any normal setup installer, which user would manually install and the malware is in the machine and uninstaller along with it, but let’s see how this evolved with time.
The whole industry completely overhauled itself, and the change is scary. Much have been targeted towards Microsoft’s own security initiatives, namely, Security Center ( more explained below ), Windows Defender, MSRT, and even Windows Vista ( or OEM products) sales and DVD package imposters.
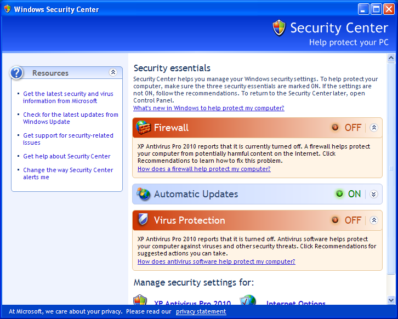
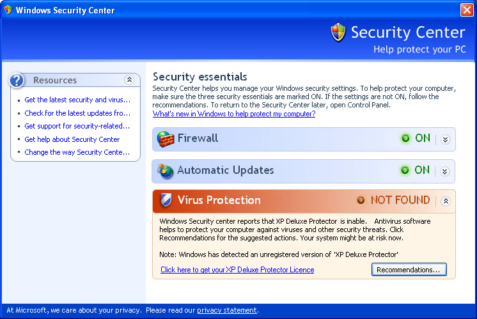
Lets look at how the rogue software started exploiting the “Security Center” of Microsoft Windows.
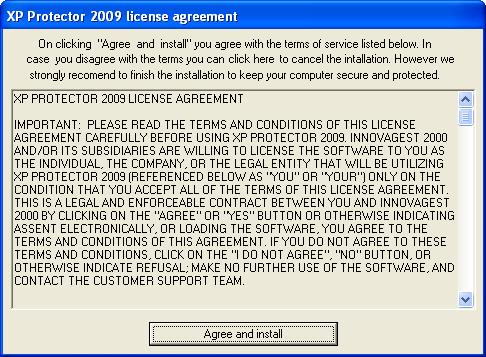
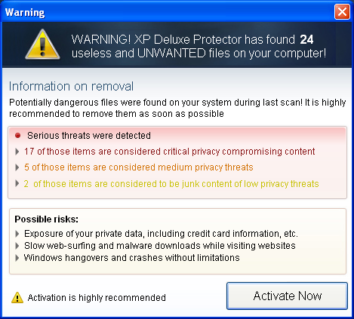
The image looks very similar and anyone using Windows, have once or more come across the same while trying to configure their Firewall or Automatic Updates options. If we look a little closer, we can see the fakeness of the products and the try to fool normal user in a make belief attempt. One very common characteristic, though very surprising, is the errors found in the language itself.
“Windows Security center reports that XP Deluxe Protector is inable.” There is also the lure to get the user “purchase” the fake product as we can see the same in the fake Security Centers.
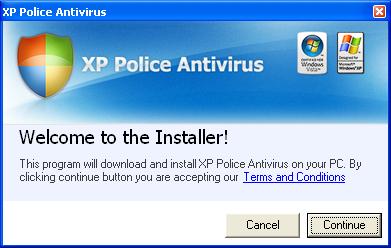
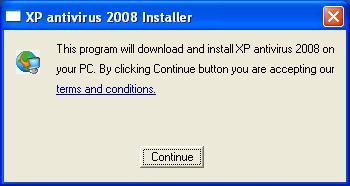
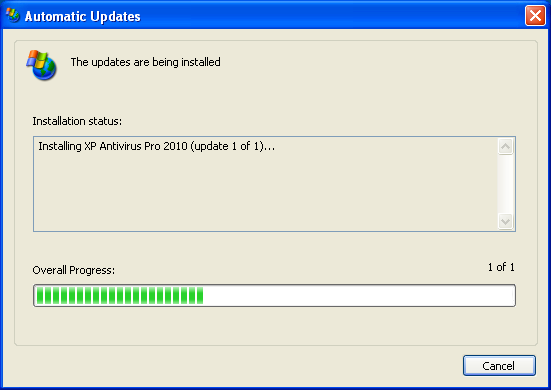
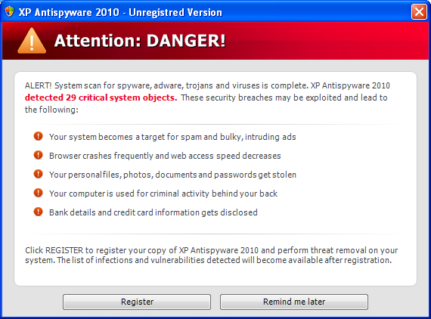
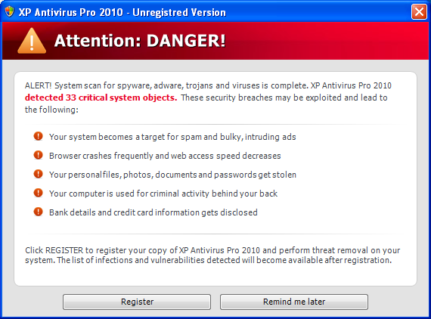
The funny thing is, the craziness of duplication did not end there. Let us look at another instance
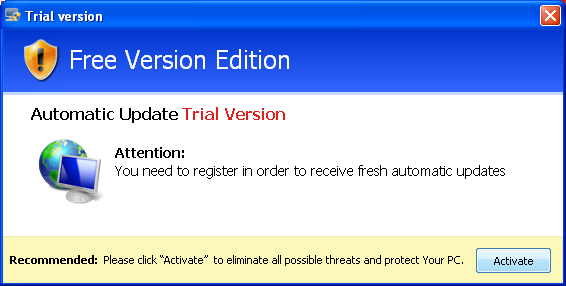
And if the user clicks the same, they will again be redirected to either the product download or registration page, which again have been manufactured in a way to fool the user
It is amazing how we as end user get manipulated so easily , that this industry which is completely based on tricking user to buy a “fake” security product so that they can feel they are protected from warnings such as below!
