Petya ransomware analysis: How the attack unfolded

From the ashes of WannaCry has emerged a new threat: Petya (or sometimes called NotPetya). Originating in Eastern Europe on June 27, Petya ransomware quickly infected a number of major organizations in Ukraine and Russia before spreading farther afield. Companies in South America, the US and Asia all reported large-scale disruption caused by Petya.
What makes the outbreak all the more perplexing is the fact that the current iteration of Petya uses the exact same NSA exploit used by WannaCry – a vulnerability that is easily resolved by following the advice of IT security experts and downloading the latest security patches from Microsoft. However, given Petya’s impact and its relatively large infection rate, it seems as though many businesses did not take initiative and were consequently left unprepared and vulnerable to attack.
While we can totally empathize with the victims of Petya, we also want to use the attack as something of a cautionary tale. In this article, we’re going to show you a play-by-play petya ransomware analysis of how it unfolded, the effect Petya had on the organizations it infected and what you can do to keep your computer safe.
Recap: What is Petya ransomware?
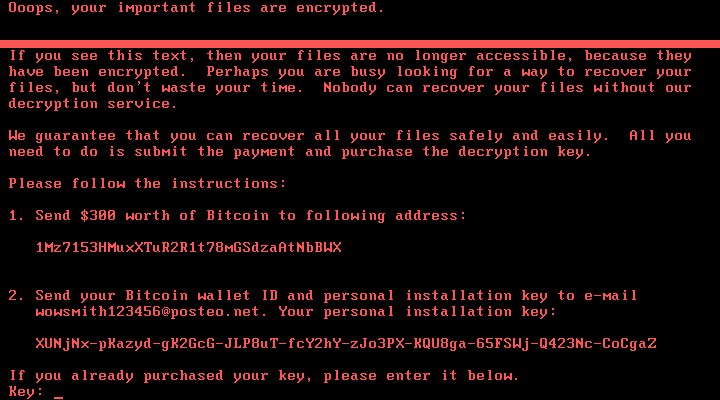
Petya is fairly unique as far as ransomware goes. Modeled after existing Petya ransomware that was circulating in March 2016, the current variant installs its own custom operating system and encrypts file system structures during the boot process, effectively locking users out of their computers.
After infecting a system disguised as a CHKDSK verification process, Petya displays a ransom screen demanding users pay $300 worth of bitcoin to decrypt files and restore access to the machine. It spreads in much the same way as WannaCry, exploiting internet-connected systems that have the SMBv1 protocol enabled and have not been patched by the MS17-010 fix.
You can get further insight into Petya’s encryption methods in our blog covering the initial outbreak.
What was the purpose of Petya ransomware?
Our understanding of the intent behind the Petya attack has evolved since the initial outbreak. From the outset, it seemed as though the ransomware was designed simply to net the cybercriminals as much money as possible.
However, closer analysis suggests that the financial aspect was probably little more than a diversion. A simplistic, traceable bitcoin payment system and a vulnerable communication channel (a regular email address that was quickly taken offline by the email provider) meant that collecting ransom money was never going to be sustainable, indicating that long-term profit was an unlikely objective.
Our hypothesis turned out to be correct; when all was said and done, less than four bitcoins (about $10,000) were paid into the bitcoin wallet connected to the Petya attack. In contrast, the cybercriminals behind WannaCry received ransom payments totaling more than 51 bitcoin (over $130,000), while the infamous CryptoLocker of 2013/14 extorted more than $3 million from victims.
So, if Petya’s primary objective wasn’t to make money, what was it designed to do? Along with many other IT experts, we believe that Petya is actually destructive malware disguised as ransomware. This enabled cybercriminals to create widespread disruption in targeted organizations – primarily the Ukrainian government, in this instance – under the guise of collecting ransom money.
How did the Petya ransomware attack start?
