Attack on Bitcoins: The virtual currency that is creating a gold-rush amongst hackers

Have you ever heard of “Bitcoins“? They are a virtual currency that has been in use since the beginning of 2009 through open-source software. Individual Bitcoins are calculated as cryptographic keys in peer-to-peer networks. This is one of their major advantages as these keys cannot be forged due to their unique characteristics.
Bitcoins are, however, similar to normal currency. The virtual coins are simply stored on a storage medium (such as a hard drive, online storage space or a USB stick) rather in a wallet. Much like any file on your hard drive, whoever has access to the storage medium, also has access to your Bitcoins – basically like a open wallet left lying around.
The entire system is free and under no control by any institution. In times of state bankruptcy and fear of inflation, it is hardly surprising that Bitcoins are booming and are a major subject in the media. Their value has been skyrocketing in recent months. On the one hand, this is due to the global economic crisis; on the other hand, it’s due to the fact that the number of Bitcoins is limited just like precious metals are.
Basically any computer can be used to generate Bitcoins. The required software is free so the only cost involved is the electricity required by your CPU and graphics card. If generating Bitcoins yourself isn’t your forte, you can exchange euros or dollars for the virtual currency on countless websites. Even some online retailers accept the new currency. This is why Bitcoins are to be taken seriously and aren’t just a pure fantasy dreamt up by idealistic individuals. You should, however, be careful and not consider it a real currency, as it is mainly an electronic collector’s item.
How do hackers get their hands on Bitcoins?
The current peak in their value has attracted cybercriminals like moths to a flame. Bitcoins promise quick money. Rogue security software and spyware is out, and Bitcoin malware is in. This is because Bitcoins can be used without revealing your identity, by sending your unique key.
 While these virtual coins can’t be forged like a bank note, they remain vulnerable to theft. Anyone with access to a computer or online storage space that contains Bitcoins, can steal them without any problems. It’s usually sufficient to have access to the person’s PC. This has happened a number of times in the past. Bitcoins worth several tens of millions of dollars have been stolen to date.
While these virtual coins can’t be forged like a bank note, they remain vulnerable to theft. Anyone with access to a computer or online storage space that contains Bitcoins, can steal them without any problems. It’s usually sufficient to have access to the person’s PC. This has happened a number of times in the past. Bitcoins worth several tens of millions of dollars have been stolen to date.
Traditional forms of theft are not the only method that hackers resort to in order to get their hands on Bitcoins. As mentioned previously, this alternative currency is calculated through complex procedures using computers. The conversion rate to conventional money, which is constantly reaching new peaks in value, is prompting more and more botnet managers to take their share. These Botmasters are now using the PCs under their control not only for DoS attacks, but also to calculate Bitcoins.
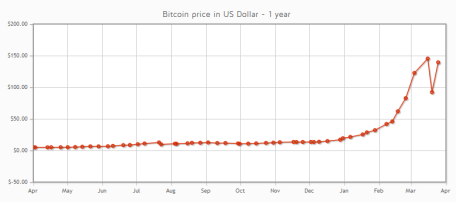
As cybercriminals continue to become increasingly sophisticated, there have been more and more sightings of specialized Bitcoin malware emerging. The most widely spread one is a variant of the trojan Fareit. First seen on Russian porn sites, Fareit either installs the Bitcoin miner “CG Miner” or uses the PC to verify transactions. The more computers that are infected, the faster the attacker receives new Bitcoins. This is highly profitable, as larger networks generate no less than 25 Bitcoins in about 10 minutes. One Bitcoin is currently (end of April 2013) worth about 140 USD. By comparison, at the end of 2012 it was worth slightly more than 14 USD.
Growth in Bitcoin value during the last 12 months, source: bitcoin.de
How to protect yourself against Bitcoin malware
Basically, the same rules of thumb apply here as they do for protection against classical trojans and common identity theft. You should ensure that your software is always up-to-date, and that you are using secure passwords. A secure password consists of at least eight characters and contains a number, an uppercase letter and a special character, such as “ApL47bAk!”. More important hints can be found in this article.
Important: Careful surfing by avoiding dubious websites is simply not adequate protection. New vulnerabilities are constantly being discovered, ensuring that malware can infect unprotected computers without the user even noticing. Use of software with efficient real-time protection is the key.
Emsisoft Anti-Malware, for instance, uses three efficient protection mechanisms at once: Surf protection to block dangerous websites, a dual-engine signature scanner with a detection rate of more than 99.x% and a state-of-the-art behavior blocker that detects even unknown malware reliably. Further information on how our award-winning software works, can be found here: The three layers of Emsisoft Anti-Malware and how they work.
Have a nice (malware-free) day!
Your Emsisoft Team