In the above images, two looks similar but different product names, thus proving similarity in coding or UI design and the other has similar strategy with different UI. It is very easy for an end user who just uses computer for email, online shopping or just browsing to get tricked by these flashy and at your face prompts, and that’s where the awareness should come into play. The creators of these fake products have tried and are always bringing out new attempts to trick users, in every possible ways and I have tried to show a few of them.
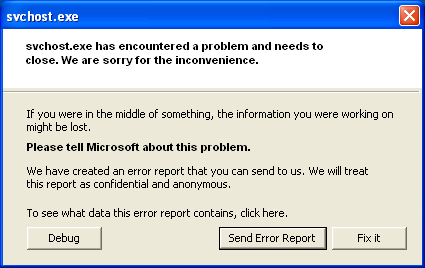
The process of infection has also evolved over time. If we take the earlier infections, it was either by harmless user install or with some third party bundlewares. The earlier versions of XPAntivirus or even SpySheriffs would have product related websites, where user would stumble upon or get redirected as part of either user consent installation or bundled installation. This changed dramatically but steadily. The malware industry is well integrated, and quite a few different malware types, like spambots, Trojan downloaders and rogue softwares serve as a complete infection chain. As recent as within a year, instances like CNN website related infections or MSNBC, malwares like cbeplay and then Trojan downloaders downloading rogue softwares at the end of infection chain. The mechanism of infection starts with vectors like exploited or hacked websites with infected codes, where user either mistakenly clicks on links or prompts which stares at their face. The other prevalent way is through a spam mail, where once user clicks, he is infected with Trojan downloader which in turn either shows balloon like warnings 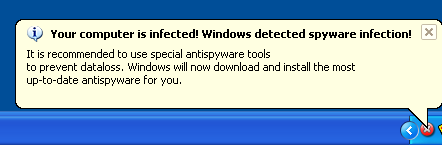 , disguised like Windows taskbar prompts or even browser prompts like
, disguised like Windows taskbar prompts or even browser prompts like 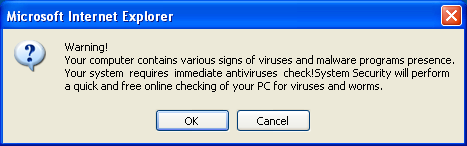 , in either case tricking user to go ahead and then download the fake malware.
, in either case tricking user to go ahead and then download the fake malware.
As I mentioned at the start of the blog, earlier there were no such lures or tricks, but as the industry grew with time and understood the huge prospect in the Security field they are now working to make full use of it. Trust is a huge factor nowadays, and very few on the web that exist have trust from a user. Let’s take another example.