It’s thought the Petya ransomware attack originated at M.E.Doc, a Ukrainian company that makes accounting software. A variety of sources, including Microsoft and the Ukrainian Police, reported that M.E.Doc’s software was infected with Petya during a software update. When M.E.Doc clients downloaded the update, they inadvertently received the ransomware, which then quickly spread to other organizations mostly concentrated in Ukraine and Russia.
“It seems like mostly Ukraine and Russia were hit,” explained Emsisoft Ransomware Analyst Sarah.
“Interestingly enough, Ukraine has been targeted by a large number of ransomware the last few months.”
On June 27, M.E.Doc posted a message all but confirming their involvement in the outbreak:
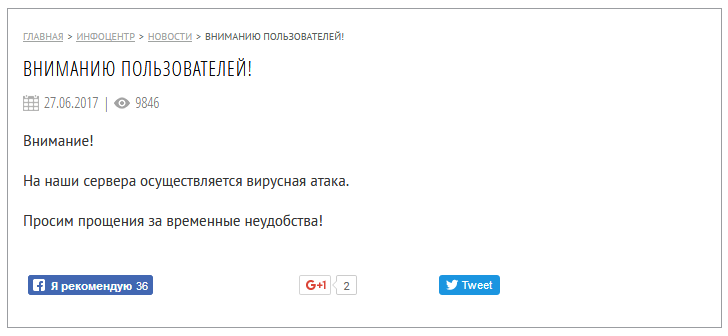
“Attention!
Our servers are carrying out a virus attack.
We apologize for the temporary inconvenience!”
(Translated)
However, the post was later withdrawn and the company went onto deny that its servers were in any way responsible for the spread of Petya. Interestingly, this is not the first time M.E.Doc has been embroiled in a malware incident. In May of this year, the organization’s servers were reportedly found to be carrying the XData ransomware, which burned a trail of destruction across Ukraine.
Regardless of M.E.Doc’s involvement, the fact remains that Petya spread quickly over the day of outbreak, leading many IT specialists to predict a high level of disruption. Thankfully, these predictions turned out to be inaccurate, with infections quickly leveling off within 24 hours – but not before infecting as many as 2,000 systems globally…
Which organizations were affected by the Petya cyber attack?

- Ukrainian government, banks, Chernobyl nuclear plant
As noted, Ukraine was hit hardest by Petya. Banks, airports, aircraft manufacturers and a number of government departments were all brought to a standstill by the ransomware as IT security teams fought to minimize disruption and restore system access.
“As a result of these cyber attacks these banks are having difficulties with client services and carrying out banking operations,” commented Ukraine’s central bank, as quoted by The New York Times.
Computers at the Chernobyl nuclear plant were also shut down after staff found evidence of the ransomware on the network, though Shift Director Vladimir Ilchuk was quick to add that there was no threat of a radiation leak.
- Rosneft (Russia)
Servers at Rosneft, Russia’s largest oil producer, were compromised and the company’s website was brought offline. By moving to a reserve production system, the organization was able to resume oil production with minimal disruption.
- Cadbury (Australia)
Although Petya infections were mostly centered on Eastern Europe, the ransomware did manage to make its way farther south. On the night of June 27, the Cadbury chocolate factory in Hobart, Australia, was forced to shut down operations after workers found themselves locked out of their computers and staring at Petya’s ransom screen.
Ransomware attack comes to Tasmania. This is what Cadbury's Hobart computers look like since 9:30pm #ransomware pic.twitter.com/tZIC16oQNH
— Leon Compton (@LeonCompton) June 27, 2017
- Maersk (Denmark)
Danish transport and logistics giant Maersk, the largest shipping company in the world, acknowledged its computer systems had experienced widespread outages at the hands of Petya. Many facets of the organization were affected, including container shipping, oil and gas production, drilling, tug boat services and oil tanker operations.
“We can confirm that Maersk IT systems are down across multiple sites and business units due to a cyber attack,” said a Maersk spokesperson, as quoted by Fortune.