This was back in 2006
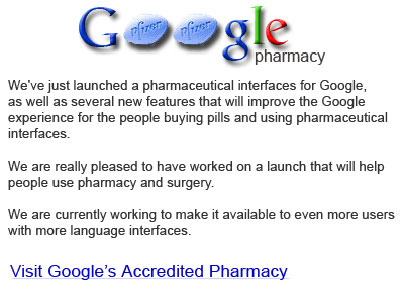 http://regmedia.co.uk/2006/06/07/google_pharmacy_site.jpg
http://regmedia.co.uk/2006/06/07/google_pharmacy_site.jpg
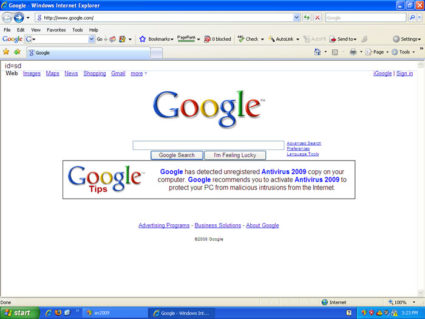
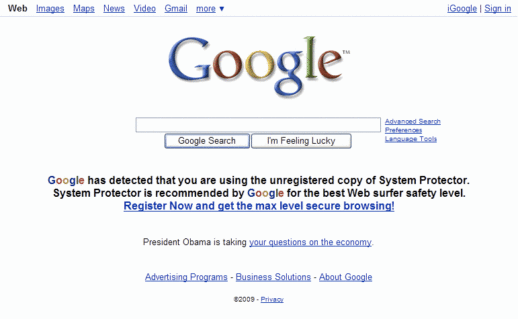
And these are recent images
Source – http://img.bleepingcomputer.com/swr-guides/a/antivirus-2009/fake-google-warning.jpg and http://www.precisesecurity.com/blogs/wp-content/uploads/2009/04/google-has-detected-page.gif
The level of tricks kept itself going with the passage of time, and ever changing for an end- user to keep up to. Let’s look at the attempts below
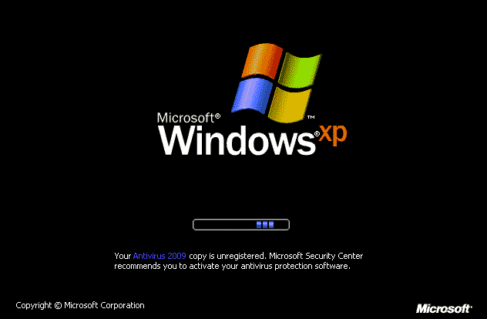
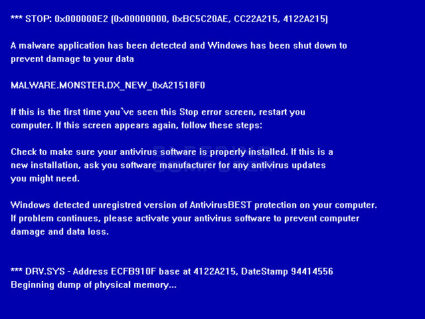
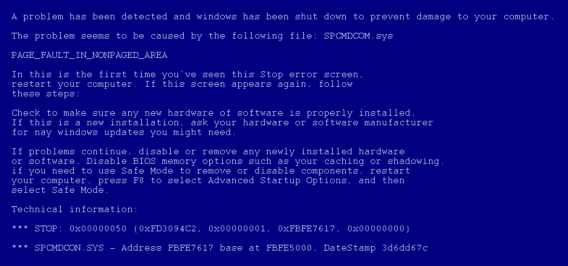
Blue Screen of Death ( Infamous BSOD) have always put Microsoft Windows user in a kind of “What the heck happened” situation, and the malware creators did not leave that area behind too. To suddenly have a restart, and even when the restart process have been made up as another Fake Advertising, or sudden Blue Screen with error messages having characteristic wrong English are supposed to put end-user in enough confusions to fall prey to these tactics. And that’s where We at Emsisoft are trying to aware you, as an end-user , about every possible tactics these malware creators are using and we will not stop. Do keep your antivirus and operating system updated, click only which you are sure about, and as always you can submit any suspicious file to us. Do visit http://www.emsisoft.com/en/support/malware/ for informations about different malwares we target.
At Emsisoft, we are continuously updating our signatures and our analysts are always on lookout for any undetected samples. Also, our behavioral based “Behavior Blocker” alerts you on a huge range of malicious related activities so that you are always aware of what is happening in your system. We make sure our customers are having a peace of mind and security should come naturally. It is not going to get any easier , and the industry will only get trickier, but we here at emsisoft are always a step ahead. We have the best protection and highest on detection than other security softwares, and we protect you from getting infected, and eradication of such threats. Especially with release of Version 5, we have overhauled our product in a lot of way, and we make sure our users remain protected from these threats today and tomorrow.
Have a Great (Malware-Free) Day!