- WPP, Saint-Gobain and Merck (UK, France and US)
In the UK, British advertising firm WPP admitted its IT systems had been infected by Petya and was experiencing disruptions as a result. France also wasn’t immune from the malware, with Saint-Gobain, a company specializing in construction material, reporting that it had been attacked and was bringing its networks offline to prevent further infection. Across the Atlantic, US pharmaceutical company Merck was hit by malware, though the organization was reluctant to confirm it was Petya specifically.
What’s the latest status with Petya ransomware?
More than a week went by after the initial infection before the cybercriminals made their next move. On the evening of July 4, the bitcoin wallet linked to Petya was emptied and transferred to a different wallet.
On the same night, Motherboard discovered a post on DeepPaste and Pastebin (web applications for storing and sharing plain text) made by someone claiming to be associated with the Petya creators.
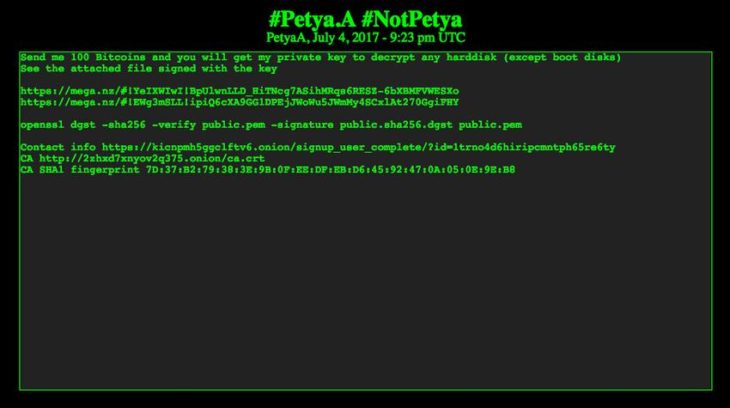
In the announcement, the authors offered to release the private encryption key used in the attack in exchange for the princely sum of 100 bitcoins, or $233,000 at the time of writing. The encryption key would supposedly decrypt all computers affected by Petya. Interestingly, there was no bitcoin address included in the announcement; instead, the author included a link to a dark web chatroom where they could be contacted.
With the help of security researchers, Motherboard was subsequently able to confirm that the message indeed came from the authors, as they were able to successfully decrypted a test file. This latest move is clearly financially motivated, adding another layer of confusion to the mystery surrounding Petya and keeping us guessing as to whether profit or destruction was the creator’s true objective all along.
So, what can we learn from Petya ransomware?
Firstly, Petya’s success draws attention to the fact that many organizations are still taking a lax approach to ransomware – despite having access to tools specifically designed to combat this type of malware. From nuclear power plants to chocolate factories and everything in between, evidently many companies and government bodies did not heed the expert advice or download the security patches that emerged after WannaCry.
Key takeaway: Be proactive! Make regular backups, keep your operating system and software updated, and listen to the recommendations of IT security specialists.
Secondly, Petya also taught us that ransomware can inflict extensive collateral damage on innocent bystanders. Although Ukraine may have been Petya’s intended target, the ransomware quickly infected organizations far outside the initial line of fire and created havoc across Europe, the US and Australia.
Key takeaway: You can still get hit by ransomware, even if you’re not directly in the firing zone. So ensure that you have a reputable anti-malware solution installed with a reputation for blocking ransomware.
Here at Emsisoft, we’re dedicated to developing comprehensive IT security solutions that protect you, your family and your business against all forms of ransomware. Unlike just about every other anti-ransomware tool on the market, Emsisoft Anti-Malware is able to intercept ransomware before it encrypts your files, minimizing disruption and saving you time and money.
Emsisoft Endpoint Protection: Award-Winning Security Made Simple
Experience effortless next-gen technology. Start Free TrialHave a wonderful (malware-free!) day.



